Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 961:
A company is deploying a wireless network. It is a requirement that client devices must use X.509 certifications to mutually authenticate before connecting to the wireless network. Which of the following protocols would be required to accomplish this?
A. EAP-TTLS
B. EAP-MD5
C. LEAP
D. EAP-TLS
E. EAP-TOTP
-
Question 962:
Buffer overflow can be avoided using proper.
A. memory leak prevention
B. memory reuse
C. input validation
D. implementation of ASLR
-
Question 963:
A penetration tester is testing passively for vulnerabilities on a company's network. Which of the following tools should the penetration tester use? (Select TWO).
A. Zenmap
B. Wireshark
C. Nmap
D. tcpdump
E. Nikto
F. Snort
-
Question 964:
During the penetration testing of an organization, the tester was provided with the names of a few key servers, along with their IP address. Which of the following is the organization conducting?
A. Gray box testing
B. White box testing
C. Back box testing
D. Isolated container testing
E. Vulnerability testing
-
Question 965:
A network administrator was provided the following output from a vulnerability scan.
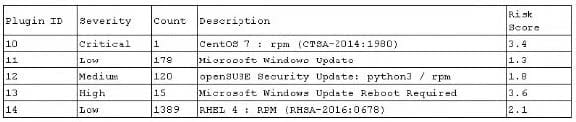
The network administrator has been instructed to prioritize remediation efforts based on overall risk to the enterprise. Which of the following plugin IDs should be remediated FIRST?
A. 10
B. 11
C. 12
D. 13
E. 14
-
Question 966:
Which of the following should a company require prior to performing a penetration test?
A. NDA
B. CVE score
C. Data classification
D. List of threats
-
Question 967:
A company is looking for an all-in-one solution to provide identification authentication, authorization, and accounting services. Which of the following technologies should the company use?
A. Diameter
B. SAML
C. Kerberos
D. CHAP
-
Question 968:
Which of the following impacts MOST likely results from poor exception handling?
A. Widespread loss of confidential data
B. Network-wide resource exhaustion
C. Privilege escalation
D. Local disruption of services
-
Question 969:
A company has a backup site with equipment on site without any data. This is an example of:
A. a hot site.
B. a cold site.
C. a hot standby.
D. a warrn site.
-
Question 970:
An internal intranet site is required to authenticate users and restrict access to content to only those who are authorized to view it The site administrator previously encountered issues with credential spoofing when using the default NTLM
setting and wants to move to a system that will be more resilient to replay attacks.
Which of the following should the administrator implement?
A. NTLMv2
B. TACACS+
C. Kerberos
D. Shibboleth
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.