Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 311:
A manager makes an unannounced visit to the marketing department and performs a walk-through of the office. The manager observes unclaimed documents on printers. A closer look at these documents reveals employee names, addresses, ages, birth dates, marital/dependent statuses, and favorite ice cream flavors. The manager brings this to the attention of the marketing department head. The manager believes this information to be PII, but the marketing head does not agree. Having reached a stalemate, which of the following is the MOST appropriate action to take NEXT?
A. Elevate to the Chief Executive Officer (CEO) for redress; change from the top down usually succeeds.
B. Find the privacy officer in the organization and let the officer act as the arbiter.
C. Notify employees whose names are on these files that their personal information is being compromised.
D. To maintain a working relationship with marketing, quietly record the incident in the risk register.
-
Question 312:
A security administrator is choosing an algorithm to generate password hashes. Which of the following would offer the BEST protection against offline brute force attacks?
A. MD5
B. 3DES
C. AES
D. SHA-1
-
Question 313:
A user from the financial aid office is having trouble interacting with the finaid directory on the university's ERP system. The systems administrator who took the call ran a command and received the following output:
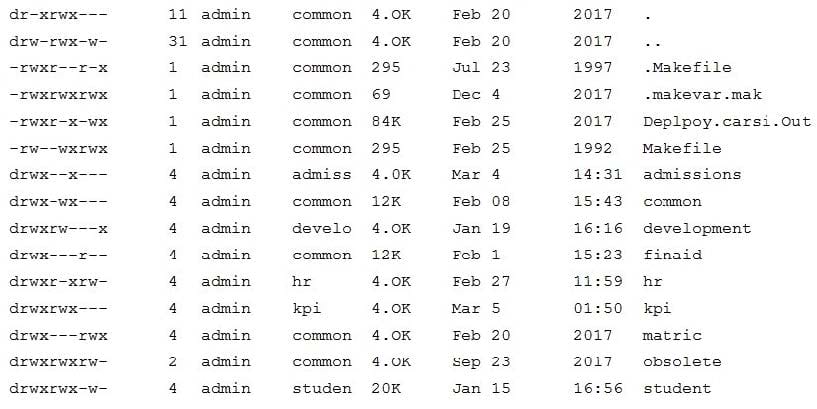
Subsequently, the systems administrator has also confirmed the user is a member of the finaid group on the ERP system. Which of the following is the MOST likely reason for the issue?
A. The permissions on the finaid directory should be drwxrwxrwx.
B. The problem is local to the user, and the user should reboot the machine.
C. The files on the finaid directory have become corrupted.
D. The finaid directory is not formatted correctly
-
Question 314:
An organization wants to ensure network access is granted only after a user or device has been authenticated. Which of the following should be used to achieve this objective for both wired and wireless networks?
A. CCMP
B. PKCS#12
C. IEEE 802.1X
D. OCSP
-
Question 315:
After the integrity of a patch has been verified, but before being deployed to production, it is important to:
A. perform static analysis
B. reverse engineer it for embedded malware.
C. run dynamic analysis on the executable.
D. test it in a staging environment
-
Question 316:
An organization has air gapped a critical system.
Which of the following BEST describes the type of attacks that are prevented by this security measure?
A. Attacks from another local network segment
B. Attacks exploiting USB drives and removable media
C. Attacks that spy on leaked emanations or signals
D. Attacks that involve physical intrusion or theft
-
Question 317:
A company has a team of penetration testers. This team has located a file on the company file server that they believe contains cleartext usernames followed by a hash. Which of the following tools should the penetration testers use to learn more about the content of this file?
A. Exploitation framework
B. Vulnerability scanner
C. Netcat
D. Password cracker
-
Question 318:
The Chief Information Security Officer (CISO) in a company is working to maximize protection efforts of sensitive corporate data. The CISO implements a "100% shred" policy within the organization, with the intent to destroy any documentation that is not actively in use in a way that it cannot be recovered or reassembled. Which of the following attacks is this deterrent MOST likely to mitigate?
A. Dumpster diving
B. Whaling
C. Shoulder surfing
D. Vishing
-
Question 319:
An organization uses application whitelisting to help prevent zero-day attacks. Malware was recently identified on one client, which was able to run despite the organization's application whitelisting approach. The forensics team has identified
the malicious file, conducted a post-incident analysis, and compared this with the original system baseline. The team sees the following output:
filename hash (SHA-1)
original: winSCP.exe 2d da b1 4a 98 fc f1 98 06 b1 e5 26 b2 df e5 f5 3e cb 83 el latest: winSCP.exe a3 4a c2 4b 85 fa f2 dd 0b ba f4 16 b2 df f2 4b 3f ac 4a e1
Which of the following identifies the flaw in the team's application whitelisting approach?
A. Their approach uses executable names and not hashes for the whitelist.
B. SHA-1 has known collision vulnerabilities and should not be used.
C. The original baseline never captured the latest file signature
D. Zero-day attacks require the latest file signatures
-
Question 320:
When used together, which of the following qualify as two-factor authentication?
A. Password and PIN
B. Smart card and PIN
C. Proximity card and smart card
D. Fingerprint scanner and iris scanner
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.