Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 601:
A security engineer needs to enhance MFA access to sensitive areas in a building. A key card and fingerprint scan are already in use. Which of the following would add another factor of authentication?
A. Hard token
B. Retina scan
C. SMS text
D. Keypad PIN
-
Question 602:
An analyst is working on an email incident in which target opened an attachment containing a worm. The analyst wants to implement mitigation techniques to prevent further spread. Which of the following is the BEST course of action for the analyst to take?
A. Apply a DLP solution
B. Implement network segmentation.
C. Utilize email content filtering.
D. Isolate the infected attachment.
-
Question 603:
A penetration tester successfully gained access to a company's network The investigating analyst determines malicious traffic connected through the WAP despite filtering rules being in place. Logging in to the connected switch, the analyst sees the following m the ARP table:
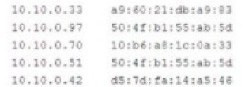
Which of the following cid the penetration tester MOST liely use?
A. ARP poisoning
B. MAC cloning
C. Man in the middle
D. Evil twin
-
Question 604:
A systems administrator is looking for a solution that will help prevent OAuth applications from being leveraged by hackers to tick users into authorizing the use of their corporate credentials.
Which of the following BEST describes this solution?
A. CASB
B. UEM
C. WAF
D. VPC
-
Question 605:
A company needs to centralize its logs to create a baseline and have visibility on its security events. Which of the following technologies will accomplish this objective?
A. Security information and event management
B. A web application firewall
C. A vulnerability scanner
D. A next-generation firewall
-
Question 606:
Which of the following refers to applications and systems that are used within an organization without consent or approval?
A. Shadow IT
B. OSINT
C. Dark web
D. Insider threats
-
Question 607:
A security analyst is using a recently released security advisory to review historical logs, looking for the specific activity that was outlined in the advisory. Which of the following is the analyst doing?
A. A packet capture
B. A user behavior analysis
C. Threat hunting
D. Credentialed vulnerability scanning
-
Question 608:
Which of the following holds staff accountable while escorting unathorized personal?
A. Locks
B. Badges
C. Cameras
D. Visitor logs
-
Question 609:
A security analyst reviews the datacenter access logs for a fingerprint scanner and notices an abundance of errors that correlate with users' reports of issues accessing the facility. Which of the following MOST likely the cause of the cause of the access issues?
A. False rejection
B. Cross-over error rate
C. Efficacy rale
D. Attestation
-
Question 610:
A company recently set up an e-commerce portal to sell its product online. The company wants to start accepting credit cards for payment, which requires compliance with a security standard. Which of the following standards must the company comply with before accepting credit cards on its e-commerce platform?
A. PCI DSS
B. ISO 22301
C. ISO 27001
D. NIST CSF
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.