Exam Details
Exam Code
:PCNSEExam Name
:Palo Alto Networks Certified Network Security Engineer - PAN-OS 11.x (PCNSE)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:860 Q&AsLast Updated
:Aug 19, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE Questions & Answers
-
Question 131:
An administrator has a Palo Alto Networks NGFW. All security subscriptions and decryption are enabled and the system is running close to its resource limits.
Knowing that using decryption can be resource-intensive, how can the administrator reduce the load on the firewall?
A. Use SSL Forward Proxy instead of SSL Inbound Inspection for decryption.
B. Use RSA instead of ECDSA for traffic that isn't sensitive or high-priority.
C. Use the highest TLS protocol version to maximize security.
D. Use ECDSA instead of RSA for traffic that isn't sensitive or high-priority.
-
Question 132:
A root cause analysis investigation into a recent security incident reveals that several decryption rules have been disabled. The security team wants to generate email alerts when decryption rules are changed.
How should email log forwarding be configured to achieve this goal?
A. With the relevant system log filter inside Device > Log Settings
B. With the relevant configuration log filter inside Device > Log Settings
C. With the relevant configuration log filter inside Objects > Log Forwarding
D. With the relevant system log filter inside Objects > Log Forwarding
-
Question 133:
A new application server 192.168.197.40 has been deployed in the DMZ. There are no public IP addresses available, resulting in the server sharing NAT IP 198.51.100.88 with another DMZ serve that uses IP address 192.168.197.60.
Firewall security and NAT rules have been configured. The application team has confirmed that the new server is able to establish a secure connection to an external database with IP address 203.0.113.40.
The database team reports that they are unable to establish a secure connection to 198.51.100.88 from 203.0.113.40. However, it confirms a successful ping test to 198.51.100.88.
Referring to the NAT configuration and traffic logs provided how can the firewall engineer resolve the situation and ensure inbound and outbound connections work concurrently for both DMZ servers?
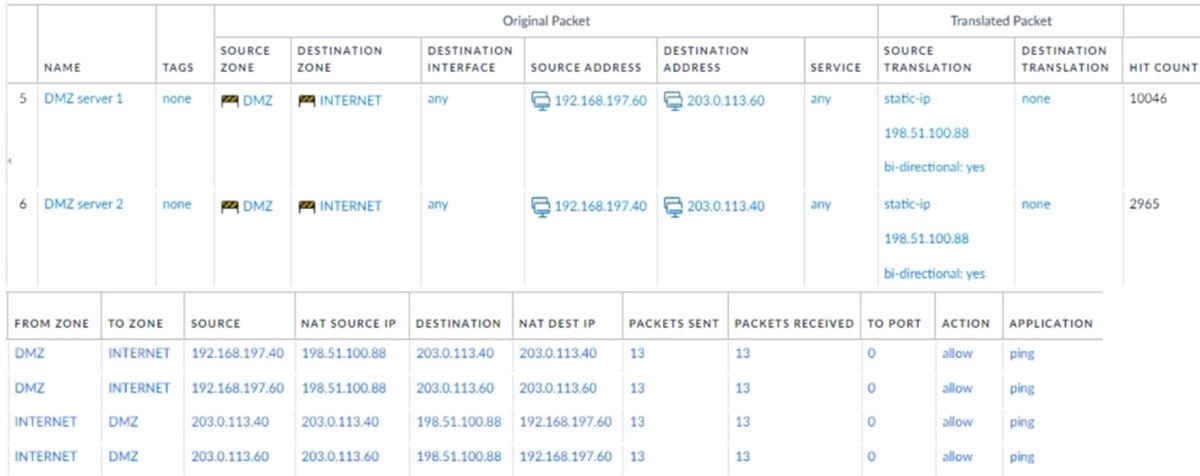
A. Move the NAT rule 6 DMZ server 2 above NAT rule 5 DMZ server 1.
B. Replace the two NAT rules with a single rule that has both DMZ servers as "Source Address" both external servers as "Destination Address," and Source Translation remaining as is with bidirectional option enabled.
C. Configure separate source NAT and destination NAT rules for the two DMZ servers without using the bidirectional option.
D. Sharing a single NAT IP is possible for outbound connectivity not for inbound therefore a new public IP address must be obtained for the new DMZ server and used in the NAT rule 6 DMZ server 2.
