Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 211:
Which data flow direction is protected in a zero trust firewall deployment that is not protected in a perimeter-only firewall deployment?
A. outbound
B. north south
C. inbound
D. east west
-
Question 212:
What are three factors that can be used in domain generation algorithms? (Choose three.)
A. cryptographic keys
B. time of day
C. other unique values
D. URL custom categories
E. IP address
-
Question 213:
Your company is highly concerned with their Intellectual property being accessed by unauthorized resources. There is a mature process to store and include metadata tags for all confidential documents. Which Security profile can further ensure that these documents do not exit the corporate network?
A. File Blocking
B. Data Filtering
C. Anti-Spyware
D. URL Filtering
-
Question 214:
An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact a command-and-control (C2) server. Which two security profile components will detect and prevent this threat after the firewall's signature database has been updated? (Choose two.)
A. vulnerability protection profile applied to outbound security policies
B. anti-spyware profile applied to outbound security policies
C. antivirus profile applied to outbound security policies
D. URL filtering profile applied to outbound security policies
-
Question 215:
The compliance officer requests that all evasive applications need to be blocked on all perimeter firewalls out to the internet The firewall is configured with two zones;
1.
trust for internal networks
2.
untrust to the internet
Based on the capabilities of the Palo Alto Networks NGFW, what are two ways to configure a security policy using App-ID to comply with this request? (Choose two )
A. Create a deny rule at the top of the policy from trust to untrust with service application-default and add an application filter with the evasive characteristic
B. Create a deny rule at the top of the policy from trust to untrust over any service and select evasive as the application
C. Create a deny rule at the top of the policy from trust to untrust with service application-default and select evasive as the application
D. Create a deny rule at the top of the policy from trust to untrust over any service and add an application filter with the evasive characteristic
-
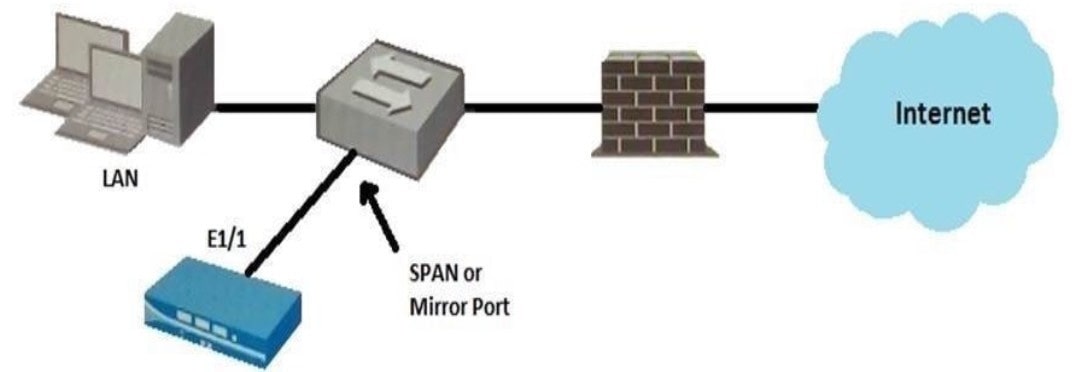
Question 216:
Given the topology, which zone type should you configure for firewall interface E1/1?
A. Tap
B. Tunnel
C. Virtual Wire
D. Layer3
-
Question 217:
Which operations are allowed when working with App-ID application tags?
A. Predefined tags may be deleted.
B. Predefined tags may be augmented by custom tags.
C. Predefined tags may be modified.
D. Predefined tags may be updated by WildFire dynamic updates.
-
Question 218:
Which action can be set in a URL Filtering Security profile to provide users temporary access to all websites in a given category using a provided password?
A. exclude
B. continue
C. hold
D. override
-
Question 219:
Which built-in IP address EDL would be useful for preventing traffic from IP addresses that are verified as unsafe based on WildFire analysis Unit 42 research and data gathered from telemetry?
A. Palo Alto Networks CandC IP Addresses
B. Palo Alto Networks Bulletproof IP Addresses
C. Palo Alto Networks High-Risk IP Addresses
D. Palo Alto Networks Known Malicious IP Addresses
-
Question 220:
Which object would an administrator create to enable access to all applications in the office-programs subcategory?
A. HIP profile
B. Application group
C. URL category
D. Application filter
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.