Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 941:
A security analyst is testing both Windows and Linux systems for unauthorized DNS zone transfers within a LAN on comptia.org from example.org. Which of the following commands should the security analyst use? (Select two.)
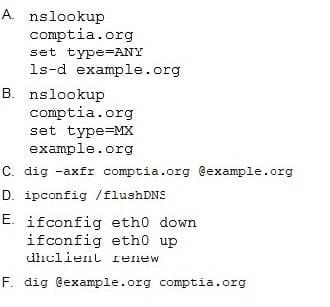
A. Option A
B. Option B
C. Option C
D. Option D
E. Option E
F. Option F
-
Question 942:
A technician suspects that a system has been compromised. The technician reviews the following log entry:
WARNING- hash mismatch: C:\Window\SysWOW64\user32.dllWARNING- hash mismatch: C:\Window\SysWOW64\kernel32.dll
Based solely ono the above information, which of the following types of malware is MOST likely installed on the system?
A. Rootkit
B. Ransomware
C. Trojan
D. Backdoor
-
Question 943:
A new firewall has been places into service at an organization. However, a configuration has not been entered on the firewall. Employees on the network segment covered by the new firewall report they are unable to access the network. Which of the following steps should be completed to BEST resolve the issue?
A. The firewall should be configured to prevent user traffic form matching the implicit deny rule.
B. The firewall should be configured with access lists to allow inbound and outbound traffic.
C. The firewall should be configured with port security to allow traffic.
D. The firewall should be configured to include an explicit deny rule.
-
Question 944:
A security administrator is Implementing a secure method that allows developers to place files or objects onto a Linux server Developers ate required to log In using a username. password, and asymmetric key. Which of the following protocols should be implemented?
A. SSL/TLS
B. SFTP
C. SRTP
D. IPSec
-
Question 945:
A technician needs lo document which application versions are listening on open ports. Which of the following is MOST likely to return the information the technician needs?
https://www.dumpsschool.com/ Questions and Answers PDF P-211
A. Banner grabbing
B. Steganography tools
C. Protocol analyzer
D. Wireless scanner
-
Question 946:
A security administrator is creating a risk assessment on BYOD. One of the requirements of the risk assessment is to address the following:
1.
Centrally managing mobile devices
2.
Data loss prevention
Which of the following recommendations should the administrator include in the assessment? (Select TWO).
A. implement encryption.
B. implement hashing.
C. implement an MDM with mobile device hardening.
D. implement a VPN with secure connection in webmail.
E. implement and allow cloud storage features on the network.
-
Question 947:
A user wants to send a confidential message to a customer to ensure unauthorized users cannot access the information. Which of the following can be used to ensure the security of the document while in transit and at rest?
A. BCRYPT
B. PGP
C. FTPS
D. S/MIME
-
Question 948:
Which of the following could an attacker use to overwrite instruction pointers in order to execute malicious code?
A. Memory leak
B. SQL injection
C. Resource exhaustion
D. Buffer overflow
-
Question 949:
After running an online password cracking tool, an attacker recovers the following password:
gh;jSKSTOi;618and
Based on the above information, which of the following technical controls have been implemented? (Select TWO).
A. Complexity
B. Encryption
C. Hashing
D. Length
E. Salting
F. Stretching
-
Question 950:
Given the following: > md5.exe filel.txt > ADIFAB103773DC6A1E6021B7E503A210 > md5.exe file2.txt > ADIFAB103773DC6A1E602lB7E503A210 Which of the following concepts of cryptography is shown?
A. Collision
B. Salting
C. Steganography
D. Stream cipher
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.