Exam Details
Exam Code
:PT1-002Exam Name
:CompTIA PenTest+ Certification ExamCertification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:131 Q&AsLast Updated
:Jul 06, 2025
CompTIA CompTIA Certifications PT1-002 Questions & Answers
-
Question 51:
Running a vulnerability scanner on a hybrid network segment that includes general IT servers and industrial control systems:
A. will reveal vulnerabilities in the Modbus protocol.
B. may cause unintended failures in control systems.
C. may reduce the true positive rate of findings.
D. will create a denial-of-service condition on the IP networks.
-
Question 52:
An Nmap network scan has found five open ports with identified services. Which of the following tools should a penetration tester use NEXT to determine if any vulnerabilities with associated exploits exist on the open ports?
A. OpenVAS
B. Drozer
C. Burp Suite
D. OWASP ZAP
-
Question 53:
In the process of active service enumeration, a penetration tester identifies an SMTP daemon running on one of the target company's servers. Which of the following actions would BEST enable the tester to perform phishing in a later stage of the assessment?
A. Test for RFC-defined protocol conformance.
B. Attempt to brute force authentication to the service.
C. Perform a reverse DNS query and match to the service banner.
D. Check for an open relay configuration.
-
Question 54:
A red team gained access to the internal network of a client during an engagement and used the Responder tool to capture important data. Which of the following was captured by the testing team?
A. Multiple handshakes
B. IP addresses
C. Encrypted file transfers
D. User hashes sent over SMB
-
Question 55:
A penetration tester runs a scan against a server and obtains the following output:
21/tcp open ftp Microsoft ftpd | ftp-anon: Anonymous FTP login allowed (FTP code 230) | 03-12-20 09:23AM 331 index.aspx | ftp-syst: 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows Server 2012 Std 3389/tcp open ssl/ms-wbt-server | rdp-ntlm-info: | Target Name: WEB3 | NetBIOS_Computer_Name: WEB3 | Product_Version: 6.3.9600 |_ System_Time: 2021-01-15T11:32:06+00:00 8443/tcp open http Microsoft IIS httpd 8.5 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/8.5 |_http-title: IIS Windows Server
Which of the following command sequences should the penetration tester try NEXT?
A. ftp 192.168.53.23
B. smbclient \\\\WEB3\\IPC$ -I 192.168.53.23 –U guest
C. ncrack –u Administrator –P 15worst_passwords.txt –p rdp 192.168.53.23
D. curl –X TRACE https://192.168.53.23:8443/index.aspx
E. nmap –-script vuln –sV 192.168.53.23
-
Question 56:
A penetration tester has been hired to configure and conduct authenticated scans of all the servers on a software company's network. Which of the following accounts should the tester use to return the MOST results?
A. Root user
B. Local administrator
C. Service
D. Network administrator
-
Question 57:
User credentials were captured from a database during an assessment and cracked using rainbow tables. Based on the ease of compromise, which of the following algorithms was MOST likely used to store the passwords in the database?
A. MD5
B. bcrypt
C. SHA-1
D. PBKDF2
-
Question 58:
A penetration tester recently performed a social-engineering attack in which the tester found an employee of the target company at a local coffee shop and over time built a relationship with the employee. On the employee's birthday, the tester gave the employee an external hard drive as a gift. Which of the following social-engineering attacks was the tester utilizing?
A. Phishing
B. Tailgating
C. Baiting
D. Shoulder surfing
-
Question 59:
A penetration tester runs the unshadow command on a machine. Which of the following tools will the tester most likely use NEXT?
A. John the Ripper
B. Hydra
C. Mimikatz
D. Cain and Abel
-
Question 60:
A penetration tester performs the following command:
curl –I –http2 https://www.comptia.org
Which of the following snippets of output will the tester MOST likely receive?
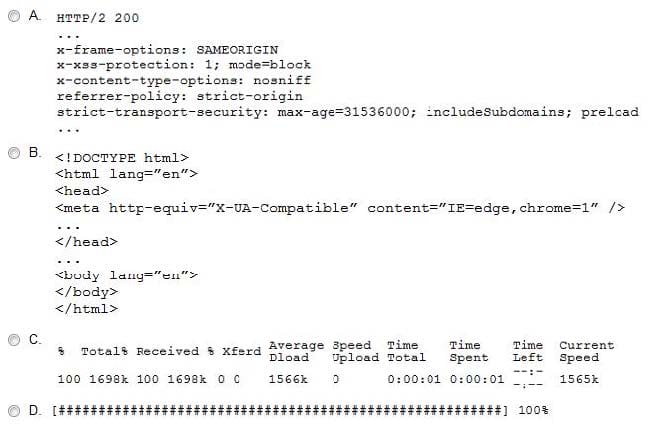
A. Option A
B. Option B
C. Option C
D. Option D
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT1-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.