Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 421:
Which of the following typically uses a combination of human and artificial intelligence to analyze event data and take action without intervention?
A. TTP
B. OSINT
C. SOAR
D. SIEM
-
Question 422:
A user wanted to catch up on some work over the weekend but had issues logging in to the corporate network using a VPN. On Monday, the user opened a ticket for this issue but was able to log in successfully.
Which of the following BEST describes the policy that is being implemented?
A. Time-based logins
B. Geofencing
C. Network location
D. Password history
-
Question 423:
An attacker has successfully exfiltrated several non-salted password hashes from an online system. Given the logs below:
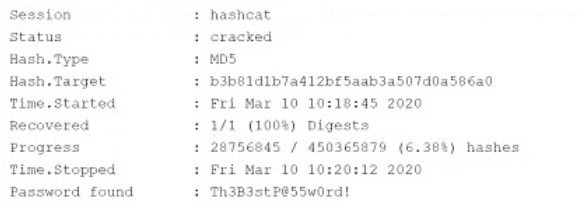
Which of the following BEST describes the type of password attack the attacker is performing?
A. Dictionary
B. Pass-the-hash
C. Brute-force
D. Password spraying
-
Question 424:
During a recent security incident at a multinational corporation a security analyst found the following logs for an account called user:
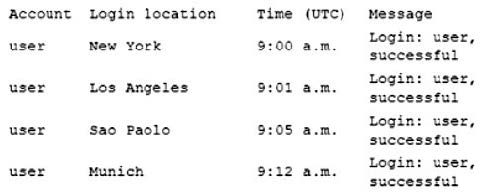
Which of the following account policies would BEST prevent attackers from logging in as user?
A. Impossible travel time
B. Geofencing
C. Time-based logins
D. Geolocation
-
Question 425:
A company wants to simplify the certificate management process. The company has a single domain with several dozen subdomains, all of which are publicly accessible on the internet. Which of the following BEST describes the type of certificate the company should implement?
A. Subject alternative name
B. Wildcard
C. Self-signed
D. Domain validation
-
Question 426:
While preparing a software Inventory report, a security analyst discovers an unauthorized program installed on most of the company's servers. The program utilizes the same code signing certificate as an application deployed to only the accounting team.
Which of the following mitigations would BEST secure the server environment?
A. Revoke the code signing certificate used by both programs.
B. Block all unapproved file hashes from installation.
C. Add the accounting application file hash to the allowed list.
D. Update the code signing certificate for the approved application.
-
Question 427:
Which of the following BEST describes when an organization utilizes a ready-to-use application from a cloud provider?
A. laaS
B. SaaS
C. Paas
D. XaaS
-
Question 428:
An organization is planning to roll out a new mobile device policy and issue each employee a new laptop, These laptops would access the users' corporate operating system remotely and allow them to use the laptops for purposes outside of their job roles.
Which of the following deployment models is being utilized?
A. MDM and application management
B. BYOO and containers
C. COPE and VDI
D. CYOD and VMs
-
Question 429:
A security manager has tasked the security operations center with locating all web servers that respond to an unsecure protocol. Which of the following commands could an analyst run to find requested servers?
A. nslookup 10.10.10.0
B. nmap -p 80 10.10.10.0/24
C. pathping 10.10.10.0 -p 80
D. no -1 -p 80
-
Question 430:
Server administrator want to configure a cloud solution so that computing memory and processor usage is maximized most efficiently acress a number of virtual servers. They also need to avoid potential denial-of-service situations caused by availiability. Which of the following should administrator configure to maximize system availability while efficiently utilizing available computing power?
A. Dynamic resource allocation
B. High availability
C. Segmentation
D. Container security
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.