Exam Details
Exam Code
:SALESFORCE-MULESOFT-DEVELOPER-IIExam Name
:Salesforce Certified MuleSoft Developer IICertification
:Salesforce CertificationsVendor
:SalesforceTotal Questions
:60 Q&AsLast Updated
:Aug 15, 2025
Salesforce Salesforce Certifications SALESFORCE-MULESOFT-DEVELOPER-II Questions & Answers
-
Question 51:
A healthcare portal needs to validate the token that it sends to a Mule API. The developer plans to implement a custom policy using the HTTP Policy Transform Extension to match the token received in the header from the heathcare portal. Which files does the developer need to create in order to package the custom policy?
A. Deployable ZIP file, YAML configuration file
B. JSON properties file, YAML configuration file
C. JSON properties file, XML template file
D. XML template file, YAML configuration file
-
Question 52:
Which type of cache invalidation does the Cache scope support without having to write any additional code?
A. Write-through invalidation
B. White-behind invalidation
C. Time to live
D. Notification-based invalidation
-
Question 53:
What is the MuleSoft recommended method to encrypt sensitive property data?
A. The encryption key and sensitive data should be different for each environment
B. The encryption key should be identical for all environments
C. The encryption key should be identical for all environments and the sensitive data should be different for each environment
D. The encryption key should be different for each environment and the sensitive data should be the same for all environments
-
Question 54:
Which statement is true when using XML SDK for creating custom message processors?
A. Properties are fields defined by an end user of the XML SDK component and serve as a global configuration for the entire Mule project in which they are used
B. An XML SDK provides both inbound and outbound operations
C. Operations can be reused in recursive calls
D. All operations are public
-
Question 55:
Which statement is true about using mutual TLS to secure an application?
A. Mutual TLS requires a hardware security module to be used
B. Mutual TLS authenticates the identity of the server before the identity of the client
C. Mutual TLS ensures only authorized end users are allowed to access an endpoint
D. Mutual TLS increases the encryption strength versus server-side TLS alone
-
Question 56:
When implementing a synchronous API where the event source is an HTTP Listener, a developer needs to return the same correlation ID back to the caller in the HTTP response header. How can this be achieved?
A. Enable the auto-generate CorrelationID option when scaffolding the flow
B. Enable the CorrelationID checkbox in the HTTP Listener configuration
C. Configure a custom correlation policy
D. NO action is needed as the correlation ID is returned to the caller in the response header by default
-
Question 57:
A custom policy needs to be developed to intercept all cutbound HTTP requests made by Mule applications. Which XML element must be used to intercept outbound HTTP requests?
A. It is not possible to intercept outgoing HTTP requests, only inbound requests
B. http-policy:source
C. htt-policy:operation
D. http-policy:processor
-
Question 58:
An API has been built to enable scheduling email provider. The front-end system does very little data entry validation, and problems have started to appear in the email that go to patients. A validatecustomer'' flow is added validate the data.
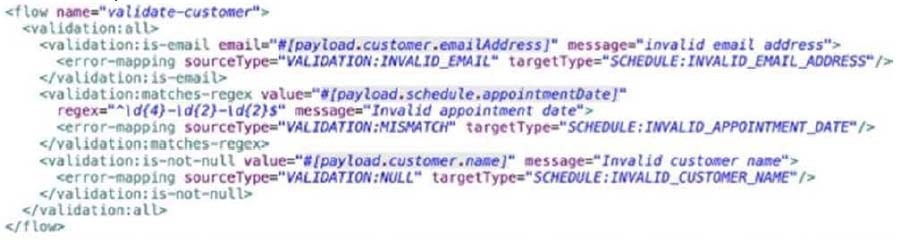
What is he expected behavior of the "validate-customer'' flow?
A. If only the email address Is invalid a VALIDATION.INVALID_EMAIL error is raised
B. If the email address is invalid, processing continues to see if the appointment data and customer name are also invalid
C. If the appointment date and customer name are invalid, a SCHEDULE:INVALID_APPOINTMENT_DATE error is raised
D. If all of the values are invalid the last validation error is raised:SCHEDULE:INVALID_CUSTOMER_NAME
-
Question 59:
The flow is invoicing a target API. The API's protocol is HTTPS. The TLS configuration in the HTTP Request Configuration global element is set to None. A web client submits a request to http:localhost:8081/vehicles. If the certificate of the target API is signed by a certificate authority (CA), what is true about the HTTP Request operation when the flow executes?
A. The HTTP Request operation will succeed if the CA'S certificate is present in the JRE's default keystore
B. The HTTP Request operation will succeed if the CA's certificate is present in the JRE's default truststore.
C. The HTTP Request operation will always succeed regardless of the CA
D. The HTTP Request operation will always fail regardless of the CA
-
Question 60:
When a client and server are exchanging messages during the mTLS handshake, what is being agreed on during the cipher suite exchange?
A. A protocol
B. The TLS version
C. An encryption algorithm
D. The Public key format
Related Exams:
201-COMMERCIAL-BANKING-FUNCTIONAL
Salesforce enCino 201 Commercial Banking FunctionalADM-201
Administration Essentials for New AdminsADM-211
Administration Essentials for Experienced AdminADVANCED-ADMINISTRATOR
Salesforce Certified Advanced AdministratorADVANCED-CROSS-CHANNEL
Salesforce Advanced Cross Channel Accredited ProfessionalADX-201
Administrative Essentials for New Admins in Lightning ExperienceADX-271
Salesforce Certified Community Cloud ConsultantAGENTFORCE-SPECIALIST
Salesforce Certified Agentforce SpecialistANC-301
Working with Data and Dashboards in Einstein AnalyticsB2B-COMMERCE-ADMINISTRATOR
Salesforce Accredited B2B Commerce Administrator
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Salesforce exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your SALESFORCE-MULESOFT-DEVELOPER-II exam preparations and Salesforce certification application, do not hesitate to visit our Vcedump.com to find your solutions here.