Exam Details
Exam Code
:PCNSEExam Name
:Palo Alto Networks Certified Network Security Engineer - PAN-OS 11.x (PCNSE)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:860 Q&AsLast Updated
:Aug 19, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE Questions & Answers
-
Question 281:
A network administrator is troubleshooting an issue with Phase 2 of an IPSec VPN tunnel. The administrator determines that the lifetime needs to be changed to match the peer. Where should this change be made?
A. IKE Gateway profile
B. IPSec Crypto profile
C. IPSec Tunnel settings
D. IKE Crypto profile
-
Question 282:
An engineer needs to collect User-ID mappings from the company's existing proxies.
What two methods can be used to pull this data from third party proxies? (Choose two.)
A. Syslog
B. XFF Headers
C. Client probing
D. Server Monitoring
-
Question 283:
A network engineer is troubleshooting a VPN and wants to verify whether the decapsulation/encapsulation counters are increasing. Which CLI command should the engineer run?
A. Show vpn tunnel name | match encap
B. Show vpn flow name
C. Show running tunnel flow lookup
D. Show vpn ipsec-sa tunnel
-
Question 284:
Refer to the exhibit.
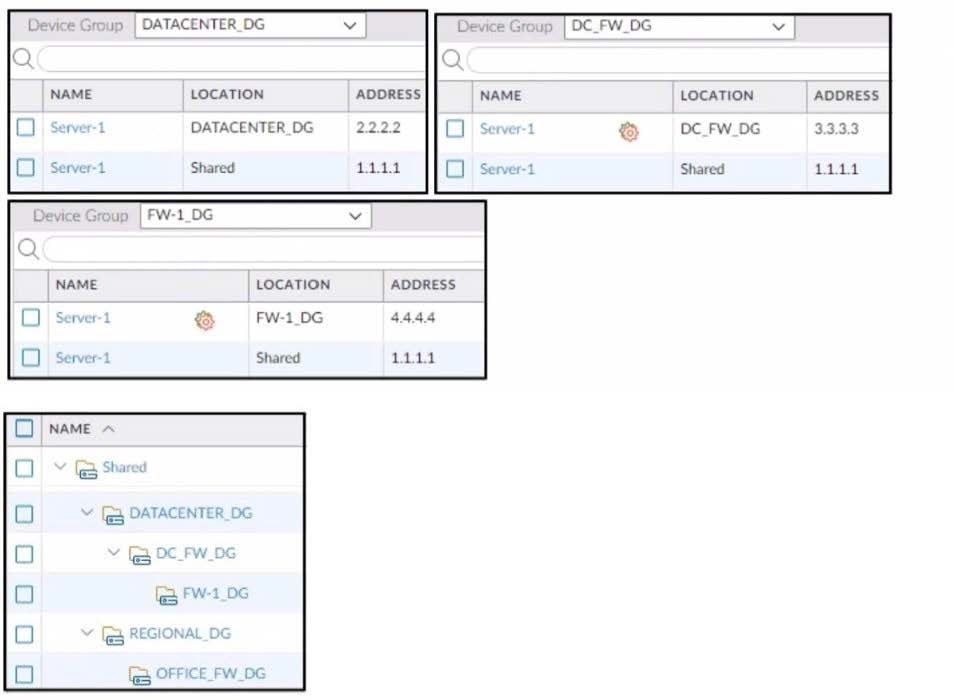
Review the screenshots and consider the following information:
1.
FW-1 is assigned to the FW-1_DG device group, and FW-2 is assigned to OFFICE_FW_DG.
2.
There are no objects configured in REGIONAL_DG and OFFICE_FW_DG device groups. Which IP address will be pushed to the firewalls inside Address Object Server-1?
A. Server-1 on FW-1 will have IP 1.1.1.1. Server-1 will not be pushed to FW-2.
B. Server-1 on FW-1 will have IP 3.3.3.3. Server-1 will not be pushed to FW-2.
C. Server-1 on FW-1 will have IP 2.2.2.2. Server-1 will not be pushed to FW-2.
D. Server-1 on FW-1 will have IP 4.4.4.4. Server-1 on FW-2 will have IP 1.1.1.1.
-
Question 285:
A system administrator runs a port scan using the company tool as part of vulnerability check. The administrator finds that the scan is identified as a threat and is dropped by the firewall. After further investigating the logs, the administrator finds that the scan is dropped in the Threat Logs.
What should the administrator do to allow the tool to scan through the firewall?
A. Remove the Zone Protection profile from the zone setting.
B. Add the tool IP address to the reconnaissance protection source address exclusion in the Zone Protection profile.
C. Add the tool IP address to the reconnaissance protection source address exclusion in the DoS Protection profile.
D. Change the TCP port scan action from Block to Alert in the Zone Protection profile.
-
Question 286:
What is the dependency for users to access services that require authentication?
A. An Authentication profile that includes those services
B. Disabling the authentication timeout
C. An authentication sequence that includes those services
D. A Security policy allowing users to access those services
-
Question 287:
An administrator is using Panorama to manage me and suspects an IKE Crypto mismatch between peers, from the firewalls to Panorama. However, pre-existing logs from the firewalls are not appearing in Panorama. Which action should be taken to enable the firewalls to send their pre-existing logs to Panorama?
A. Export the log database.
B. Use the import option to pull logs.
C. Use the ACC to consolidate the logs.
D. Use the scp logdb export command.
-
Question 288:
An engineer needs to configure SSL Forward Proxy to decrypt traffic on a PA-5260. The engineer uses a forward trust certificate from the enterprise PKI that expires December 31, 2025. The validity date on the PA-generated certificate is taken from what?
A. The trusted certificate
B. The server certificate
C. The untrusted certificate
D. The root CA
-
Question 289:
An engineer has been given approval to upgrade their environment 10 PAN-OS 10 2 The environment consists of both physical and virtual firewalls a virtual Panorama HA pair, and virtual log collectors
What is the recommended order when upgrading to PAN-OS 10.2?
A. Upgrade Panorama, upgrade the log collectors, upgrade the firewalls
B. Upgrade the firewalls upgrade log collectors, upgrade Panorama
C. Upgrade the firewalls upgrade Panorama, upgrade the log collectors
D. Upgrade the log collectors, upgrade the firewalls, upgrade Panorama
-
Question 290:
An administrator wants to grant read-only access to all firewall settings, except administrator accounts, to a new-hire colleague in the IT department. Which dynamic role does the administrator assign to the new-hire colleague?
A. Device administrator (read-only)
B. System administrator (read-only)
C. Firewall administrator (read-only)
D. Superuser (read-only)
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.