Exam Details
Exam Code
:PCNSE8Exam Name
:Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 8.0Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:255 Q&AsLast Updated
:Jun 11, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE8 Questions & Answers
-
Question 131:
Which three authentication factors does PAN-OS?software support for MFA (Choose three.)
A. Push
B. Pull
C. Okta Adaptive
D. Voice
E. SMS
-
Question 132:
VPN traffic intended for an administrator's Palo Alto Networks NGFW is being maliciously intercepted and retransmitted by the interceptor. When creating a VPN tunnel, which protection profile can be enabled to prevent this malicious behavior?
A. Zone Protection
B. Replay
C. Web Application
D. DoS Protection
-
Question 133:
A customer wants to combine multiple Ethernet interfaces into a single virtual interface using link aggregation. Which two formats are correct for naming aggregate interfaces? (Choose two.)
A. ae.8
B. aggregate.1
C. ae.1
D. aggregate.8
-
Question 134:
Which prerequisite must be satisfied before creating an SSH proxy Decryption policy?
A. Both SSH keys and SSL certificates must be generated.
B. No prerequisites are required.
C. SSH keys must be manually generated.
D. SSL certificates must be generated.
-
Question 135:
What is exchanged through the HA2 link?
A. hello heartbeats
B. User-ID information
C. session synchronization
D. HA state information
-
Question 136:
Which three user authentication services can be modified to provide the Palo Alto Networks NGFW with both usernames and role names? (Choose three.)
A. TACACS+
B. Kerberos
C. PAP
D. LDAP
E. SAML
F. RADIUS
-
Question 137:
View the GlobalProtect configuration screen capture. What is the purpose of this configuration?
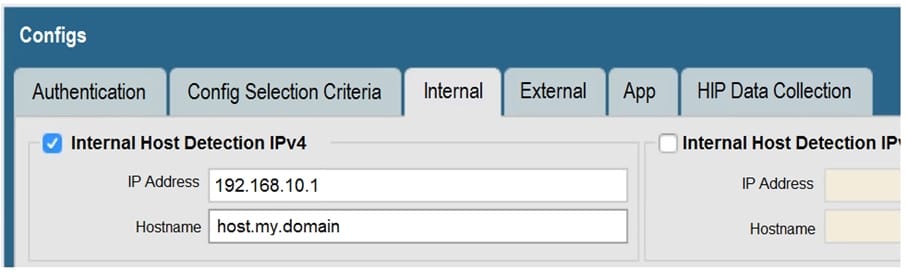
A. It configures the tunnel address of all internal clients to an IP address range starting at 192.168.10.1.
B. It forces an internal client to connect to an internal gateway at IP address 192.168.10.1.
C. It enables a client to perform a reverse DNS lookup on 192.168.10.1 to detect that it is an internal client.
D. It forces the firewall to perform a dynamic DNS update, which adds the internal gateway's hostname and IP address to the DNS server.
-
Question 138:
Which two subscriptions are available when configuring panorama to push dynamic updates to connected devices? (Choose two.)
A. Content-ID
B. User-ID
C. Applications and Threats
D. Antivirus
-
Question 139:
Which DoS protection mechanism detects and prevents session exhaustion attacks?
A. Packet Based Attack Protection
B. Flood Protection
C. Resource Protection
D. TCP Port Scan Protection
-
Question 140:
Which CLI command enables an administrator to check the CPU utilization of the dataplane?
A. show running resource-monitor
B. debug data-plane dp-cpu
C. show system resources
D. debug running resources
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)PCNSC
Palo Alto Networks Certified Network Security Consultant (PCNSC)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE8 exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.