Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 51:
Joe recently assumed the role of data custodian for this organization. While cleaning out an unused storage safe, he discovers several hard drives that are labeled "unclassified" and awaiting destruction. The hard drives are obsolete and cannot be installed in any of his current computing equipment. Which of the following is the BEST method for disposing of the hard drives?
A. Burning
B. Wiping
C. Purging
D. Pulverizing
-
Question 52:
A network administrator is creating a new network for an office. For security purposes, each department should have its resources isolated from every other department but be able to communicate back to central servers. Which of the following architecture concepts would BEST accomplish this?
A. Air gapped network
B. Load balanced network
C. Network address translation
D. Network segmentation
-
Question 53:
A customer calls a technician and needs to remotely connect to a web server to change some code manually. The technician needs to configure the user's machine with protocols to connect to the Unix web server, which is behind a firewall. Which of the following protocols does the technician MOST likely need to configure?
A. SSH
B. SFTP
C. HTTPS
D. SNMP
-
Question 54:
A security analyst is assessing a small company's internal servers against recommended security practices. Which of the following should the analyst do to conduct the assessment? (Choose two.)
A. Compare configurations against platform benchmarks
B. Confirm adherence to the company's industry-specific regulations
C. Review the company's current security baseline
D. Verify alignment with policy related to regulatory compliance
E. Run an exploitation framework to confirm vulnerabilities
-
Question 55:
Which of the following are considered among the BEST indicators that a received message is a hoax? (Choose two.)
A. Minimal use of uppercase letters in the message
B. Warnings of monetary loss to the receiver
C. No valid digital signature from a known security organization
D. Claims of possible damage to computer hardware
E. Embedded URLs
-
Question 56:
Management wishes to add another authentication factor in addition to fingerprints and passwords in order to have three-factor authentication. Which of the following would BEST satisfy this request?
A. Retinal scan
B. Passphrase
C. Token fob
D. Security question
-
Question 57:
During a lessons learned meeting regarding a previous incident, the security team receives a follow- up action item with the following requirements:
Allow authentication from within the United States anytime Allow authentication if the user is accessing email or a shared file system Do not allow authentication if the AV program is two days out of date
Do not allow authentication if the location of the device is in two specific countries Given the requirements, which of the following mobile deployment authentication types is being utilized?
A. Geofencing authentication
B. Two-factor authentication
C. Context-aware authentication
D. Biometric authentication
-
Question 58:
A systems administrator has implemented multiple websites using host headers on the same server.
The server hosts two websites that require encryption and other websites where encryption is optional. Which of the following should the administrator implement to encrypt web traffic for the required websites?
A. Extended domain validation
B. TLS host certificate
C. OCSP stapling
D. Wildcard certificate
-
Question 59:
A security analyst is doing a vulnerability assessment on a database server. A scanning tool returns the following information:
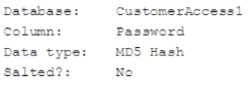
There have been several security breaches on the web server that accesses this database. The security team is instructed to mitigate the impact of any possible breaches. The security team is also instructed to improve the security on this database by making it less vulnerable to offline attacks. Which of the following would BEST accomplish these goals? (Choose two.)
A. Start using salts to generate MD5 password hashes
B. Generate password hashes using SHA-256
C. Force users to change passwords the next time they log on
D. Limit users to five attempted logons before they are locked out
E. Require the web server to only use TLS 1.2 encryption
-
Question 60:
Which of the following is a major difference between XSS attacks and remote code exploits?
A. XSS attacks use machine language, while remote exploits use interpreted language
B. XSS attacks target servers, while remote code exploits target clients
C. Remote code exploits aim to escalate attackers' privileges, while XSS attacks aim to gain access only
D. Remote code exploits allow writing code at the client side and executing it, while XSS attacks require no code to work
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.