Exam Details
Exam Code
:PCNSAExam Name
:Palo Alto Networks Certified Network Security Administrator (PCNSA)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:443 Q&AsLast Updated
:Aug 15, 2025
Palo Alto Networks Palo Alto Networks Certifications PCNSA Questions & Answers
-
Question 201:
Which rule type is appropriate for matching traffic occurring within a specified zone?
A. Interzone
B. Universal
C. Intrazone
D. Shadowed
-
Question 202:
Which interface type is used to monitor traffic and cannot be used to perform traffic shaping?
A. Layer 2
B. Tap
C. Layer 3
D. Virtual Wire
-
Question 203:
The CFO found a USB drive in the parking lot and decide to plug it into their corporate laptop. The USB drive had malware on it that loaded onto their computer and then contacted a known command and control (CnC) server, which ordered the infected machine to begin Exfiltrating data from the laptop.
Which security profile feature could have been used to prevent the communication with the CnC server?
A. Create an anti-spyware profile and enable DNS Sinkhole
B. Create an antivirus profile and enable DNS Sinkhole
C. Create a URL filtering profile and block the DNS Sinkhole category
D. Create a security policy and enable DNS Sinkhole
-
Question 204:
Based on the screenshot what is the purpose of the included groups?
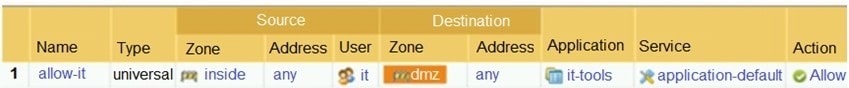
A. They are only groups visible based on the firewall's credentials.
B. They are used to map usernames to group names.
C. They contain only the users you allow to manage the firewall.
D. They are groups that are imported from RADIUS authentication servers.
-
Question 205:
Based on the graphic which statement accurately describes the output shown in the server monitoring panel?
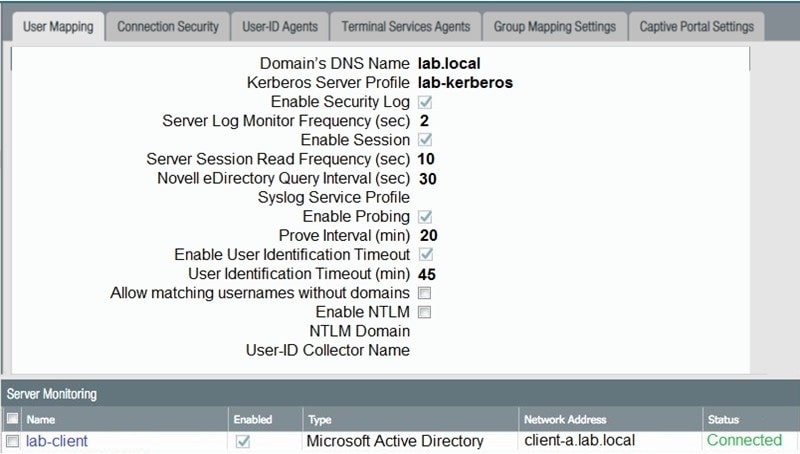
A. The User-ID agent is connected to a domain controller labeled lab-client.
B. The host lab-client has been found by the User-ID agent.
C. The host lab-client has been found by a domain controller.
D. The User-ID agent is connected to the firewall labeled lab-client.
-
Question 206:
An administrator is troubleshooting an issue with traffic that matches the intrazone-default rule, which is set to default configuration.
What should the administrator do?
A. change the logging action on the rule
B. review the System Log
C. refresh the Traffic Log
D. tune your Traffic Log filter to include the dates
-
Question 207:
What action will inform end users when their access to Internet content is being restricted?
A. Create a custom 'URL Category' object with notifications enabled.
B. Publish monitoring data for Security policy deny logs.
C. Ensure that the 'site access" setting for all URL sites is set to 'alert'.
D. Enable 'Response Pages' on the interface providing Internet access.
-
Question 208:
At which stage of the cyber-attack lifecycle would the attacker attach an infected PDF file to an email?
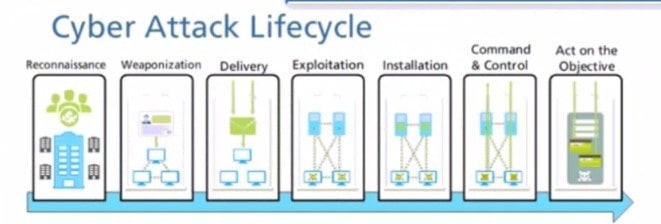
A. delivery
B. command and control
C. explotation
D. reinsurance
E. installation
-
Question 209:
A network administrator created an intrazone Security policy rule on the firewall. The source zones were set to IT. Finance, and HR. Which two types of traffic will the rule apply to? (Choose two)
A. traffic between zone IT and zone Finance
B. traffic between zone Finance and zone HR
C. traffic within zone IT
D. traffic within zone HR
-
Question 210:
An administrator is trying to enforce policy on some (but not all) of the entries in an external dynamic list. What is the maximum number of entries that they can be exclude?
A. 50
B. 100
C. 200
D. 1,000
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCNSA exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.