Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 1001:
An application developer is working on a new calendar and scheduling application. The developer wants to test new functionality that is time/date dependent and set the local system time to one year in the future. The application also has a feature that uses SHA-256 hashing and AES encryption for data exchange. The application attempts to connect to a separate remote server using SSL, but the connection fails. Which of the following is the MOST likely cause and next step?
A. The date is past the certificate expiration; reset the system to the current time and see if the connection still fails.
B. The remote server cannot support SHA-256; try another hashing algorithm like SHA+1 and see if the application can connect.
C. AES date/time dependent either the system time to the correct time or try a different encryption approach.
D. SSL is not the correct protocol to use in this situation-damage to TLS and by the client- server connection again
-
Question 1002:
A security analyst investigate a report from an employee in the human resources (HR) department who is issues with Internal access. When the security analyst pull the UTM logs for the IP addresses in the HR group, the following activity is shown:
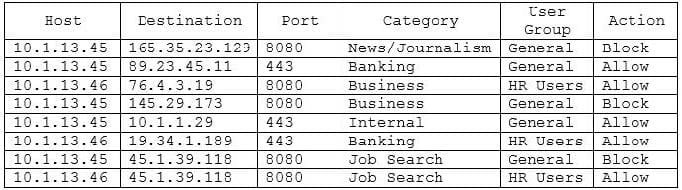
Which of the following actions should the security analyst take?
A. Ensure the HR employee is in the appropriate user group
B. Allow port 8080 on the UTM for all outgoing traffic
C. Disable the proxy settings on the HR employee's device.
D. Edit the last line Of the ACL On the UTM lo: allow any any.
-
Question 1003:
After a breach, a company has decided to implement a solution to better understand the technique used by the attackers. Which of the following is the BEST solution to be deployed?
A. Network analyzer
B. Protocol analyzer
C. Honeypot network
D. Configuration compliance scanner
-
Question 1004:
A company notices that at 10 a.m. every Thursday, three users' computers become inoperable. The security analyst team discovers a file called where.pdf.exe that runs on system startup. The contents of where.pdf.exe are shown below:

Based on the above information, which of the following types of malware was discovered?
A. Rootkit
B. Backdoor
C. Logic bomb
D. RAT
-
Question 1005:
Which of the following is the purpose of an industry-standard framework?
A. To promulgate compliance requirements for sales of common IT systems
B. To provide legal relief to participating organizations in the event of a security breach
C. To promulgate security settings on a vendor-by-vendor basis
D. To provide guidance across common system implementations
-
Question 1006:
A security analyst recommends implementing SSL for an existing web service. A technician installs the SSL certificate and successfully tests the connection on the server Soon after, the help desk begins receiving calls from users who are unable to log in After further investigation, it becomes clear that no users have successfully logged in since the certificate installation. Which of the following is MOST likely the issue?
A. Incorrect firewall rules are blocking HTTPS traffic.
B. Users are still accessing the IP address and not the HTTPS address.
C. Workstations need an updated trusted sites list
D. Users are not using tokens to log on.
-
Question 1007:
A technician suspects that a desktop was compromised with a rootkit. After removing lhe hard drive from the desktop and running an offline le integrity check, the technician reviews the following output:
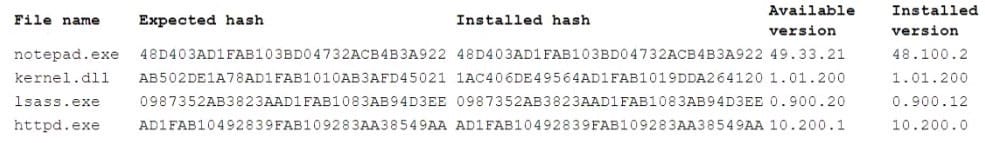
Based on the above output, which of the following is the malicious file?
A. notepad.exe
B. lsass.exe
C. kernel.dll
D. httpd.axe
-
Question 1008:
A network administrator wants to gather information on the security of the network servers in the DMZ. The administrator runs the following command:
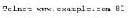
Which of the following actions is the administrator performing?
A. Grabbing the web server banner
B. Logging into the web server
C. Harvesting cleartext credentials
D. Accessing the web server management console
-
Question 1009:
During a routine check, a security analyst discovered the script responsible for the backup of the corporate file server had been changed to the following.
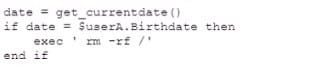
Which of the following BEST describes the type of malware the analyst discovered?
A. Key logger
B. Rootkit
C. RAT
D. Logic bomb
-
Question 1010:
When building a hosted datacenter. Which of the following is the MOST important consideration for physical security within the datacenter?
A. Security guards
B. Cameras
C. Secure enclosures
D. Biometrics
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.