Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 641:
An organization is concerned that is hosted web servers are not running the most updated version of the software. Which of the following would work BEST to help identify potential vulnerabilities?
A. Hping3 -s comptia, org - 80
B. Nc -1 -v comptia, org -p 80
C. nmp comptia, org -p 80 -aV
D. nslookup -port=80 comtia.org
-
Question 642:
A company provides mobile devices to its users to permit access to email and enterprise applications. The company recently started allowing users to select from several different vendors and device models. When configuring the MDM, which of the following is a key security implication of this heterogeneous device approach?
A. The most common set of MDM configurations will become the effective set of enterprise mobile security controls.
B. All devices will need to support SCEP-based enrollment; therefore, the heterogeneity of the chosen architecture may unnecessarily expose private keys to adversaries.
C. Certain devices are inherently less secure than others, so compensatory controls will be needed to address the delta between device vendors.
D. MDMs typically will not support heterogeneous deployment environments, so multiple MDMs will need to be installed and configured.
-
Question 643:
Which of the following is used to ensure that evidence is admissible in legal proceedings when it is collected and provided to the authorities?
A. Chain of custody
B. Legal hold
C. Event log
D. Artifacts
-
Question 644:
A security analyst has been tasked with finding the maximum amount of data loss that can occur before ongoing business operations would be impacted. Which of the following terms BEST defines this metric?
A. MTTR
B. RTO
C. RPO
D. MTBF
-
Question 645:
Which of the following is the FIRST environment in which proper, secure coding should be practiced?
A. Stage
B. Development
C. Production
D. Test
-
Question 646:
A user reports falling for a phishing email to an analyst. Which of the following system logs would the analyst check FIRST?
A. DNS
B. Message gateway
C. Network
D. Authentication
-
Question 647:
A security analyst is reviewing web-application logs and finds the following log:
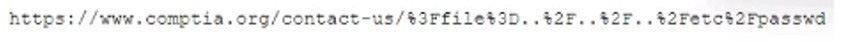
Which of the following attacks is being observed?
A. Directory traversal
B. XSS
C. CSRF
D. On-path attack
-
Question 648:
The Chief information Security Officer wants to prevent exfilitration of sensitive information from employee cell phones when using public USB power charging stations. Which of the following would be the Best solution to implement?
A. DLP
B. USB data blocker
C. USB OTG
D. Disabling USB ports
-
Question 649:
Which of the following is a risk that is specifically associated with hosting applications in the public cloud?
A. Unsecured root accounts
B. Zero--day
C. Shared tenancy
D. Insider threat
-
Question 650:
Which of the following concepts BEST describes tracking and documenting changes to software and managing access to files and systems?
A. Version control
B. Continuous monitoring
C. Stored procedures
D. Automation
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.