Exam Details
Exam Code
:PCNSE8Exam Name
:Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 8.0Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:255 Q&AsLast Updated
:Jun 11, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE8 Questions & Answers
-
Question 151:
Which two options prevent the firewall from capturing traffic passing through it? (Choose two.)
A. The firewall is in multi-vsys mode.
B. The traffic is offloaded.
C. The traffic does not match the packet capture filter.
D. The firewall's DP CPU is higher than 50%.
-
Question 152:
A web server is hosted in the DMZ and the server is configured to listen for incoming connections on TCP port 443. A Security policies rules allowing access from the Trust zone to the DMZ zone needs to be configured to allow web-browsing
access. The web server hosts its contents over HTTP(S). Traffic from Trust to DMZ is being decrypted with a Forward Proxy rule.
Which combination of service and application, and order of Security policy rules, needs to be configured to allow cleartext web- browsing traffic to this server on tcp/443?
A. Rule #1: application: web-browsing; service: application-default; action: allow Rule #2: application: ssl; service: application-default; action: allow
B. Rule #1: application: web-browsing; service: service-https; action: allow Rule #2: application: ssl; service: application-default; action: allow
C. Rule # 1: application: ssl; service: application-default; action: allow Rule #2: application: web-browsing; service: application-default; action: allow
D. Rule #1: application: web-browsing; service: service-http; action: allow Rule #2: application: ssl; service: application-default; action: allow
-
Question 153:
Refer to the exhibit. A web server in the DMZ is being mapped to a public address through DNAT.
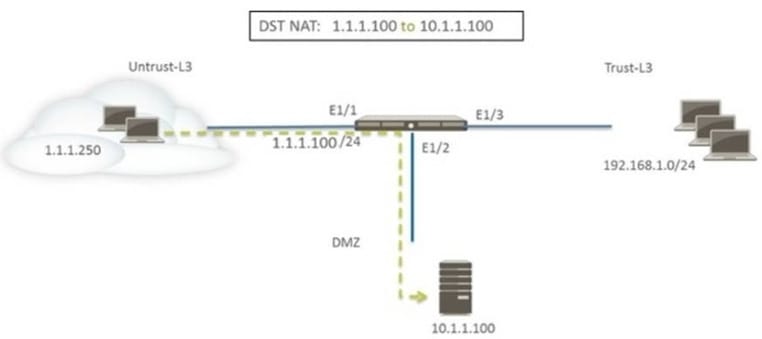
Which Security policy rule will allow traffic to flow to the web server?
A. Untrust (any) to Untrust (10. 1.1. 100), web browsing -Allow
B. Untrust (any) to Untrust (1. 1. 1. 100), web browsing -Allow
C. Untrust (any) to DMZ (1. 1. 1. 100), web browsing -Allow
D. Untrust (any) to DMZ (10. 1. 1. 100), web browsing -Allow
-
Question 154:
Exhibit:
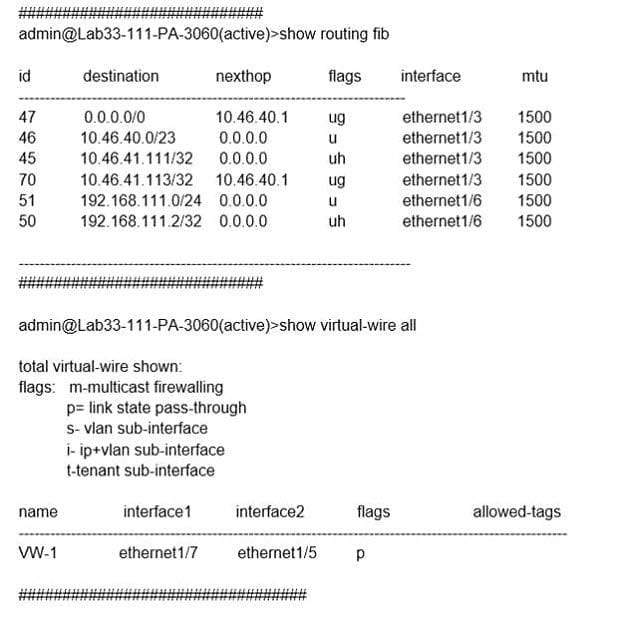
What will be the egress interface if the traffic's ingress interface is ethernet1/6 sourcing from 192.168.111.3 and to the destination 10.46.41.113 during the time shown in the image?
A. ethernet1/7
B. ethernet1/5
C. ethernet1/6
D. ethernet1/3
-
Question 155:
Which processing order will be enabled when a Panorama administrator selects the setting "Objects defined in ancestors will take higher precedence?"
A. Descendant objects will take precedence over other descendant objects.
B. Descendant objects will take precedence over ancestor objects.
C. Ancestor objects will have precedence over descendant objects.
D. Ancestor objects will have precedence over other ancestor objects.
-
Question 156:
An administrator using an enterprise PKI needs to establish a unique chain of trust to ensure mutual authentication between Panorama and the managed firewalls and Log Collectors. How would the administrator establish the chain of trust?
A. Use custom certificates
B. Enable LDAP or RADIUS integration
C. Set up multi-factor authentication
D. Configure strong password authentication
-
Question 157:
An administrator has been asked to configure a Palo Alto Networks NGFW to provide protection against external hosts attempting to exploit a flaw in an operating system on an internal system.
Which Security Profile type will prevent this attack?
A. Vulnerability Protection
B. Anti-Spyware
C. URL Filtering
D. Antivirus
-
Question 158:
An administrator has created an SSL Decryption policy rule that decrypts SSL sessions on any port. Which log entry can the administrator use to verify that sessions are being decrypted?
A. In the details of the Traffic log entries
B. Decryption log
C. Data Filtering log
D. In the details of the Threat log entries
-
Question 159:
When is the content inspection performed in the packet flow process?
A. after the application has been identified
B. before session lookup
C. before the packet forwarding process
D. after the SSL Proxy re-encrypts the packet
-
Question 160:
Which virtual router feature determines if a specific destination IP address is reachable?
A. Heartbeat Monitoring
B. Failover
C. Path Monitoring
D. Ping-Path
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)PCNSC
Palo Alto Networks Certified Network Security Consultant (PCNSC)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE8 exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.