Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 971:
A tester was able to leverage a pass-the-hash attack during a recent penetration test. The tester gained a foothold and moved laterally through the network. Which of the following would prevent this type of attack from reoccurring?
A. Renaming all active service accounts and disabling all inactive service accounts
B. Creating separate accounts for privileged access that are not used to log on to local machines
C. Enabling full-disk encryption on all workstations that are used by administrators and disabling RDP
D. Increasing the password complexity requirements and setting account expiration dates
-
Question 972:
A critical enterprise component whose loss or destruction would significantly impede business operations or have an outsized impact on corporate revenue is known as:
A. a single point of failure
B. critical system infrastructure
C. proprietary information.
D. a mission-essential function
-
Question 973:
A technician is auditing network security by connecting a laptop to open hardwired jacks within the facility to verify they cannot connect. Which of the following is being tested?
A. Layer 3 routing
B. Port security
C. Secure IMAP
D. S/MIME
-
Question 974:
A technician is installing a new SIEM and is configuring the system to count the number of times an event occurs at a specific logical location before the system takes action. Which of the following BEST describes the feature being configured by the technician?
A. Correlation
B. Aggregation
C. Event deduplication
D. Flood guard
-
Question 975:
A network administrator needs to restrict the users of the company's WAPs to the sales department. The network administrator changes and hides the SSID and then discovers several employees had connected their personal devices to the wireless network. Which of the following would limit access to the wireless network to only organization-owned devices in the sales department?
A. Implementing MAC filtering
B. Reducing the signal strength to encompass only the sales department
C. Replacing the APs and sales department wireless cards to support 802.11b
D. Issuing a BYOD policy
-
Question 976:
An organization uses an antivirus scanner from Company A on its firewall, an email system antivirus scanner from Company B. and an endpoint antivirus scanner from Company C. This is an example of:
A. unified threat management.
B. an OVAL system.
C. vendor diversity.
D. alternate processing sites.
-
Question 977:
The Chief information Officer (CIO) has decided to add two-factor authentication along with the use of passwords when logging on to the network. Which of the following should be implemented to BEST accomplish this requirement?
A. Require users to enter a PIN
B. Require users to set complex passwords
C. Require users to insert a smart card when logging on
D. Require the system to use a CAPTCHA
-
Question 978:
An employee on the Internet facing part of a company's website submits a 20-character phrase in a small textbox on a web form. The website returns a message back to the browser stating.
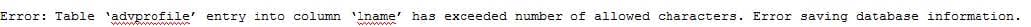
Of which of the following is this an example?
A. Resources exhaustion
B. Buffer overflow
C. Improperly configured account
D. Improper error handling
-
Question 979:
Which of the following security controls BEST mitigates social engineering attacks?
A. Separation of duties
B. Least privilege
C. User awareness training
D. Mandatory vacation
-
Question 980:
A technician wants to implement PKI-based authentication on an enterprise wireless network. Which of the following should configure to enforce the use for client-site certificates?
A. 802.1X with PEAP
B. WPA2-PSK
C. EAP-TLS
D. RADIUS Federation
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.