-
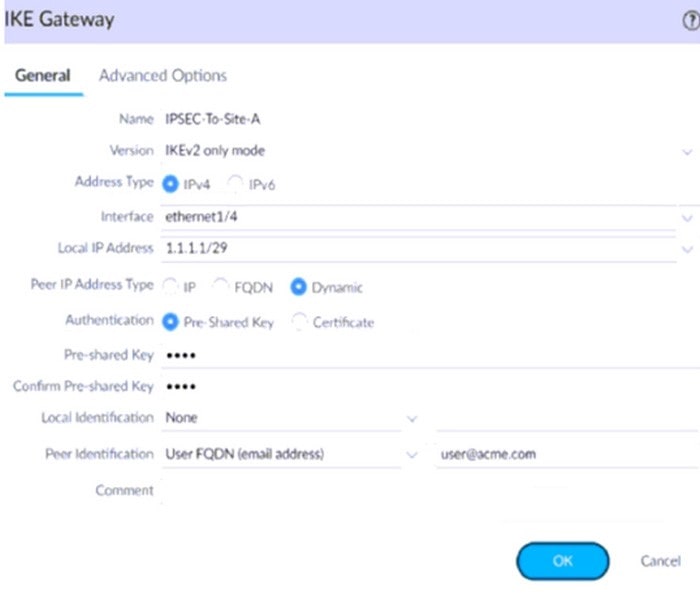
Question 134:
A firewall administrator is configuring an IPSec tunnel between Site A and Site B. The Site A firewall uses a DHCP assigned address on the outside interface of the firewall, and the Site B firewall uses a static IP address assigned to the
outside interface of the firewall. However, the use of dynamic peering is not working.
Refer to the two sets of configuration settings provided. Which two changes will allow the configurations to work? (Choose two.)
Site A configuration:
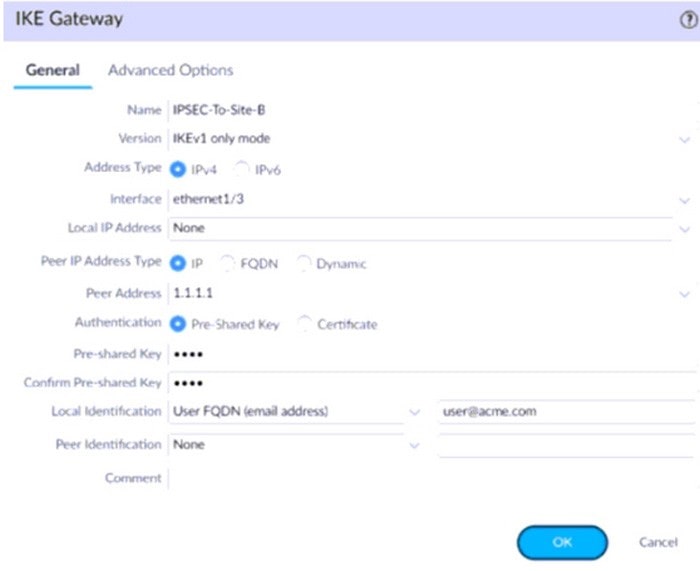
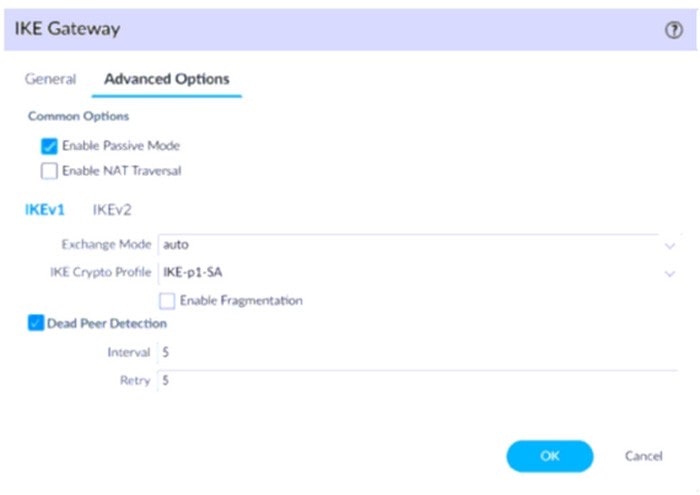
Site B configuration:
