Exam Details
Exam Code
:PCNSE8Exam Name
:Palo Alto Networks Certified Security Engineer (PCNSE) PAN-OS 8.0Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:255 Q&AsLast Updated
:Jun 11, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE8 Questions & Answers
-
Question 11:
A company hosts a publicly accessible web server behind a Palo Alto Networks next-generation firewall with the following configuration information:
*
Users outside the company are in the "Untrust-L3" zone.
*
The web server physically resides in the "Trust-L3" zone.
*
Web server public IP address: 23.54.6.10
*
Web server private IP address: 192.168.1.10
Which two items must the NAT policy contain to allow users in the Untrust-L3 zone to access the web server? (Choose two.)
A. Destination IPof 23.54.6.10
B. UntrustL3 for both Source and Destination Zone
C. Destination IP of 192.168.1.10
D. UntrustL3 for Source Zone and Trust-L3 for Destination Zone
-
Question 12:
In an enterprise deployment, a network security engineer wants to assign to a group of administrators without creating local administrator accounts on the firewall. Which authentication method must be used?
A. LDAP
B. Kerberos
C. Certification based authentication
D. RADIUS with Vendor-Specific Attributes
-
Question 13:
Which two logs on the firewall will contain authentication-related information useful for troubleshooting purpose (Choose two)
A. ms.log
B. traffic.log
C. system.log
D. dp-monitor.log
E. authd.log
-
Question 14:
When a malware-infected host attempts to resolve a known command-and-control server, the traffic matches a security policy with DNS sinhole enabled, generating a traffic log. What will be the destination IP Address in that log entry?
A. The IP Address of sinkhole.paloaltonetworks.com
B. The IP Address of the command-and-control server
C. The IP Address specified in the sinkhole configuration
D. The IP Address of one of the external DNS servers identified in the anti-spyware database
-
Question 15:
Which CLI command displays the current management plane memory utilization?
A. > debug management-server show
B. > show running resource-monitor
C. > show system info
D. > show system resources
-
Question 16:
A network security engineer needs to configure a virtual router using IPv6 addresses. Which two routing options support these addresses? (Choose two)
A. BGP not sure
B. OSPFv3
C. RIP
D. Static Route
-
Question 17:
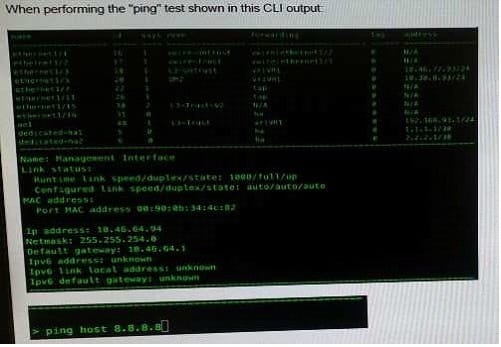
What will be the source address in the ICMP packet?
A. 10.30.0.93
B. 10.46.72.93
C. 10.46.64.94
D. 192.168.93.1
-
Question 18:
A file sharing application is being permitted and no one knows what this application is used for. How should this application be blocked?
A. Block all unauthorized applications using a security policy
B. Block all known internal custom applications
C. Create a WildFire Analysis Profile that blocks Layer 4 and Layer 7 attacks
D. Create a File blocking profile that blocks Layer 4 and Layer 7 attacks
-
Question 19:
Which three rule types are available when defining policies in Panorama? (Choose three.)
A. Pre Rules
B. Post Rules
C. Default Rules
D. Stealth Rules
E. Clean Up Rules
-
Question 20:
Which CLI command displays the current management plan memory utilization?
A. > show system info
B. > show system resources
C. > debug management-server show
D. > show running resource-monitor
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)PCNSC
Palo Alto Networks Certified Network Security Consultant (PCNSC)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE8 exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.