Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 1291:
When an initialization vector is added to each encryption cycle, it is using the:
A. ECB cipher mode
B. MD5 cipher mode
C. XOR cipher mode
D. CBC cipher mode
-
Question 1292:
During a routine check, a security analyst discovered the script responsible for the backup of the corporate file server has been changed to the following:
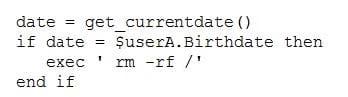
Which of the following BEST describes the type of malware the analyst discovered?
A. Keylogger
B. Rootkit
C. RAT
D. Logic bomb
-
Question 1293:
An analysis of a threat actor, which has been active for several years, reveals the threat actor has high levels of funding, motivation, and sophistication. Which of the following types of threat actors does this BEST describe?
A. Advanced persistent threat
B. Hacktivist
C. Organized crime
D. Insider
-
Question 1294:
Given the following output:
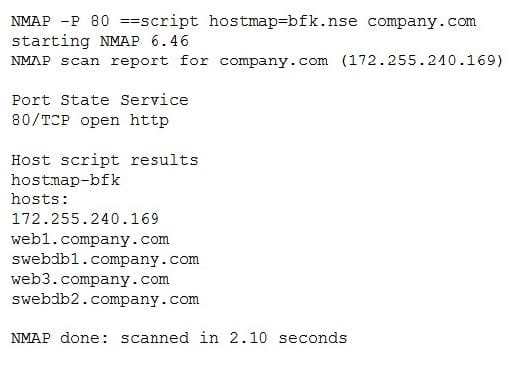
Which of the following BEST describes the scanned environment?
A. A host was identified as a web server that is hosting multiple domains
B. A host was scanned, and web-based vulnerabilities were found
C. A connection was established to a domain, and several redirect connections were identified
D. A web shell was planted in company.com's content management system
-
Question 1295:
A security analyst is determining the point of compromise after a company was hacked. The analyst checks the server logs and sees that a user account was logged in at night, and several large compressed files were exfiltrated. The analyst then discovers the user last logged in four years ago and was terminated. Which of the following should the security analyst recommend to prevent this type of attack in the future? (Choose two.)
A. Review and update the firewall settings
B. Restrict the compromised user account
C. Disable all user accounts that are not logged in to for 180 days
D. Enable a login banner prohibiting unauthorized use
E. Perform an audit of all company user accounts
F. Create a honeypot to catch the hacker
-
Question 1296:
In which of the following ways does phishing and smishing differ?
A. One is primarily based on social engineering, and the other is based on evading spam filters
B. One uses SMS as a delivery mechanism, and the other uses email
C. Smishing relies on hard-wired connections and mobile code updates
D. Phishing leverages poor email tagging to exploit SPIM settings
-
Question 1297:
A penetration tester has successfully accessed a web server using an exploit in the user-agent string for Apache Struts. The tester then brute forces a credential that provides access to the back-end database server in a different subnet. This is an example of:
A. persistence
B. pivoting
C. escalation of privilege
D. a remote access Trojan
-
Question 1298:
A software development company needs to augment staff by hiring consultants for a high-stakes project. The project has the following requirements:
1.
Consultants will have access to highly confidential, proprietary data.
2.
Consultants will not be provided with company-owned assets.
3.
Work needs to start immediately.
4.
Consultants will be provided with internal email addresses for communications.
Which of the following solutions is the BEST method for controlling data exfiltration during this project?
A. Require that all consultant activity be restricted to a secure VDI environment
B. Require the consultants to sign an agreement stating they will only use the company-provided email address for communications during the project
C. Require updated antivirus, USB blocking, and a host-based firewall on all consultant devices
D. Require the consultants to connect to the company VPN when accessing confidential resources
-
Question 1299:
Which of the following cryptography algorithms will produce a fixed-length, irreversible output?
A. AES
B. 3DES
C. RSA
D. MD5
-
Question 1300:
Which of the following must be intact for evidence to be admissible in court?
A. Chain of custody
B. Order of volatility
C. Legal hold
D. Preservation
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.