Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 491:
Which of the following concepts ensure ACL rules on a directory are functioning as expected? (Select TWO).
A. Accounting
B. Authentication
C. Auditing
D. Authorization
E. Non-repudiation
-
Question 492:
Which of the following may indicate a configuration Hem has reached end-of-life?
A. The device will no longer turn on and indicates an error
B. The vendor has not published security patches recently.
C. The object has been removed from the Active Directory.
D. Logs show a performance degradation of the component.
-
Question 493:
A security administrator is adding a NAC requirement for all VPN users to ensure the co requirement?
A. Implement a permanent agent.
B. Install antivirus software.
C. Use an agentless implementation.
D. Implement PKI.
-
Question 494:
A systems administrator wants to implement a secure wireless network requiring wireless clients to pre-register with the company and install a PKI client certificate prior to being able to connect to the wireless network.
Which of the following should the systems administrator configure?
A. EAP-TTLS
B. EAP-TLS
C. EAP-FAST
D. EAP with PEAP
E. EAP with MSCHAPv2
-
Question 495:
An organization is concerned that Its hosted web servers are not running the most updated version of the software. Which of the following would work BEST to help identify potential vulnerabilities?
A. hping3 -s compwia.org -p 80
B. nc -1 -v compria.org -p 60
C. nmap comptia.org -p 80 -sv
D. nslookup -port-80 compcia.org
-
Question 496:
Given the output:
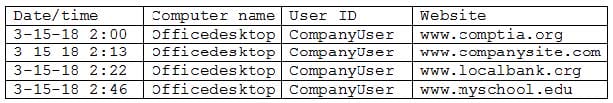
Which of the following account management practices should the security engineer use to mitigate the identified risk?
A. Implement least privilege.
B. Eliminate shared accounts.
C. Eliminate password reuse.
D. Implement two-factor authentication.
-
Question 497:
A technician needs to document which application versions are listening on open ports. Which of the following is MOST likely to return the information the technician needs?
A. Banner grabbing
B. Steganography tools
C. Protocol analyzer
D. Wireless scanner
-
Question 498:
The network information for a workstation is as follows:

When the workstation's user attempts to access www.example.com. the URL that actually opens is www.notexample.com. The user successfully connects to several other legitimate URLs. Which of the following have MOST likely occurred? (Select TWO).
A. ARP poisoning
B. Buffer overflow
C. DNS poisoning
D. Domain hijacking
E. IP spoofing
-
Question 499:
A security analyst needs to be proactive in understanding the types of attacks that could potentially target the company's executives. Which of the following intelligence sources should the security analyst review?
A. Vulnerability feeds
B. Trusted automated exchange of indicator Information
C. Structured threat information expression
D. Industry Information-sharing and collaboration groups
-
Question 500:
A security analyst is performing a forensic investigation involving compromised account credentials. Using the Event Viewer, the analyst was able to defect the following message: "Special privileges assigned to new logon.' Several of these messages did not have a valid logon associated with the user before these privileges were assigned.
Which of the following attacks is MOST likely being detected?
A. Pass-the-hash
B. Buffer overflow
C. Cross-site scripting
D. Session replay
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.