Exam Details
Exam Code
:PCNSEExam Name
:Palo Alto Networks Certified Network Security Engineer - PAN-OS 11.x (PCNSE)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:860 Q&AsLast Updated
:Aug 19, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE Questions & Answers
-
Question 271:
An engineer is bootstrapping a VM-Series Firewall Other than the 'config folder, which three directories are mandatory as part of the bootstrap package directory structure? (Choose three.)
A. /software
B. /opt
C. /license
D. /content
E. /plugins
-
Question 272:
Review the screenshot of the Certificates page.
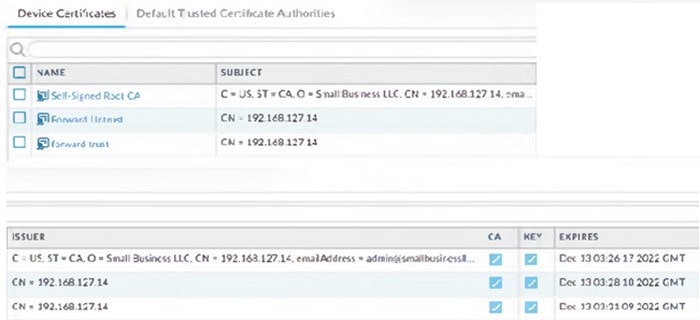
An administrator tor a small LLC has created a series of certificates as shown, to use tor a planned Decryption roll out The administrator has also installed the sell-signed root certificate
A. The forward trust certificate has not been signed by the set-singed root CA certificate
B. The self-signed CA certificate has the same CN as the forward trust and untrust certificates
C. The forward untrust certificate has not been signed by the self-singed root CA certificate
D. The forward trust certificate has not been installed in client systems
-
Question 273:
The decision to upgrade to PAN-OS 10.2 has been approved. The engineer begins the process by upgrading the Panorama servers, but gets an error when trying to install. When performing an upgrade on Panorama to PAN-OS 10.2, what is the potential cause of a failed install?
A. Management only mode
B. Expired certificates
C. Outdated plugins
D. GlobalProtect agent version
-
Question 274:
An engineer is designing a deployment of multi-vsys firewalls.
What must be taken into consideration when designing the device group structure?
A. Multiple vsys and firewalls can be assigned to a device group, and a multi-vsys firewall must have all its vsys in a single device group.
B. Only one vsys or one firewall can be assigned to a device group, except for a multi-vsys firewall, which must have all its vsys in a single device group.
C. Multiple vsys and firewalls can be assigned to a device group, and a multi-vsys firewall can have each vsys in a different device group.
D. Only one vsys or one firewall can be assigned to a device group, and a multi-vsys firewall can have each vsys in a different device group.
-
Question 275:
A network security administrator wants to begin inspecting bulk user HTTPS traffic flows egressing out of the internet edge firewall. Which certificate is the best choice to configure as an SSL Forward Trust certificate?
A. A self-signed Certificate Authority certificate generated by the firewall
B. A Machine Certificate for the firewall signed by the organization's PKI
C. A web server certificate signed by the organization's PKI
D. A subordinate Certificate Authority certificate signed by the organization's PKI
-
Question 276:
After configuring HA in Active/Passive mode on a pair of firewalls the administrator gets a failed commit with the following details.
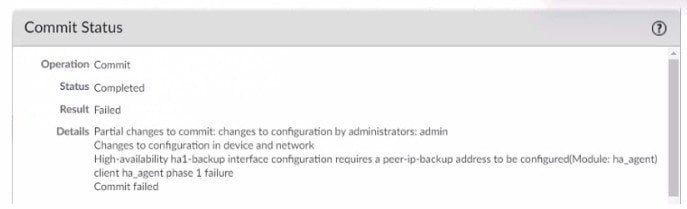
What are two explanations for this type of issue? (Choose two)
A. The peer IP is not included in the permit list on Management Interface Settings
B. The Backup Peer HA1 IP Address was not configured when the commit was issued
C. Either management or a data-plane interface is used as HA1-backup
D. One of the firewalls has gone into the suspended state
-
Question 277:
With the default TCP and UDP settings on the firewall, what will be the identified application in the following session?
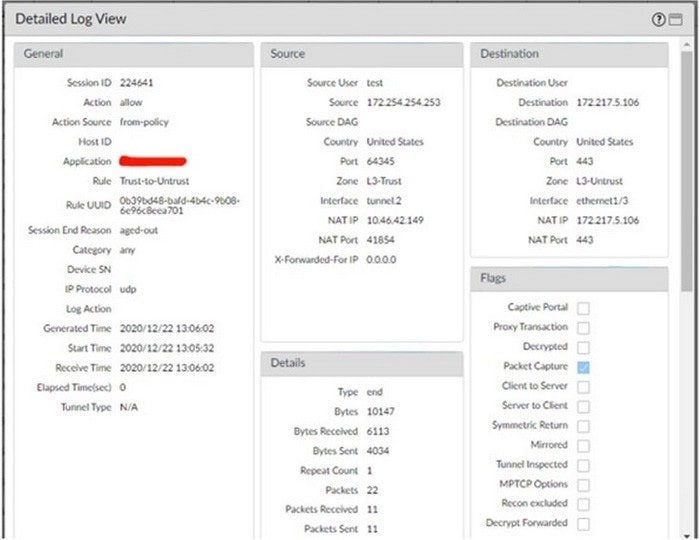
A. Incomplete
B. unknown-udp
C. Insufficient-data
D. not-applicable
-
Question 278:
An administrator creates an application-based security policy rule and commits the change to the firewall. Which two methods should be used to identify the dependent applications for the respective rule? (Choose two.)
