Exam Details
Exam Code
:PT1-002Exam Name
:CompTIA PenTest+ Certification ExamCertification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:131 Q&AsLast Updated
:Jul 06, 2025
CompTIA CompTIA Certifications PT1-002 Questions & Answers
-
Question 1:
An attacker performed a MITM attack against a mobile application. The attacker is attempting to manipulate the application's network traffic via a proxy tool. The attacker only sees limited traffic as cleartext. The application log files indicate secure SSL/TLS connections are failing. Which of the following is MOST likely preventing proxying of all traffic?
A. Misconfigured routes
B. Certificate pinning
C. Strong cipher suites
D. Closed ports
-
Question 2:
A penetration tester has been hired to perform a penetration test for an organization. Which of the following is indicative of an error-based SQL injection attack?
A. a=1 or 1
B. 1=1 or b
C. 1=1 or 2
D. 1=1 or a
-
Question 3:
A penetration tester is testing a web application and is logged in as a lower-privileged user. The tester runs arbitrary JavaScript within an application, which sends an XMLHttpRequest, resulting in exploiting features to which only an administrator should have access. Which of the following controls would BEST mitigate the vulnerability?
A. Implement authorization checks.
B. Sanitize all the user input.
C. Prevent directory traversal.
D. Add client-side security controls
-
Question 4:
During a penetration test, a tester identifies traditional antivirus running on the exploited server. Which of the following techniques would BEST ensure persistence in a post-exploitation phase?
A. Shell binary placed in C:\windows\temp
B. Modified daemons
C. New user creation
D. Backdoored executables
-
Question 5:
When negotiating a penetration testing contract with a prospective client, which of the following disclaimers should be included in order to mitigate liability in case of a future breach of the client's systems?
A. The proposed mitigations and remediations in the final report do not include a cost-benefit analysis.
B. The NDA protects the consulting firm from future liabilities in the event of a breach.
C. The assessment reviewed the cyber key terrain and most critical assets of the client's network.
D. The penetration test is based on the state of the system and its configuration at the time of assessment.
-
Question 6:
A security team is switching firewall vendors. The director of security wants to scope a penetration test to satisfy requirements to perform the test after major architectural changes. Which of the following is the BEST way to approach the project?
A. Design a penetration test approach, focusing on publicly released firewall DoS vulnerabilities.
B. Review the firewall configuration, followed by a targeted attack by a read team.
C. Perform a discovery scan to identify changes in the network.
D. Focus on an objective-based approach to assess network assets with a red team.
-
Question 7:
A penetration tester must assess a web service. Which of the following should the tester request during the scoping phase?
A. XSD
B. After-hours contact escalation
C. WSDLfile
D. SOAP project file
-
Question 8:
Joe, a penetration tester, was able to exploit a web application behind a firewall He is trying to get a reverse shell back to his machine but the firewall blocks the outgoing traffic Ports for which of the following should the security consultant use to have the HIGHEST chance to bypass the firewall?
A. HTTP
B. SMTP
C. FTP
D. DNS
-
Question 9:
A penetration tester has obtained access to an IP network subnet that contains ICS equipment intercommunication. Which of the following attacks is MOST likely to succeed in creating a physical effect?
A. DNS cache poisoning
B. Record and replay
C. Supervisory server SMB
D. Blind SQL injection
-
Question 10:
During an internal network penetration test the tester is able to compromise a Windows system and recover the NTLM hash for a local wrltsrnAdrain account Attempting to recover the plaintext password by cracking the hash has proved to be unsuccessful, and the tester has decided to try a pass-the-hash attack to see if the credentials are reused on other in-scope systems Using the Medusa tool the tester attempts to authenticate to a list of systems, including the originally compromised host, with no success Given the output below:
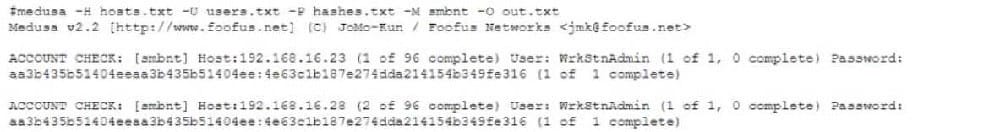
Which of the following Medusa commands would potentially provide better results?
A. #medusa -h hosts.txt -U usera.txt -P hashes, txt -M smbnt. -m GROP:LOCAL -O out.txt -m PASS:HASH
B. #medusa -H hosts.txt -U users, txt -P hashes, txt -M smbnt -m PASS:HASH -o out. txt
C. #medusa -H hosts.txt -u WrkStnAdmin -paa3b435b51404eeaa3b435b51404ee:4e63c1b137e274dda214154b349fe316 -M smbnt -m GROUP:DOMAIN -o out.txt
D. #medusa -H hosts.txt -C creds.txt -M mssq1 -m GROUP: DOMAIN -o out.txt
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT1-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.