Exam Details
Exam Code
:SY0-501Exam Name
:CompTIA Security+Certification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:1423 Q&AsLast Updated
:Sep 04, 2023
CompTIA CompTIA Certifications SY0-501 Questions & Answers
-
Question 1021:
A security engineer deploys a certificate from a commercial CA to the RADIUS server for use with the EAP-TLS wireless network. Authentication is failing, so the engineer examines the certificate's properties:
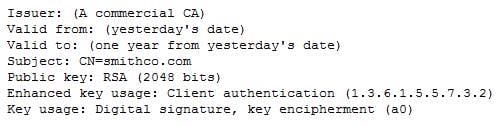
Which of the following is the MOST likely cause of the failure?
A. The certificate is missing the proper OID.
B. The certificate is missing wire-less authentication in key usage.
C. The certificate is self-signed.
D. The certificate has expired.
-
Question 1022:
A NIPS administrator needs to install a new signature to observe the behavior of a worm that may be spreading over SMB. Which of the following signatures should be installed on the NIPS'?
A. PERMIT from ANY:ANY to ANY:445 regex '.-SMB.-'
B. DROP from ANY:445 Co ANY:445 regex '.-SMB.*'
C. DENY from ANY:ANY Co ANY:445 regex '.*SMB.*'
D. RESET from ANY:ANY co ANY:445 regex '.-3MB.-'
-
Question 1023:
Penetration testing is distinct from vulnerability scanning primarily because penetration testing:
A. leverages credentials scanning to obtain persistence.
B. involve multiple active exploitation technique
C. relies exclusively on passive exploitation attempts for pivoting
D. relies on misconfiguration of security controls.
-
Question 1024:
While testing a new application, a developer discovers that the inclusion of an apostrophe in a username cause the application to crash. Which of the following secure coding techniques would be MOST useful to avoid this problem?
A. Input validation
B. Code signing
C. Obfuscation
D. Encryption
-
Question 1025:
Which of the following cloud models is used to share resources and information with business partners and like businesses without allowing everyone else access?
A. Public
B. Hybrid
C. Community
D. Private
-
Question 1026:
Staff members of an organization received an email message from the Chief Executive Officer (CEO) asking them for an urgent meeting in the main conference room. When the staff assembled, they learned the message received was not actually from the CEO. Which of the following BEST represents what happened?
A. Spear phoshing attack
B. Whaling attack
C. Phishing attack
D. Vishing attack
-
Question 1027:
An organization is setting up a satellite office and wishes to extend the corporate network to the new site. Which of the following is the BEST solution to allow the users to access corporate resources while focusing on usability and security?
A. Federated services
B. Single sign-on
C. Site-to-site VPN
D. SSL accelerators
-
Question 1028:
Which of the following physical security controls is MOST effective when trying to prevent tailgating?
A. CCTV
B. Mantrap
C. Biometrics
D. RFID badge
E. Motion detection
-
Question 1029:
A security analyst wants to limit the use of USB and external drives to protect against malware. as well as protect les leaving a user's computer. Which of the following is the BEST method to use?
A. Firewall
B. Router
C. Antivirus software
D. Data loss prevention
-
Question 1030:
A technician wants to configure a wireless router at a small office that manages a family- owned dry cleaning business. The router will support five laptops, potential smartphones, a wireless printer, and occasional guests. Which of the following wireless configuration is BEST implemented in this scenario?
A. Single SSID with WPA2-Enterprise
B. 802.1X with guest VLAN
C. Dual SSID with WPA2-PSK
D. Captive portal with two-factor authentication
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SY0-501 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.