Exam Details
Exam Code
:PT1-002Exam Name
:CompTIA PenTest+ Certification ExamCertification
:CompTIA PenTest+Vendor
:CompTIATotal Questions
:131 Q&AsLast Updated
:May 06, 2025
CompTIA CompTIA PenTest+ PT1-002 Questions & Answers
-
Question 71:
A penetration tester has completed an analysis of the various software products produced by the company under assessment. The tester found that over the past several years the company has been including vulnerable third-party modules in multiple products, even though the quality of the organic code being developed is very good. Which of the following recommendations should the penetration tester include in the report?
A. Add a dependency checker into the tool chain.
B. Perform routine static and dynamic analysis of committed code.
C. Validate API security settings before deployment.
D. Perform fuzz testing of compiled binaries.
-
Question 72:
A penetration tester wants to identify CVEs that can be leveraged to gain execution on a Linux server that has an SSHD running. Which of the following would BEST support this task?
A. Run nmap with the –o, -p22, and –sC options set against the target
B. Run nmap with the –sV and –p22 options set against the target
C. Run nmap with the --script vulners option set against the target
D. Run nmap with the –sA option set against the target
-
Question 73:
A penetration tester needs to perform a test on a finance system that is PCI DSS v3.2.1 compliant. Which of the following is the MINIMUM frequency to complete the scan of the system?
A. Weekly
B. Monthly
C. Quarterly
D. Annually
-
Question 74:
A company becomes concerned when the security alarms are triggered during a penetration test. Which of the following should the company do NEXT?
A. Halt the penetration test.
B. Conduct an incident response.
C. Deconflict with the penetration tester.
D. Assume the alert is from the penetration test.
-
Question 75:
A company is concerned that its cloud VM is vulnerable to a cyberattack and proprietary data may be stolen. A penetration tester determines a vulnerability does exist and exploits the vulnerability by adding a fake VM instance to the IaaS component of the client's VM. Which of the following cloud attacks did the penetration tester MOST likely implement?
A. Direct-to-origin
B. Cross-site scripting
C. Malware injection
D. Credential harvesting
-
Question 76:
A penetration tester is looking for a vulnerability that enables attackers to open doors via a specialized TCP service that is used for a physical access control system. The service exists on more than 100 different hosts, so the tester would like to automate the assessment. Identification requires the penetration tester to:
Have a full TCP connection Send a "hello" payload Walt for a response Send a string of characters longer than 16 bytes
Which of the following approaches would BEST support the objective?
A. Run nmap –Pn –sV –script vuln
. B. Employ an OpenVAS simple scan against the TCP port of the host.
C. Create a script in the Lua language and use it with NSE.
D. Perform a credentialed scan with Nessus.
-
Question 77:
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:
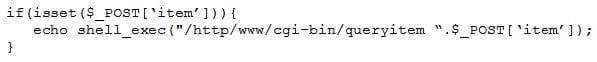
Which of the following tools will help the tester prepare an attack for this scenario?
A. Hydra and crunch
B. Netcat and cURL
C. Burp Suite and DIRB
D. Nmap and OWASP ZAP
-
Question 78:
Which of the following would MOST likely be included in the final report of a static application-security test that was written with a team of application developers as the intended audience?
A. Executive summary of the penetration-testing methods used
B. Bill of materials including supplies, subcontracts, and costs incurred during assessment
C. Quantitative impact assessments given a successful software compromise
D. Code context for instances of unsafe type-casting operations
-
Question 79:
Which of the following should a penetration tester do NEXT after identifying that an application being tested has already been compromised with malware?
A. Analyze the malware to see what it does.
B. Collect the proper evidence and then remove the malware.
C. Do a root-cause analysis to find out how the malware got in.
D. Remove the malware immediately.
E. Stop the assessment and inform the emergency contact.
-
Question 80:
A penetration tester runs the following command on a system:
find / -user root –perm -4000 –print 2>/dev/null
Which of the following is the tester trying to accomplish?
A. Set the SGID on all files in the / directory
B. Find the /root directory on the system
C. Find files with the SUID bit set
D. Find files that were created during exploitation and move them to /dev/null
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT1-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.