Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 731:
When a malicious user is able to retrieve sensitive information from RAM, the programmer has failed to implement:
A. session keys.
B. encryption of data at rest
C. encryption of data in use.
D. ephemeral keys.
-
Question 732:
A systems administrator is auditing the company's Active Directory environment. It is quickly noted that the username "company\bsmith" is interactively logged into several desktops across the organization. Which of the following has the systems administrator MOST likely come across?
A. Service account
B. Shared credentials
C. False positive
D. Local account
-
Question 733:
Which of the following are considered to be "something you do"? (Select TWO).
A. Iris scan
B. Handwriting
C. Common Access Card
D. Gait
E. PIN
F. Fingerprint
-
Question 734:
A security analyst wishes to scan the network to view potentially vulnerable systems the way an attacker would. Which of the following would BEST enable the analyst to complete the objective?
A. Perform a non-credentialed scan.
B. Conduct an intrusive scan.
C. Attempt escalation of privilege
D. Execute a credentialed scan.
-
Question 735:
A system in the network is used to store proprietary secrets and needs the highest level of security possible. Which of the following should a security administrator implement to ensure the system cannot be reached from the Internet?
A. VLAN
B. Air gap
C. NAT
D. Firewall
-
Question 736:
Which of the following serves to warn users against downloading and installing pirated software on company devices?
A. AUP
B. NDA
C. ISA
D. BPA
-
Question 737:
Which of the following is the MOST significant difference between intrusive and non-intrusive vulnerability scanning?
A. One uses credentials, but the other does not
B. One has a higher potential for disrupting system operations.
C. One allows systems to activate firewall countermeasures.
D. One returns service banners, including running versions
-
Question 738:
A highly complex password policy has made it nearly impossible to crack account passwords. Which of the following might a hacker still be able to perform?
A. Pass-the-hash attack
B. ARP poisoning attack
C. Birthday attack
D. Brute-force attack
-
Question 739:
A security analyst has received several reports of an issue on an internal web application. Users state they are having to provide their credentials twice to log in. The analyst checks with the application team and notes this is not an expected behavior. After looking at several logs, the analyst decides to run some commands on the gateway and obtains the following output:
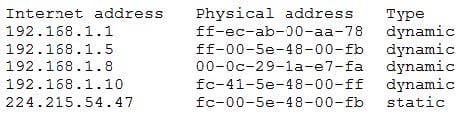
Which of the following BEST describes the attack the company is experiencing?
A. MAC flooding
B. URL redirection
C. ARP poisoning
D. DNS hijacking
-
Question 740:
A contracting company recently completed its period of performance on a government contract and would like to destroy all information associated with contract performance. Which of the following is the best NEXT step for the company to take?
A. Consult data disposition policies in the contract.
B. Use a pulper or pulverizer for data destruction
C. Retain the data for a period no more than one year
D. Burn hard copies containing Pll or PHI.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.