WGU-D488 Exam Details
-
Exam Code
:WGU-D488 -
Exam Name
:WGU Cybersecurity Architecture and Engineering (D488) -
Certification
:WGU University Certifications -
Vendor
:WGU University -
Total Questions
:232 Q&As -
Last Updated
:Jan 11, 2026
WGU University WGU-D488 Online Questions & Answers
-
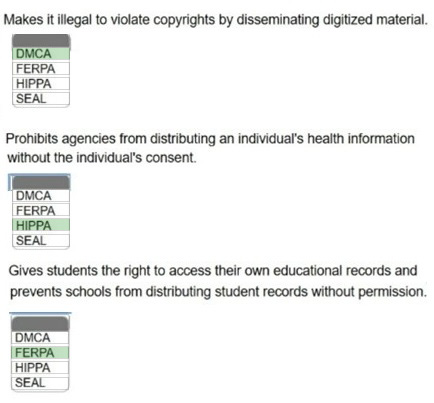
Question 1:
HOTSPOT
Match the legislative purpose with the corresponding legislation.
Answer options may be used more than once or not at all.

-
Question 2:
An engineer has noticed increased network traffic originating from an unknown IP address. Which action should be taken to analyze the unusual network traffic patterns?
A. Compare the unknown address to known IP addresses to determine if it is a threat
B. Temporarily block all incoming traffic from the unknown IP address
C. Permanently block all incoming traffic from the unknown IP address
D. Rate limit incoming traffic from the unknown IP address -
Question 3:
A retail company has recently implemented a new point of sale (POS) system that is critical to its business. Which security control is essential for protecting the availability of the POS system?
A. Implementing intrusion detection and prevention systems can help detect and prevent unauthorized access to the POS system.
B. Regularly backing up the data stored in the POS system and having a disaster recovery plan can help ensure that the system is available in the event of a security incident or system failure.
C. Enforcing strict access controls can limit the number of users with access to the POS system and prevent unauthorized access.
D. Regularly updating the POS system with the latest security patches can help prevent exploitation of known vulnerabilities and maintain the system's availability. -
Question 4:
The development team has requested permission to use several open-source libraries to build a corporate web application. Which resource can the security team recommend to ensure these libraries can be trusted?
A. Agile software development
B. Waterfall software development
C. Common Vulnerabilities and Exposures (CVE)
D. Continuous delivery -
Question 5:
A company is developing a new system to process personal information about its customers, including their names, addresses, and purchase histories.
Which term describes the process of identifying and evaluating the potential effects that the new system may have on the privacy of personal information and developing strategies to mitigate those risks?
A. Data Protection Impact Assessment (DPIA)
B. Business Continuity Planning (BCP)
C. Risk Management
D. Disaster Recovery (DR) -
Question 6:
Which risk management strategy will ensure the secure configuration and deployment of a new supply chain management system and prevent identity theft?
A. Use of a strict firewall policy to restrict access to the system's server
B. Configuration of the system to disable all universal serial bus (USB) ports on all workstations
C. Implementation of regular vulnerability scans and patch management
D. Implementation of multifactor authentication for all user accounts -
Question 7:
A company has recently implemented a hybrid cloud deployment. The security team has been notified about thousands of failed attempts to connect to routers and switches in the on-premises network. A solution must be implemented to block connections after three unsuccessful SSH attempts on any network device.
Which solution meets the requirements in this scenario?
A. Data loss prevention
B. Firewall
C. Intrusion prevention system
D. File integrity monitoring -
Question 8:
An e-commerce company has recently experienced a data breach in which the personal and financial information of its customers was stolen. The company is concerned about the potential for future data breaches. What is the most important factor to consider when evaluating the potential for future data breaches in this scenario?
A. Impact
B. Risk
C. Threat actors
D. Likelihood -
Question 9:
What is one purpose of an End User License Agreement?
A. Allow customers to legally create and sell a new version of the software
B. Allow customers to legally use the software
C. Allow customers to legally modify and compile the source code
D. Allow customers to legally distribute the application to other users -
Question 10:
What is a component of IT infrastructure?
A. Data
B. People
C. Networks
D. Printer
Related Exams:
-
WGU-C202
WGU Managing Human Capital (C202) -
WGU-D488
WGU Cybersecurity Architecture and Engineering (D488) -
WGU-IAC1
WGU Principles of Management at Western Governors University -
WGU-IBC1
WGU Organizational Behaviors and Leadership -
WGU-ITI
WGU Introduction to IT -
WGU-JY02
WGU Managing Cloud Security (JY02) -
WGU-KEO1
WGU Secure Software Design -
WGU-KVO1
WGU Web Development Applications -
WGU-MTC1
WGU Integrated Physical Sciences (MTC1) -
WGU-NSF
WGU Network and Security Foundation
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only WGU University exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your WGU-D488 exam preparations and WGU University certification application, do not hesitate to visit our Vcedump.com to find your solutions here.