A. Use the show predefined xpath
command and review the output. B. Review the App Dependency application list from the Commit Status view.
C. Open the security policy rule and review the Depends On application list.
D. Reference another application group containing similar applications.
-
Question 279:
Refer to the exhibit.
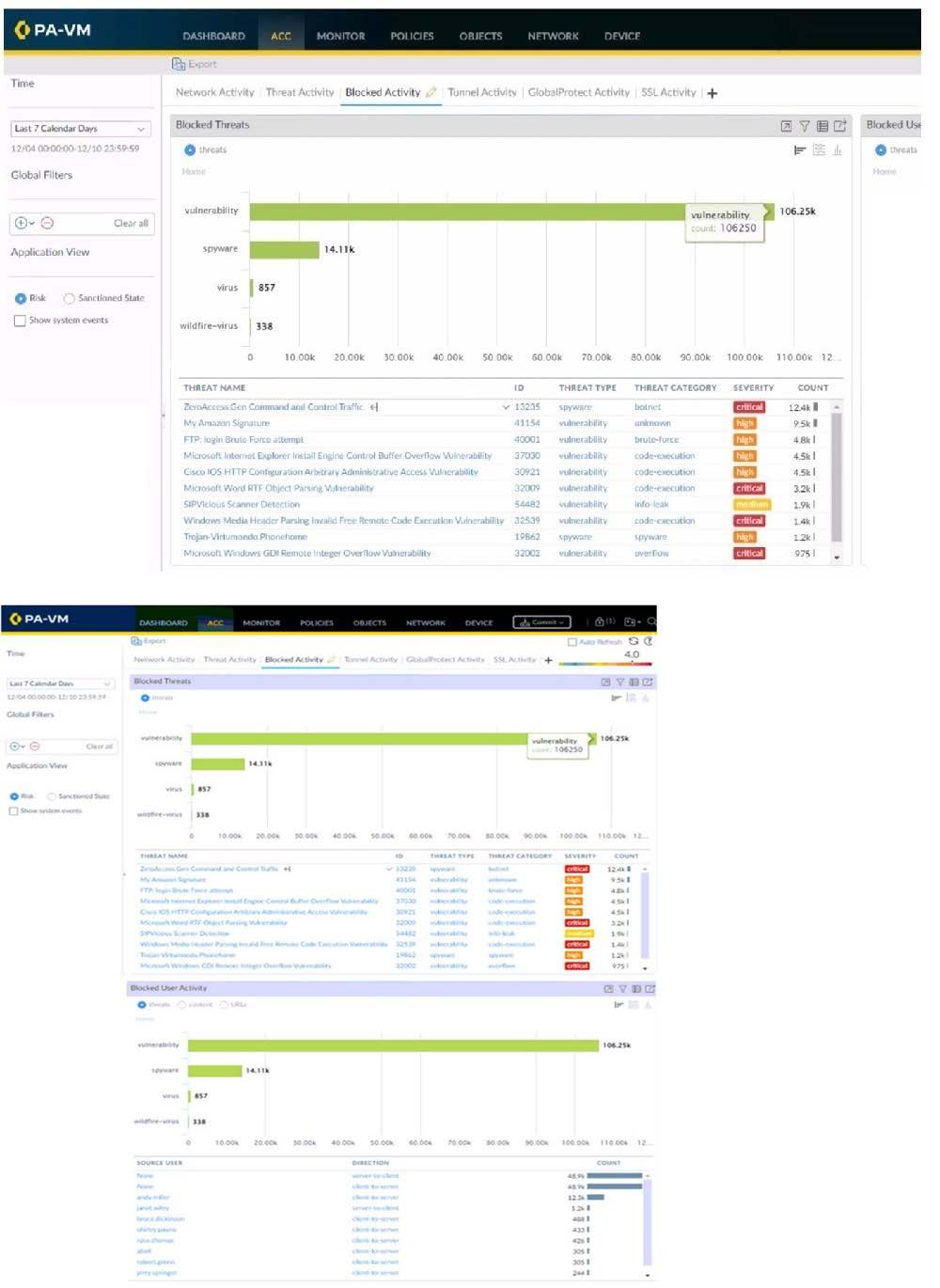
Using the above screenshot of the ACC, what is the best method to set a global filter, narrow down Blocked User Activity, and locate the user(s) that could be compromised by a botnet?
A. Click the hyperlink for the Zero Access.Gen threat.
B. Click the left arrow beside the Zero Access.Gen threat.
C. Click the source user with the highest threat count.
D. Click the hyperlink for the hotport threat Category.
-
Question 280:
Four configuration choices are listed, and each could be used to block access to a specific URL.
If you configured each choice to block the same URL, then which choice would be evaluated last in the processing order to block access to the URL?
A. PAN-DB URL category in URL Filtering profile
B. Custom URL category in Security policy rule
C. Custom URL category in URL Filtering profile
D. EDL in URL Filtering profile
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.