Exam Details
Exam Code
:PCNSEExam Name
:Palo Alto Networks Certified Network Security Engineer - PAN-OS 11.x (PCNSE)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:860 Q&AsLast Updated
:Aug 19, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSE Questions & Answers
-
Question 91:
Review the screenshots and consider the following information:
1.
FW-1 is assigned to the FW-1_DG device group and FW-2 is assigned to OFFICE_FW_DG
2.
There are no objects configured in REGIONAL_DG and OFFICE_FW_DG device groups Which IP address will be pushed to the firewalls inside Address Object Server-1?
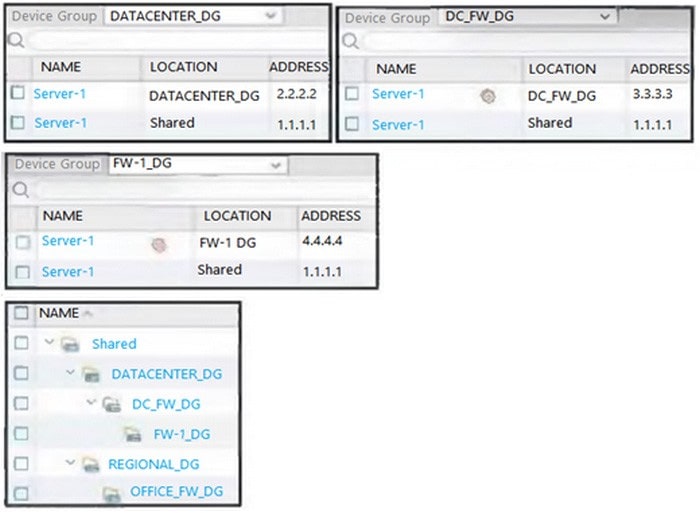
A. Server-1 on FW-1 will have IP 2.2.2.2 Server-1 will not be pushed to FW-2
B. Server-1 on FW-1 will have IP 3.3.3.3 Server-1 will not be pushed to FW-2
C. Server-1 on FW-1 will have IP 1.1.1.1 Server-1 will not be pushed to FW-2
D. Server-1 on FW-1 will have IP 4.4.4.4 Server-1 on FW-2 will have IP 1.1.1.1
-
Question 92:
Which two methods can be used to verify firewall connectivity to AutoFocus? (Choose two.)
A. Verify AutoFocus status using the CLI test command.
B. Check the WebUI Dashboard AutoFocus widget.
C. Check for WildFire forwarding logs.
D. Check the license.
E. Verify AutoFocus is enabled below Device Management tab.
-
Question 93:
A bootstrap USB flash drive has been prepared using a Linux workstation to load the initial configuration of a Palo Alto Networks firewall. The USB flash drive was formatted using file system ntfs and the initial configuration is stored in a file
named init-cfg.txt.
The contents of init-cfg.txt in the USB flash drive are as follows:
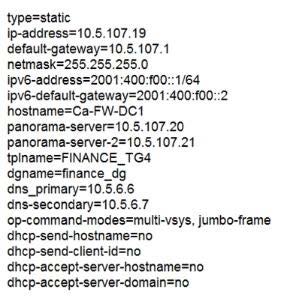
The USB flash drive has been inserted in the firewalls' USB port, and the firewall has been powered on. Upon boot, the firewall fails to begin the bootstrapping process. The failure is caused because:
A. the bootstrap.xml file is a required file, but it is missing
B. nit-cfg.txt is an incorrect filename, the correct filename should be init-cfg.xml
C. The USB must be formatted using the ext4 file system
D. There must be commas between the parameter names and their values instead of the equal symbols
E. The USB drive has been formatted with an unsupported file system
-
Question 94:
Given the following snippet of a WildFire submission log, did the end user successfully download a file?

A. Yes, because the final action is set to "allow."
B. No, because the action for the wildfire-virus is "reset-both."
C. No, because the URL generated an alert.
D. Yes, because both the web-browsing application and the flash file have the "alert" action.
-
Question 95:
An administrator has been tasked with configuring decryption policies, Which decryption best practice should they consider?
A. Consider the local, legal, and regulatory implications and how they affect which traffic can be decrypted.
B. Decrypt all traffic that traverses the firewall so that it can be scanned for threats.
C. Place firewalls where administrators can opt to bypass the firewall when needed.
D. Create forward proxy decryption rules without Decryption profiles for unsanctioned applications.
-
Question 96:
An engineer is monitoring an active/active high availability (HA) firewall pair.
Which HA firewall state describes the firewall that is currently processing traffic?
A. Passive
B. Initial
C. Active
D. Active-primary
-
Question 97:
Which two key exchange algorithms consume the most resources when decrypting SSL traffic? (Choose two.)
A. ECDSA
B. ECDHE
C. RSA
D. DHE
-
Question 98:
An organization wants to begin decrypting guest and BYOD traffic.
Which NGFW feature can be used to identify guests and BYOD users, instruct them how to download and install the CA certificate, and clearly notify them that their traffic will be decrypted?
A. Authentication Portal
B. SSL Decryption profile
C. SSL decryption policy
D. comfort pages
-
Question 99:
After switching to a different WAN connection, users have reported that various websites will not load, and timeouts are occurring. The web servers work fine from other locations.
The firewall engineer discovers that some return traffic from these web servers is not reaching the users behind the firewall. The engineer later concludes that the maximum transmission unit (MTU) on an upstream router interface is set to
1400 bytes.
The engineer reviews the following CLI output for ethernet1/1.
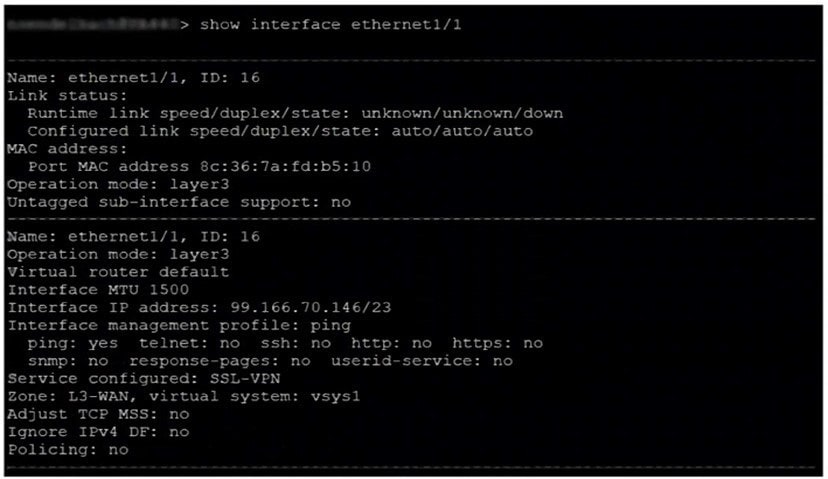
Which setting should be modified on ethernet1/1 to remedy this problem?
A. Change the subnet mask from /23 to /24.
B. Lower the interface MTU value below 1500.
C. Adjust the TCP maximum segment size (MSS) value.
D. Enable the Ignore IPv4 Don't Fragment (DF) setting.
-
Question 100:
In a security-first network, what is the recommended threshold value for apps and threats to be dynamically updated?
A. 1 to 4 hours
B. 6 to 12 hours
C. 24 hours
D. 36 hours
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.