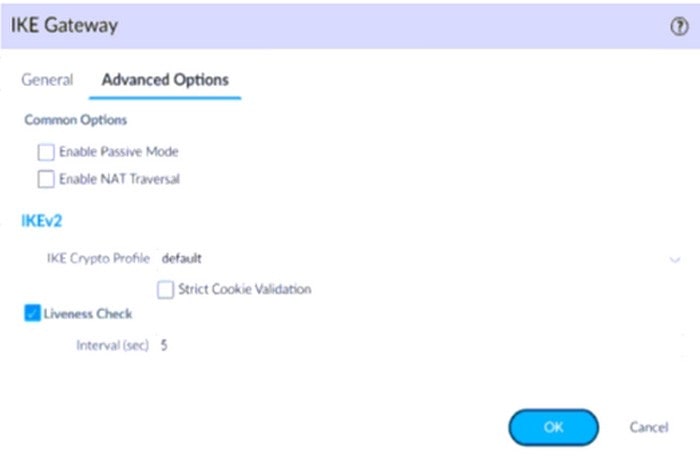
A. Match IKE version on both firewalls.
B. Configure Local Identification on Site B firewall.
C. Enable NAT Traversal on Site B firewall.
D. Disable passive mode on Site A firewall.
-
Question 135:
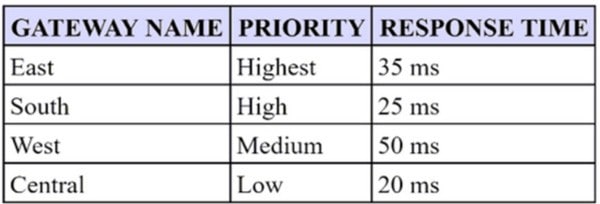
A security engineer has configured a GlobalProtect portal agent with four gateways.
Which GlobalProtect Gateway will users connect to based on the chart provided?
A. East
B. South
C. West
D. Central
-
Question 136:
A firewall engineer creates a source NAT rule to allow the company's internal private network 10.0.0.0/23 to access the internet. However, for security reasons, one server in that subnet (10.0.0.10/32) should not be allowed to access the internet, and therefore should not be translated with the NAT rule.
Which set of steps should the engineer take to accomplish this objective?
A. 1. Create a NAT rule (NAT-Rule-1) and set the source address in the original packet to 10.0.0.10/32.
2. Check the box for negate option to negate this IP from the NAT translation.
B. 1. Create a NAT rule (NAT-Rule-1) and set the source address in the original packet to 10.0.0.0/23.
2. Check the box for negate option to negate this IP subnet from NAT translation.
C. 1. Create a source NAT rule (NAT-Rule-1) to translate 10.0.0/23 with source address translation set to dynamic IP and port.
2.
Create another NAT rule (NAT-Rule-2) with source IP address in the original packet set to 10.0.0.10/32 and source translation set to none.
3.
Place (NAT-Rule-2) above (NAT-Rule-1).
D. 1. Create a source NAT rule (NAT-Rule-1) to translate 10.0.0/23 with source address translation set to dynamic IP and port.
2.
Create another NAT rule (NAT-Rule-2) with source IP address in the original packet set to 10.0.0.10/32 and source translation set to none.
3.
Place (NAT-Rule-1) above (NAT-Rule-2).
-
Question 137:
Which two items must be configured when implementing application override and allowing traffic through the firewall? (Choose two.)
A. Application filter
B. Application override policy rule
C. Security policy rule
D. Custom app
-
Question 138:
Which server platforms can be monitored when a company is deploying User-ID through server monitoring in an environment with diverse directory services?
A. Novell eDirectory, Microsoft Terminal Server, and Microsoft Active Directory
B. Red Hat Linux, Microsoft Exchange, and Microsoft Terminal Server
C. Novell eDirectory, Microsoft Exchange, and Microsoft Active Directory
D. Red Hat Linux, Microsoft Active Directory, and Microsoft Exchange
-
Question 139:
An engineer is monitoring an active/passive high availability (HA) firewall pair. Which HA firewall state describes the firewall that is currently processing traffic?
A. Active-primary
B. Active
C. Active-secondary
D. Initial
-
Question 140:
A root cause analysis investigation into a recent security incident reveals that several decryption rules have been disabled. The security team wants to generate email alerts when decryption rules are changed. How should email log forwarding be configured to achieve this goal?
A. With the relevant system log filter inside Device > Log Settings
B. With the relevant configuration log filter inside Device > Log Settings
C. With the relevant configuration log filter inside Objects > Log Forwarding
D. With the relevant system log filter inside Objects > Log Forwarding
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.