Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 11:
A security researcher is tracking an adversary by noting its attacks and techniques based on its capabilities, infrastructure, and victims. Which of the following is the researcher MOST likely using?
A. The Diamond Model of Intrusion Analysis
B. The Cyber Kill Chain
C. The MITRE CVE database
D. The incident response process
-
Question 12:
A technician is auditing network security by connecting a laptop to open hardwired jacks within the facility to verify they cannot connect. Which of the following is being tested?
A. Layer 3 routing
B. Port security
C. Secure IMAP
D. S/MIME
-
Question 13:
A security analyst needs to generate a server certificate to be used for 802.1X and secure RDP connections. The analyst is unsure what is required to perform the task and solicits help from a senior colleague. Which of the following is the FIRST step the senior colleague will most likely tell the analyst to perform to accomplish this task?
A. Create an OCSP
B. Generate a CSR
C. Create a CRL
D. Generate a .pfx file.
-
Question 14:
A commercial cyber-threat intelligence organization observes IoCs across a variety of unrelated customers. Prior to releasing specific threat intelligence to other paid subscribers, the organization is MOST likely obligated by contracts to:
A. perform attribution to specific APTs and nation-state actors.
B. anonymize any PII that is observed within the IoC data.
C. add metadata to track the utilization of threat intelligence reports.
D. assist companies with impact assessments based on the observed data.
-
Question 15:
A root cause analysis reveals that a web application outage was caused by one of the company's developers uploading a newer version of the third-party libraries that were shared among several applications. Which of the following implementations would be BEST to prevent this issue from reoccurring?
A. CASB
B. SWG
C. Containerization
D. Automated failover
-
Question 16:
The Chief Security Officer (CSO) at a major hospital wants to implement SSO to help improve security in the environment and protect patient data, particularly at shared terminals. The Chief Risk Officer (CRO) is concerned that training and guidance have not been provided to frontline staff, and a risk analysis has not been performed. Which of the following is the MOST likely cause of the CRO's concerns?
A. SSO would simplify username and password management, making it easier for hackers to guess accounts.
B. SSO would reduce password fatigue, but staff would still need to remember more complex passwords.
C. SSO would reduce the password complexity for frontline staff.
D. SSO would reduce the resilience and availability of systems if the identity provider goes offline.
-
Question 17:
A consultant is configuring a vulnerability scanner for a large, global organization in multiple countries. The consultant will be using a service account to scan systems with administrative privileges on a weekly basis, but there is a concern that hackers could gain access to the account and pivot throughout the global network. Which of the following would be BEST to help mitigate this concern?
A. Create different accounts for each region, each configured with push MFA notifications.
B. Create one global administrator account and enforce Kerberos authentication.
C. Create different accounts for each region, limit their logon times, and alert on risky logins.
D. Create a guest account for each region, remember the last ten passwords, and block password reuse.
-
Question 18:
A security analyst discovers that a company's username and password database was posted on an Internet forum. The username and passwords are stored in plain text. Which of the following would mitigate the damage done by this type of data exfiltration in the future?
A. Create DLP controls that prevent documents from leaving the network
B. Implement salting and hashing.
C. Configure the web content filter to block access to the forum.
D. Increase password complexity requirements.
-
Question 19:
While checking logs, a security engineer notices a number of end users suddenly downloading files with the .tar.gz extension. Closer examination of the files reveals they are PE32 files. The end users state they did not initiate any of the downloads. Further investigation reveals the end users all clicked on an external email containing an infected MHT file with an href link a week prior. Which of the following is MOST likely occurring?
A. A RAT was installed and is transferring additional exploit tools.
B. The workstations are beaconing to a command-and-control server.
C. A logic bomb was executed and is responsible for the data transfers.
D. A fireless virus is spreading in the local network environment.
-
Question 20:
SIMULATION
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
INSTRUCTIONS
Click on each firewall to do the following:
1.
Deny cleartext web traffic.
2.
Ensure secure management protocols are used.
3.
Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.


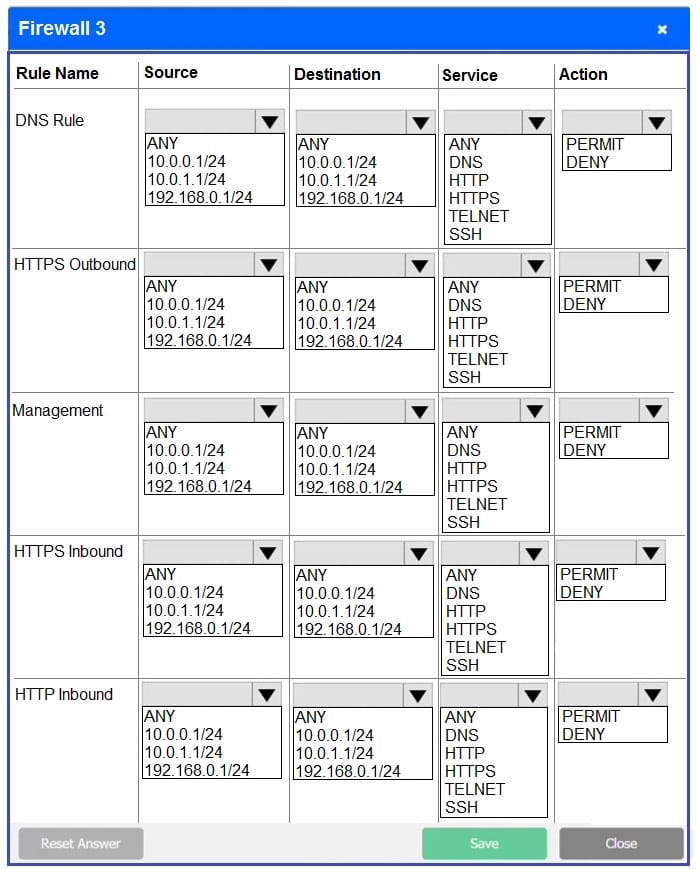
A. See explanation below.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.