Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 481:
An Organization wants to separate permissions for individuals who perform system changes from individuals who perform auditing of those system changes. Which of the following access control approaches is BEST suited for this?
A. Assign administrators and auditors to different groups and restrict permissions on system log files to read-only for the auditor group.
B. Assign administrators and auditors to the same group, but ensure they have different permissions based on the function they perform.
C. Create two groups and ensure each group has representation from both the auditors and the administrators so they can verify any changes that were made.
D. Assign file and folder permissions on an Individual user basis and avoid group assignment altogether.
-
Question 482:
A company uses an enterprise desktop imaging solution to manage deployment of its desktop computers. Desktop computer users are only permitted to use software that is part of the baseline image. Which of the following technical solutions was MOST likely deployed by the company to ensure only known-good software can be installed on corporate desktops?
A. Network access control
B. Configuration manager
C. Application whitelisting
D. File integrity checks
-
Question 483:
A cybersecurity administrator needs to add disk redundancy for a critical server. The solution must have a two-drive failure for better fault tolerance. Which of the following RAID levels should the administrator select?
A. 0
B. 1
C. 5
D. 6
-
Question 484:
A company recently experienced a security incident in which its domain controllers were the target of a DoS attack. In which of the following steps should technicians connect domain controllers to the network and begin authenticating users again?
A. Preparation
B. Identification
C. Containment
D. Eradication
E. Recovery
F. Lessons learned
-
Question 485:
A large Industrial system's smart generator monitors the system status and sends alerts to third-party maintenance personnel when critical failures occur. While reviewing the network logs, the company's security manager notices the generator's IP is sending packets to an internal file server's IP. Which of the following mitigations would be BEST for the security manager to implement while maintaining alerting capabilities?
A. Segmentation
B. Firewall whitelisting
C. Containment
D. Isolation
-
Question 486:
A company wants to configure its wireless network to require username and password authentication. Which of the following should the systems administrator Implement?
A. WPS
B. PEAP
C. TKIP
D. PKl
-
Question 487:
Which of the following explains why a vulnerability scan might return a false positive?
A. The scan is performed at a time of day when the vulnerability does not exist.
B. The test Is performed against the wrong host.
C. The signature matches the product but not the version information.
D. The hosts are evaluated based on an OS-specific profile.
-
Question 488:
A government contracting company Issues smartphones lo employees lo enable access lo corporate resources. Several employees will need to travel to a foreign country (or business purposes and will require access lo their phones. However, the company recently received intelligence that its intellectual property is highly desired by the same country's government. Which of the following MDM configurations would BEST reduce the risk of compromise while on foreign soil?
A. Disable firmware OTA updates.
B. Disable location services.
C. Disable push notification services.
D. Disable wipe.
-
Question 489:
Which of the following attacks can be mitigated by proper data retention policies?
A. Dumpster diving
B. Man-in-the-browser
C. Spear phishing
D. Watering hole
-
Question 490:
An Organization requires secure configuration baselines for all platforms and technologies that are used. If any system cannot conform to the secure baseline, the organization must process a risk acceptance and receive approval before the system is placed into production. It may have non- conforming systems in its lower environments (development and staging) without risk acceptance, but must receive risk approval before the system is placed in production. Weekly scan reports identify systems that do not conform to any secure baseline. The application team receive a report with the following results:
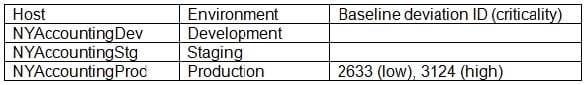
There are currently no risk acceptances for baseline deviations. This is a mission-critical application, and the organization cannot operate If the application is not running. The application fully functions in the development and staging environments. Which of the following actions should the application team take?
A. Remediate 2633 and 3124 immediately.
B. Process a risk acceptance for 2633 and 3124.
C. Process a risk acceptance for 2633 and remediate 3124.
D. Shut down NYAccountingProd and Investigate the reason for the different scan results.
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+CLO-002
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.