Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 571:
After being alerted to potential anomalous activity related to trivial DNS lookups, a security analyst looks at the following output of implemented firewall rules:
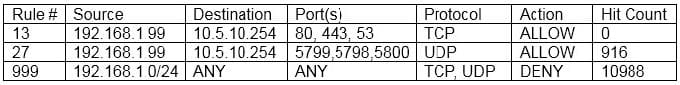
The analyst notices that the expected policy has no hit count for the day. Which of the following MOST likely occurred?
A. Data execution prevention is enabled.
B. The VLAN is not trunked properly.
C. There is a policy violation for DNS lookups.
D. The firewall policy is misconfigured.
-
Question 572:
The application team within a company is asking the security team to investigate why its application is slow after an upgrade. The source of the team's application is 10.13.136.9, and the destination IP is 10.17.36.5. The security analyst pulls the logs from the endpoint security software but sees nothing is being blocked. The analyst then looks at the UTM firewall logs and sees the following:
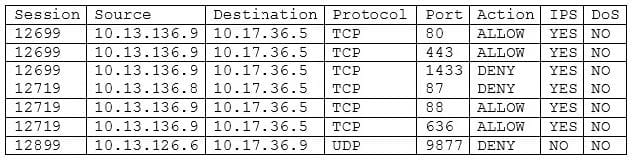
Which of the following should the security analyst request NEXT based on the UTM firewall analysis?
A. Request the application team to allow TCP port 87 to listen on 10.17.36.5.
B. Request the network team to open port 1433 from 10.13.136.9 to 10.17.36.5.
C. Request the network team to turn off IPS for 10.13.136.8 going to 10.17.36.5.
D. Request the application team to reconfigure the application and allow RPC communication.
-
Question 573:
After a systems administrator installed and configured Kerberos services, several users experienced authentication issues. Which of the following should be installed to resolve these issues?
A. RADIUS server
B. NTLM service
C. LDAP service
D. NTP server
-
Question 574:
A Chief Security Office's (CSO's) key priorities are to improve preparation, response, and recovery practices to minimize system downtime and enhance organizational resilience to ransomware attacks. Which of the following would BEST meet the CSO's objectives?
A. Use email-filtering software and centralized account management, patch high-risk systems, and restrict administration privileges on fileshares.
B. Purchase cyber insurance from a reputable provider to reduce expenses during an incident.
C. Invest in end-user awareness training to change the long-term culture and behavior of staff and executives, reducing the organization's susceptibility to phishing attacks.
D. Implement application whitelisting and centralized event-log management, and perform regular testing and validation of full backups.
-
Question 575:
Which of the following is a reason why an organization would define an AUP?
A. To define the lowest level of privileges needed for access and use of the organization's resources
B. To define the set of rules and behaviors for users of the organization's IT systems
C. To define the intended partnership between two organizations
D. To define the availability and reliability characteristics between an IT provider and consumer
-
Question 576:
An intruder sniffs network traffic and captures a packet of internal network transactions that add funds to a game card. The intruder pushes the same packet multiple times across the network, which increments the funds on the game card. Which of the following should a security administrator implement to BEST protect against this type of attack?
A. An IPS
B. A WAF
C. SSH
D. An IPSec VPN
-
Question 577:
Which of the following is the MAIN disadvantage of using SSO?
A. The architecture can introduce a single point of failure.
B. Users need to authenticate for each resource they access.
C. It requires an organization to configure federation.
D. The authentication is transparent to the user.
-
Question 578:
Which of the following BEST describes the concept of perfect forward secrecy?
A. Using quantum random number generation to make decryption effectively impossible
B. Preventing cryptographic reuse so a compromise of one operation does not affect other operations
C. Implementing elliptic curve cryptographic algorithms with true random numbers
D. The use of NDAs and policy controls to prevent disclosure of company secrets
-
Question 579:
An organization plans to transition the intrusion detection and prevention techniques on a critical subnet to an anomaly-based system. Which of the following does the organization need to determine for this to be successful?
A. The baseline
B. The endpoint configurations
C. The adversary behavior profiles
D. The IPS signatures
-
Question 580:
Joe, an employee, knows he is going to be fired in three days. Which of the following is Joe?
A. An insider threat
B. A competitor
C. A hacktivist
D. A state actor
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.