Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 401:
Which of the following control Types would be BEST to use in an accounting department to reduce losses from fraudulent transactions?
A. Recovery
B. Deterrent
C. Corrective
D. Detective
-
Question 402:
An organization wants to implement a biometric system with the highest likelihood that an unauthorized user will be denied access. Which of the following should the organization use to compare biometric solutions?
A. FRR
B. Difficulty of use
C. Cost
D. FAR
E. CER
-
Question 403:
After a recent security incident, a security analyst discovered that unnecessary ports were open on a firewall policy for a web server. Which of the following firewall policies would be MOST secure for a web server?
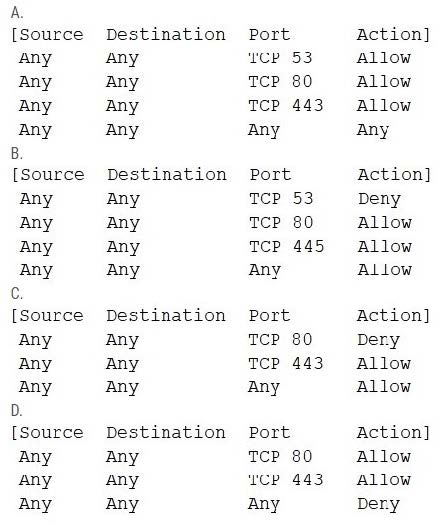
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 404:
Which of the following is the BEST example of a cost-effective physical control to enforce a USB removable media restriction policy?
A. Putting security/antitamper tape over USB ports, logging the port numbers, and regularly inspecting the ports
B. Implementing a GPO that will restrict access to authorized USB removable media and regularly verifying that it is enforced
C. Placing systems into locked key-controlled containers with no access to the USB ports
D. Installing an endpoint agent to detect connectivity of USB and removable media
-
Question 405:
A security analyst receives an alert from trie company's SIEM that anomalous activity is coming from a local source IP address of 192.168.34.26. The Chief Information Security Officer asks the analyst to block the originating source Several days later, another employee opens an internal ticket stating that vulnerability scans are no longer being performed properly. The IP address the employee provides is 192 168.3426. Which of the following describes this type of alert?
A. True positive
B. True negative
C. False positive
D. False negative
-
Question 406:
Which of the following would detect intrusions at the perimeter of an airport?
A. Signage
B. Fencing
C. Motion sensors
D. Lighting
E. Bollards
-
Question 407:
A systems administrator is troubleshooting a server's connection to an internal web server. The administrator needs to determine the correct ports to use. Which of the following tools BEST shows which ports on the web server are in a listening state?
A. ipconfig
B. ssh
C. Ping
D. Netstat
-
Question 408:
A security analyst is investigating suspicious traffic on the web server located at IP address 10.10.1.1. A search of the WAF logs reveals the following output:
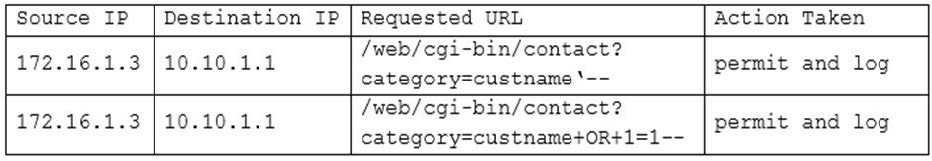
Which of the following is MOST likely occurring?
A. XSS attack
B. SQLi attack
C. Replay attack
D. XSRF attack
-
Question 409:
Which of the following explains why RTO is included in a BIA?
A. It identifies the amount of allowable downtime for an application or system,
B. It prioritizes risks so the organization can allocate resources appropriately,
C. It monetizes the loss of an asset and determines a break-even point for risk mitigation.
D. It informs the backup approach so that the organization can recover data to a known time.
-
Question 410:
Which of the following describes the continuous delivery software development methodology?
A. Waterfall
B. Spiral
C. V-shaped
D. Agile
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.