Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 71:
A buffer overflow can result in:
A. loss of data caused by unauthorized command execution.
B. privilege escalation caused by TPN override.
C. reduced key strength due to salt manipulation.
D. repeated use of one-time keys.
-
Question 72:
A call center company wants to implement a domain policy primarily for its shift workers. The call center has large groups with different user roles. Management wants to monitor group performance. Which of the following is the BEST solution for the company to implement?
A. Reduced failed logon attempts
B. Mandatory password changes
C. Increased account lockout time
D. Time-of-day restrictions
-
Question 73:
A security administrator is implementing a new WAF solution and has placed some of the web servers behind the WAF, with the WAF set to audit mode. When reviewing the audit logs of external requests and posts to the web servers, the administrator finds the following entry:
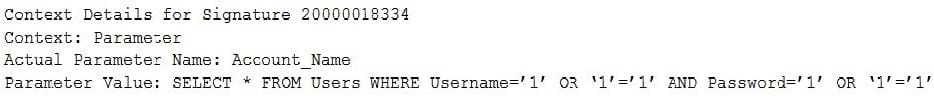
Based on this data, which of the following actions should the administrator take?
A. Alert the web server administrators to a misconfiguration.
B. Create a blocking policy based on the parameter values.
C. Change the parameter name `Account_Name' identified in the log.
D. Create an alert to generate emails for abnormally high activity.
-
Question 74:
Which of the following is the BEST way for home users to mitigate vulnerabilities associated with IoT devices on their home networks?
A. Power off the devices when they are not in use,
B. Prevent IoT devices from contacting the Internet directly.
C. Apply firmware and software updates upon availability.
D. Deploy a bastion host on the home network.
-
Question 75:
Corporations choose to exceed regulatory framework standards because of which of the following incentives?
A. It improves the legal defensibility of the company.
B. It gives a social defense that the company is not violating customer privacy laws.
C. It proves to investors that the company takes APT cyber actors seriously
D. It results in overall industrial security standards being raised voluntarily.
-
Question 76:
Which of the following BEST explains why sandboxing is a best practice for testing software from an untrusted vendor prior to an enterprise deployment?
A. It allows the software to run in an unconstrained environment with full network access.
B. It eliminates the possibility of privilege escalation attacks against the local VM host.
C. It facilitates the analysis of possible malware by allowing it to run until resources are exhausted.
D. It restricts the access of the software to a contained logical space and limits possible damage.
-
Question 77:
A small- to medium-sized company wants to block the use of USB devices on its network. Which of the following is the MOST cost-effective way for the security analyst to prevent this?
A. Implement a DLP system
B. Apply a GPO
C. Conduct user awareness training
D. Enforce the AUP.
-
Question 78:
A group of developers is collaborating to write software for a company. The developers need to work in subgroups and control who has access to their modules. Which of the following access control methods is considered user-centric?
A. Time-based
B. Mandatory
C. Rule-based
D. Discretionary
-
Question 79:
Which of the following methods minimizes the system interaction when gathering information to conduct a vulnerability assessment of a router?
A. Download the configuration
B. Run a credentialed scan.
C. Conduct the assessmenet during downtime
D. Change the routing to bypass the router.
-
Question 80:
Which of the following is the main difference an XSS vulnerability and a CSRF vulnerability?
A. XSS needs the attacker to be authenticated to the trusted server.
B. XSS does not need the victim to be authenticated to the trusted server.
C. CSRF needs the victim to be authenticated to the trusted server.
D. CSRF does not need the victim to be authenticated to the trusted server.
E. CSRF does not need the attacker to be authenticated to the trusted server.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.