Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 621:
A cybersecurity administrator needs to allow mobile BYOD devices to access network resources. As the devices are not enrolled to the domain and do not have policies applied to them, which of the following are best practices for authentication and infrastructure security? (Select TWO)
A. Create a new network for the mobile devices and block the commurycaton to the intemal network and servers
B. Use a captive portal for user authentication
C. Authenticate users using OAuth for more resiliency.
D. Implement SSO and allow communication to the intemal network.
E. Use the existing network and allow communscation to the internal network and servers
F. Use a new and updated RADIUS server to mamntain the best solution
-
Question 622:
An incident response technician collected a mobile device during an investigation. Which of the following should the technician do to maintain chain of custody?
A. Document the collection and require a sign-off when possession changes.
B. Lock the device in a safe or other secure location to prevent theft or alteration.
C. Place the device in a Faraday cage to prevent corruption of the data.
D. Record the collection in a blockchain-protected public ledger
-
Question 623:
A security engineer needs to select a primary authentication source for use with a client application. The application requires the user to log in with a username, password, and, when needed, a challenge response. Which of the following solutions BEST meets this requirement?
A. PSK
B. LDAP
C. RADIUS
D. PAP
-
Question 624:
A researcher has been analyzing large data sets for the last ten months. The researcher works with colleagues from other institutions and typically connects via SSH to retrieve additional data. Historically, this setup has worked without issue, but the researcher recently started getting the following message:
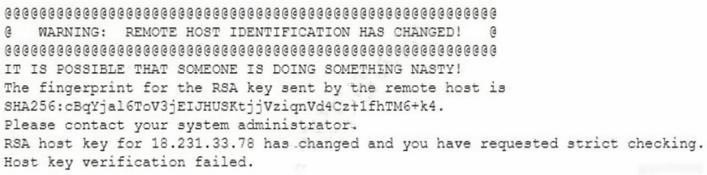
Which of the following network attacks is the researcher MOST likely experiencing?
A. MAC cloning
B. Evil twin
C. Man-in-the-middle
D. ARP poisoning
-
Question 625:
A news article states that a popular web browser deployed on all corporate PCs is vulnerable to a zero-day attack. Which of the following MOST concerns the Chief Information Security Officer about the information in the news article?
A. Insider threats have compromised this network.
B. Web browsing is not functional for the entire network.
C. Antivirus signatures are required to be updated immediately.
D. No patches are available for the web browser.
-
Question 626:
A company i working on mobile device security after a report revealed that users granted non-verified software access to corporate data. Which of the following ts the MOST effective security control to mitigate this risk?
A. Block access to application stores.
B. Implement OTA updates
C. Update the BYOD pot
D. Deploy a urttoem firmware
-
Question 627:
The IT department at a university is concerned about professors placing servers on the university network in an attempt to bypass security controls. Which of the following BEST represents this type of threat?
A. A script kiddie
B. Shadow IT
C. Hacktivism
D. White-hat
-
Question 628:
A security analyst has received an alert about being sent via email. The analyst's Chief information Security Officer (CISO) has made it clear that PII must be handle with extreme care From which of the following did the alert MOST likely originate?
A. S/MIME
B. DLP
C. IMAP
D. HIDS
-
Question 629:
A consultant is configuring a vulnerability scanner for a large, global organization in multiple countries. The consultant will be using a service account to scan systems with administrative privileges on a weekly basis, but there is a concern that hackers could gain access to account to the account and pivot through the global network. Which of the following would be BEST to help mitigate this concern?
A. Create consultant accounts for each region, each configured with push MFA notifications.
B. Create one global administrator account and enforce Kerberos authentication
C. Create different accounts for each region. limit their logon times, and alert on risky logins
D. Create a guest account for each region. remember the last ten passwords, and block password reuse
-
Question 630:
A company has decided to move its operations to the cloud. It wants to utilize technology that will prevent users from downloading company applications for personal use, restrict data that is uploaded, and have visibility into which applications are being used across the company.
Which of the following solutions will BEST meet these requirements?
A. An NGFW
B. A CASB
C. Application whitelisting
D. An NG-SWG
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.