Exam Details
Exam Code
:SY0-601Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1334 Q&AsLast Updated
:Jul 04, 2025
CompTIA CompTIA Certifications SY0-601 Questions & Answers
-
Question 391:
A company recently experienced a significant data loss when proprietary information was leaked to a competitor. The company took special precautions by using proper labels; however, email filter logs do not have any record of the incident. An investigation confirmed the corporate network was not breached, but documents were downloaded from an employee's COPE tablet and passed to the competitor via cloud storage. Which of the following is the BEST remediation for this data leak?
A. User training
B. CASB
C. MDM
D. DLP
-
Question 392:
A user enters a username and a password at the login screen for a web portal. A few seconds later the following message appears on the screen: Please use a combination of numbers, special characters, and letters in the password field. Which of the following concepts does this message describe?
A. Password complexity
B. Password reuse
C. Password history
D. Password age
-
Question 393:
The Chief Information Security Officer directed a risk reduction in shadow IT and created a policy requiring all unsanctioned high-risk SaaS applications to be blocked from user access.
Which of the following is the BEST security solution to reduce this risk?
A. CASB
B. VPN concentrator
C. MFA
D. VPC endpoint
-
Question 394:
A security analyst is investigating some users who are being redirected to a fake website that resembles www.comptia.org. The following output was found on the naming server of the organization:
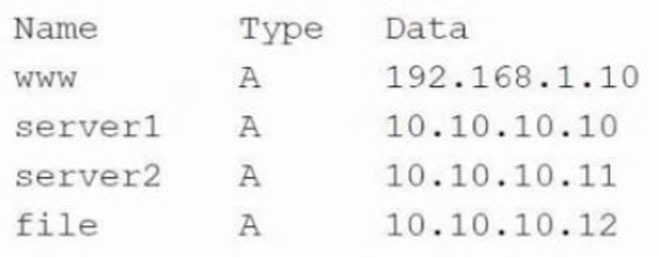
Which of the following attacks has taken place?
A. Domain reputation
B. Domain hijacking
C. Disassociation
D. DNS poisoning
-
Question 395:
A security analyst generated a file named host1.pcap and shared it with a team member who is going to use it for further incident analysis. Which of the following tools will the other team member MOST likely use to open this file?
A. Autopsy
B. Memdump
C. FTK imager
D. Wireshark
-
Question 396:
An employee received a word processing file that was delivered as an email attachment The subject line and email content enticed the employee to open the attachment. Which of the following attack vectors BEST matches this malware?
A. Embedded Python code
B. Macro-enabled file
C. Bash scripting
D. Credential-harvesting website
-
Question 397:
A Chief Information Security Officer has defined resiliency requirements for a new data center architecture The requirements are as follows
1.
Critical fileshares will remain accessible during and after a natural disaster
2.
Frve percent of hard disks can fail at any given time without impacting the data.
3.
Systems will be forced to shut down gracefully when battery levels are below 20%
Which of the following are required to BEST meet these objectives? (Select THREE)
A. Fiber switching
B. laC
C. NAS
D. RAID
E. UPS
F. Redundant power supplies
G. Geographic dispersal
H. Snapshots
I. Load balancing
-
Question 398:
Which of the following risk management strategies would an organization use to maintain a legacy system with known risks for operational purposes?
A. Acceptance
B. Transference
C. Avoidance
D. Mitigation
-
Question 399:
A security analyst has been asked by the Chief Information Security Officer to ?develop a secure method of providing centralized management of infrastructure
1.
reduce the need to constantly replace aging end user machines
2.
provide a consistent user desktop expenence Which of the following BEST meets these requirements?
A. BYOD
B. Mobile device management
C. VDI
D. Containers ation
-
Question 400:
Which of the following would be the BEST way to analyze diskless malware that has infected a VDI?
A. Shut down the VDI and copy off the event logs.
B. Take a memory snapshot of the running system.
C. Use NetFlow to identify command-and-control IPs.
D. Run a full on-demand scan of the root volume.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-601 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.