Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 1311:
When identifying a company's most valuable assets as part of a BIA, which of the following should be the FIRST priority?
A. Life
B. Intellectual property
C. Sensitive data
D. Public reputation
-
Question 1312:
An organization needs to implement a large PKI. Network engineers are concerned that repeated transmission of the OCSP will impact network performance. Which of the following should the security analyst recommend is lieu of an OCSP?
A. CSR
B. CRL
C. CA
D. OID
-
Question 1313:
When considering a third-party cloud service provider, which of the following criteria would be the BEST to include in the security assessment process? (Select two.)
A. Use of performance analytics
B. Adherence to regulatory compliance
C. Data retention policies
D. Size of the corporation
E. Breadth of applications support
-
Question 1314:
A security analyst observes the following events in the logs of an employee workstation:
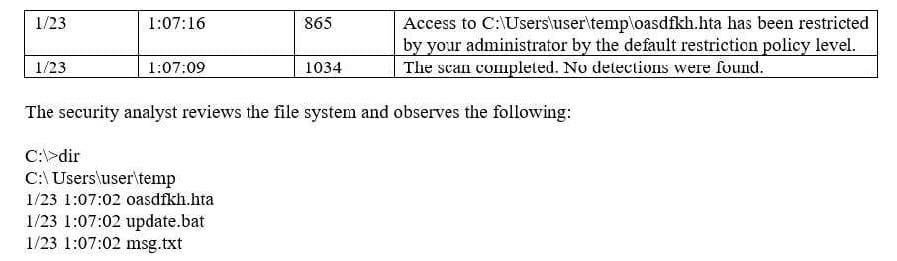
Given the information provided, which of the following MOST likely occurred on the workstation?
A. Application whitelisting controls blocked an exploit payload from executing.
B. Antivirus software found and quarantined three malware files.
C. Automatic updates were initiated but failed because they had not been approved.
D. The SIEM log agent was not tuned properly and reported a false positive.
-
Question 1315:
Which of the following would MOST likely appear in an uncredentialed vulnerability scan?
A. Self-signed certificates
B. Missing patches
C. Auditing parameters
D. Inactive local accounts
-
Question 1316:
In terms of encrypting data, which of the following is BEST described as a way to safeguard password data by adding random data to it in storage?
A. Using salt
B. Using hash algorithms
C. Implementing elliptical curve
D. Implementing PKI
-
Question 1317:
A system administrator wants to provide for and enforce wireless access accountability during events where external speakers are invited to make presentations to a mixed audience of employees and non-employees. Which of the following should the administrator implement?
A. Shared accounts
B. Preshared passwords
C. Least privilege
D. Sponsored guest
-
Question 1318:
A system administrator wants to provide balance between the security of a wireless network and usability. The administrator is concerned with wireless encryption compatibility of older devices used by some employees. Which of the following would provide strong security and backward compatibility when accessing the wireless network?
A. Open wireless network and SSL VPN
B. WPA using a preshared key
C. WPA2 using a RADIUS back-end for 802.1x authentication
D. WEP with a 40-bit key
-
Question 1319:
An information security specialist is reviewing the following output from a Linux server.
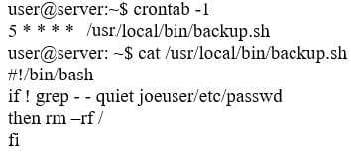
Based on the above information, which of the following types of malware was installed on the server?
A. Logic bomb
B. Trojan
C. Backdoor
D. Ransomware
E. Rootkit
-
Question 1320:
A company wants to host a publicity available server that performs the following functions:
1.
Evaluates MX record lookup
2.
Can perform authenticated requests for A and AAA records Uses RRSIG Which of the following should the company use to fulfill the above requirements?
A. LDAPS
B. DNSSEC
C. SFTP
D. nslookup
E. dig
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.