Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 321:
Ann, a new employee, received an email from an unknown source indicating she needed to click on the provided link to update her company's profile. Once Ann clicked the link, a command prompt appeared with the following output:
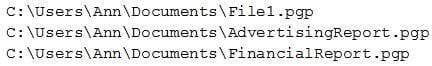
Which of the following types of malware was executed?
A. Ransomware
B. Adware
C. Spyware
D. Virus
-
Question 322:
A network technician is designing a network for a small company. The network technician needs to implement an email server and web server that will be accessed by both internal employees and external customers. Which of the following would BEST secure the internal network and allow access to the needed servers?
A. Implementing a site-to-site VPN for server access.
B. Implementing a DMZ segment for the server.
C. Implementing NAT addressing for the servers.
D. Implementing a sandbox to contain the servers.
-
Question 323:
Which of the following identity access methods creates a cookie on the first login to a central authority to allow logins to subsequent applications without re-entering credentials?
A. Multifactor authentication
B. Transitive trust
C. Federated access
D. Single sign-on
-
Question 324:
A developer has incorporated routines into the source code for controlling the length of the input passed to the program. Which of the following types of vulnerabilities is the developer protecting the code against?
A. DLL injection
B. Memory leak
C. Buffer overflow
D. Pointer dereference
-
Question 325:
An application developer has neglected to include input validation checks in the design of the company's new web application. An employee discovers that repeatedly submitting large amounts of data, including custom code, to an application will allow the execution of the custom code at the administrator level. Which of the following BEST identifies this application attack?
A. Cross-site scripting
B. Clickjacking
C. Buffer overflow
D. Replay
-
Question 326:
Joe, a user, reports to the help desk that he can no longer access any documents on his PC. He states that he saw a window appear on the screen earlier, but he closed it without reading it. Upon investigation, the technician sees high disk activity on Joe's PC. Which of the following types of malware is MOST likely indicated by these findings?
A. Keylogger
B. Trojan
C. Rootkit
D. Crypto-malware
-
Question 327:
An administrator is implementing a secure web server and wants to ensure that if the web server application is compromised, the application does not have access to other parts of the server or network. Which of the following should the administrator implement? (Choose two.)
A. Mandatory access control
B. Discretionary access control
C. Rule-based access control
D. Role-based access control
E. Attribute-based access control
-
Question 328:
Management wants to ensure any sensitive data on company-provided cell phones is isolated in a single location that can be remotely wiped if the phone is lost. Which of the following technologies BEST meets this need?
A. Geofencing
B. Containerization
C. Device encryption
D. Sandboxing
-
Question 329:
A company is planning to utilize its legacy desktop systems by converting them into dummy terminals and moving all heavy applications and storage to a centralized server that hosts all of the company's required desktop applications. Which of the following describes the BEST deployment method to meet these requirements?
A. IaaS
B. VM sprawl
C. VDI
D. PaaS
-
Question 330:
When backing up a database server to LTO tape drives, the following backup schedule is used. Backups take one hour to complete:
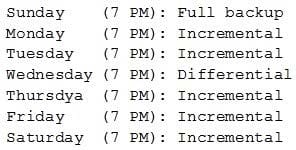
On Friday at 9:00 p.m., there is a RAID failure on the database server. The data must be restored from backup. Which of the following is the number of backup tapes that will be needed to complete this operation?
A. 1
B. 2
C. 3
D. 4
E. 6
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.