Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 751:
An employee workstation with an IP address of 204 211.38.211/24 reports it is unable to submit print jobs to a network printer at 204.211.38.52/24 after a firewall upgrade. The active firewall rules are as follows:
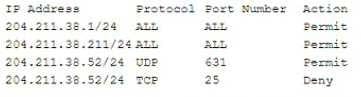
Assuming port numbers have not been changed from their defaults, which of the following should be modified to allow printing to the network printer?
A. The permit statement for 204.211.38.52/24 should be changed to TCP port 631 instead of UDP.
B. The deny statement for 204 211.38.52/24 should be changed to a permit statement
C. The permit statement for 204.211.38.52/24 should be changed to UDP port 443 instead of 631
D. The permit statement for 204.211.38 211/24 should be changed to TCP port 631 only instead of ALL
-
Question 752:
During a forensics investigation, which of the following must be addressed FIRST according to the order of volatility?
A. Hard drive
B. RAM
C. Network-attached storage
D. USB flash drive
-
Question 753:
A recent audit uncovered a key finding regarding the use of a specific encryption standard in a web application that is used to communicate with business customers. Due to the technical limitations of its customers, the company is unable to upgrade the encryption standard. Which of the following types of controls should be used to reduce the risk created by this scenario?
A. Physical
B. Detective
C. Preventive
D. Compensating
-
Question 754:
Which of the following access management concepts is MOST closely associated with the use of a password or PIN?
A. Authorization
B. Authentication
C. Accounting
D. Identification
-
Question 755:
A security analyst is hardening a large-scale wireless network. The primary requirements are the following
*
Must use authentication through EA
*
Must use an AAA server
*
Must use the most secure encryption protocol
Given these requirements, which of the following should the analyst implement and recommend? (Select TWO).
A.
802.1X
B.
802.3
C.
LDAP
D.
TKIP
E.
CCMP
F.
WPA2-PSK
-
Question 756:
An accountant is attempting to log in to the internal accounting system and receives a message that the website's certificate is fraudulent. The accountant finds instructions for manually installing the new trusted root onto the local machine. Which of the following would be the company's BEST option for this situation in the future?
A. Utilize a central CRL.
B. Implement certificate management.
C. Ensure access to KMS.
D. Use a stronger cipher suite.
-
Question 757:
A security consultant was asked to revise the security baselines that are utilized by a large organization. Although the company provides different platforms for its staff, including desktops, laptops, and mobile devices, the applications do not vary by platform. Which of the following should the consultant recommend? (Select Two).
A. Apply patch management on a daily basis.
B. Allow full functionality for all applications that are accessed remotely
C. Apply default configurations of all operating systems
D. Apply application whitelisting.
E. Disable default accounts and/or passwords.
-
Question 758:
A junior systems administrator noticed that one of two hard drives in a server room had a red error notification. The administrator removed the hard drive to replace it but was unaware that the server was configured in an array. Which of the following configurations would ensure no data is lost?
A. RAID 0
B. RAID 1
C. RAID 2
D. RAID 3
-
Question 759:
A security engineer at a manufacturing company is implementing a third-party cloud application. Rather than creating users manually in the application, the engineer decides to use the SAML protocol. Which of the following is being used for this implementation?
A. The manufacturing company is the service provider, and the cloud company is the identity provider.
B. The manufacturing company is the authorization provider, and the cloud company is the service provider.
C. The manufacturing company is the identity provider, and the cloud company is the OAuth provider.
D. The manufacturing company is the identity provider, and the cloud company is the service provider.
E. The manufacturing company is the service provider, and the cloud company is the authorization provider.
-
Question 760:

A user receives a security alert pop-up from the host-based IDS, and a few minutes later notices a document on the desktop has disappeared and in its place is an odd filename with no icon image. When clicking on this icon, the user receives a system notification that it cannot find the correct program to use to open this file. Which of the following types of malware has MOST likely targeted this workstation?
A. Rootkit
B. Spyware
C. Ransomware
D. Remote-access Trojan
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.