Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 611:
An attacker is attempting to exploit users by creating a fake website with the URL users. Which of the following social-engineering attacks does this describe?
A. Information elicitation
B. Type squatting
C. Impersonation
D. Watering-hole attack
-
Question 612:
Phishing and spear-phishing attacks have been occurring more frequently against a company's staff. Which of the following would MOST likely help mitigate this issue?
A. DNSSEC and DMARC
B. DNS query logging
C. Exact mail exchanger records in the DNS
D. The addition of DNS conditional forwarders
-
Question 613:
An engineer is configuring AAA authentication on a Cisco MDS 9000 Series Switch. The LDAP server is located under the IP 10.10.2.2. The data sent to the LDAP server should be encrypted. Which command should be used to meet these requirements?
A. Idap-server 10.10.2.2 key SSL_KEY
B. Idap-server host 10.10.2.2 key SSL_KEY
C. Idap-server 10.10.2.2 port 443
D. Idap-server host 10.10.2.2 enable-ssl
-
Question 614:
A manufacturer creates designs for very high security products that are required to be protected and controlled
A. Session replay
B. Evil twin
C. Bluejacking
D. ARP poisoning
-
Question 615:
Which of the following is a detective and deterrent control against physical intrusions?
A. Alock
B. An alarm
C. A fence
D. Asign
-
Question 616:
A security engineer obtained the following output from a threat intelligence source that recently performed an attack on the company's server:

Which of the following BEST describes this kind of attack?
A. Directory traversal
B. SQL injection
C. API
D. Request forgery
-
Question 617:
An attacker is trying to gain access by installing malware on a website that is known to be visited by the target victims. Which of the following is the attacker MOST likely attempting?
A. A spear-phishing attack
B. A watering-hole attack
C. Typo squatting
D. A phishing attack
-
Question 618:
On which of the following is the live acquisition of data for forensic analysis MOST dependent? (Choose two.)
A. Data accessibility
B. Legal hold
C. Cryptographic or hash algorithm
D. Data retention legislation
E. Value and volatility of data
F. Right-to-audit clauses
-
Question 619:
A security analyst is reviewing the following attack log output:
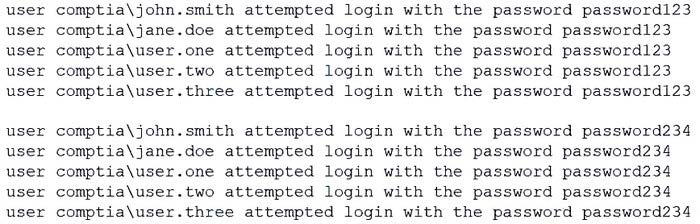
Which of the following types of attacks does this MOST likely represent?
A. Rainbow table
B. Brute-force
C. Password-spraying
D. Dictionary
-
Question 620:
A startup company is using multiple SaaS and IaaS platforms to stand up a corporate infrastructure and build out a customer-facing web application. Which of the following solutions would be BEST to provide security, manageability, and visibility into the platforms?
A. SIEM
B. DLP
C. CASB
D. SWG
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.