Exam Details
Exam Code
:PT1-002Exam Name
:CompTIA PenTest+ Certification ExamCertification
:CompTIA PenTest+Vendor
:CompTIATotal Questions
:131 Q&AsLast Updated
:May 06, 2025
CompTIA CompTIA PenTest+ PT1-002 Questions & Answers
-
Question 91:
A penetration tester was conducting a penetration test and discovered the network traffic was no longer reaching the client's IP address. The tester later discovered the SOC had used sinkholing on the penetration tester's IP address. Which of the following BEST describes what happened?
A. The penetration tester was testing the wrong assets
B. The planning process failed to ensure all teams were notified
C. The client was not ready for the assessment to start
D. The penetration tester had incorrect contact information
-
Question 92:
A penetration tester wants to perform reconnaissance without being detected. Which of the following activities have a MINIMAL chance of detection? (Choose two.)
A. Open-source research
B. A ping sweep
C. Traffic sniffing
D. Port knocking
E. A vulnerability scan
F. An Nmap scan
-
Question 93:
A penetration tester is testing input validation on a search form that was discovered on a website. Which of the following characters is the BEST option to test the website for vulnerabilities?
A. Comma
B. Double dash
C. Single quote
D. Semicolon
-
Question 94:
Appending string values onto another string is called:
A. compilation
B. connection
C. concatenation
D. conjunction
-
Question 95:
Given the following output:
User-agent:* Disallow: /author/ Disallow: /xmlrpc.php Disallow: /wp-admin Disallow: /page/
During which of the following activities was this output MOST likely obtained?
A. Website scraping
B. Website cloning
C. Domain enumeration
D. URL enumeration
-
Question 96:
A security engineer identified a new server on the network and wants to scan the host to determine if it is running an approved version of Linux and a patched version of Apache. Which of the following commands will accomplish this task?
A. nmap –f –sV –p80 192.168.1.20
B. nmap –sS –sL –p80 192.168.1.20
C. nmap –A –T4 –p80 192.168.1.20
D. nmap –O –v –p80 192.168.1.20
-
Question 97:
Which of the following expressions in Python increase a variable val by one (Choose two.)
A. val++
B. +val
C. val=(val+1)
D. ++val
E. val=val++
F. val+=1
-
Question 98:
A penetration tester has been contracted to review wireless security. The tester has deployed a malicious wireless AP that mimics the configuration of the target enterprise WiFi. The penetration tester now wants to try to force nearby wireless stations to connect to the malicious AP. Which of the following steps should the tester take NEXT?
A. Send deauthentication frames to the stations.
B. Perform jamming on all 2.4GHz and 5GHz channels.
C. Set the malicious AP to broadcast within dynamic frequency selection channels.
D. Modify the malicious AP configuration to not use a pre-shared key.
-
Question 99:
A penetration tester conducted a discovery scan that generated the following:
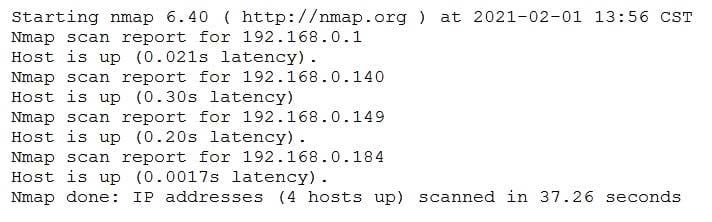
Which of the following commands generated the results above and will transform them into a list of active hosts for further analysis?
A. nmap –oG list.txt 192.168.0.1-254 , sort
B. nmap –sn 192.168.0.1-254 , grep “Nmap scan” | awk ‘{print S5}’
C. nmap –-open 192.168.0.1-254, uniq
D. nmap –o 192.168.0.1-254, cut –f 2
-
Question 100:
Which of the following BEST describe the OWASP Top 10? (Choose two.)
A. The most critical risks of web applications
B. A list of all the risks of web applications
C. The risks defined in order of importance
D. A web-application security standard
E. A risk-governance and compliance framework
F. A checklist of Apache vulnerabilities
Related Exams:
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT1-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.