Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 1271:
A security team received reports of increased latency on a highly utilized e-commerce server. This led to eventual service unavailability as a result of internal scanning activity. The following web-server log was shared with the team to support this claim:
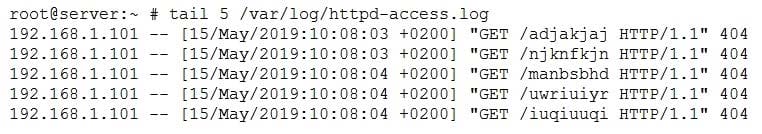
Which of the following actions would BEST address the service impact caused by scanning?
A. Enable proper error handling on the web server
B. Run scans during off peak hours
C. Stop scanning the affected servers
D. Disable directory enumeration in the scanning policy
-
Question 1272:
A company recently experienced a security breach. The security staff determined that the intrusion was due to an out-of-date proprietary software program running on a non-compliant server. The server was imaged and copied onto a hardened VM, with the previous connections re-established. Which of the following is the NEXT step in the incident response process?
A. Recovery
B. Eradication
C. Lessons learned
D. Containment
E. Identification
-
Question 1273:
A Chief Information Officer (CIO) wants to eliminate the number of calls the help desk is receiving for password resets when users log on to internal portals. Which of the following is the BEST solution?
A. Increase password length
B. Implement a self-service portal
C. Decrease lockout threshold
D. Deploy mandatory access control
-
Question 1274:
The website of a bank that an organization does business with is being reported as untrusted by the organization's web browser. A security analyst has been assigned to investigate. The analyst discovers the bank recently merged with another local bank and combined names. Additionally, the user's bookmark automatically redirects to the website of the newly named bank. Which of the following is the MOST likely cause of the issue?
A. The company's web browser is not up to date
B. The website's certificate still has the old bank's name
C. The website was created too recently to be trusted
D. The website's certificate has expired
-
Question 1275:
Which of the following threat actors is motivated primarily by a desire for personal recognition and a sense of accomplishment?
A. A script kiddie
B. A hacktivist
C. An insider threat
D. An industrial saboteur
-
Question 1276:
An attacker has gained control of several systems on the Internet and is using them to attack a website, causing it to stop responding to legitimate traffic. Which of the following BEST describes the attack?
A. MITM
B. DNS poisoning
C. Buffer overflow
D. DDoS
-
Question 1277:
A company has users and printers in multiple geographic locations, and the printers are located in common areas of the offices. To preserve the confidentiality of PII, a security administrator needs to implement the appropriate controls. Which of the following would BEST meet the confidentiality requirements of the data?
A. Enforcing location-based policy restrictions
B. Adding location to the standard naming convention
C. Implementing time-of-day restrictions based on location
D. Conducting regular account maintenance at each location
-
Question 1278:
Exploitation of a system using widely known credentials and network addresses that results in DoS is an example of:
A. improper error handling
B. default configurations
C. untrained users
D. lack of vendor support
-
Question 1279:
Which of the following is an example of the second A in the AAA model?
A. The encryption protocol successfully completes the handshake and establishes a connection
B. The one-time password is keyed in, and the login system grants access
C. The event log records a successful login with a type code that indicates an interactive login
D. A domain controller confirms membership in the appropriate group
-
Question 1280:
An organization uses an antivirus scanner from Company A on its firewall, an email system antivirus scanner from Company B, and an endpoint antivirus scanner from Company C. This is an example of:
A. unified threat management
B. an OVAL system
C. vendor diversity
D. alternate processing sites
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.