Exam Details
Exam Code
:PCCSEExam Name
:Prisma Certified Cloud Security Engineer (PCCSE)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:281 Q&AsLast Updated
:Aug 19, 2025
Palo Alto Networks Palo Alto Networks Certifications PCCSE Questions & Answers
-
Question 101:
A customer wants to monitor the company's AWS accounts via Prisma Cloud, but only needs the resource configuration to be monitored for now.
Which two pieces of information do you need to onboard this account? (Choose two.)
A. Cloudtrail
B. Subscription ID
C. Active Directory ID
D. External ID
E. Role ARN
-
Question 102:
What is an automatically correlated set of individual events generated by the firewall and runtime sensors to identify unfolding attacks?
A. policy
B. incident
C. audit
D. anomaly
-
Question 103:
An administrator wants to enforce a rate limit for users not being able to post five (5) .tar.gz files within five (5) seconds. What does the administrator need to Configure?
A. A ban for DoS protection with an average rate of 5 and file extensions match on .tar.gz on WAAS
B. A ban for DoS protection with a burst rate of 5 and file extensions match on .tar.gz on CNNF
C. A ban for DoS protection with a burst rate of 5 and file extensions match on .tar gz on WAAS
D. A ban for DoS protection with an average rate of 5 and file extensions match on .tar.gz on CNNF
-
Question 104:
A manager informs the SOC that one or more RDS instances have been compromised and the SOC needs to make sure production RDS instances are NOT publicly accessible. Which action should the SOC take to follow security best practices?
A. Enable "AWS S3 bucket is publicly accessible" policy and manually remediate each alert.
B. Enable "AWS RDS database instance is publicly accessible" policy and for each alert, check that it is a production instance, and then manually remediate.
C. Enable "AWS S3 bucket is publicly accessible" policy and add policy to an auto-remediation alert rule.
D. Enable "AWS RDS database instance is publicly accessible" policy and add policy to an auto-remediation alert rule.
-
Question 105:
The development team is building pods to host a web front end, and they want to protect these pods with an application firewall. Which type of policy should be created to protect this pod from Layer7 attacks?
A. The development team should create a WAAS rule for the host where these pods will be running.
B. The development team should create a WAAS rule targeted at all resources on the host.
C. The development team should create a runtime policy with networking protections.
D. The development team should create a WAAS rule targeted at the image name of the pods.
-
Question 106:
Which of the following are correct statements regarding the use of access keys? (Choose two.)
A. Access keys must have an expiration date
B. Up to two access keys can be active at any time
C. System Admin can create access key for all users
D. Access keys are used for API calls
-
Question 107:
Given the following RQL:

Which audit event snippet is identified by the RQL?
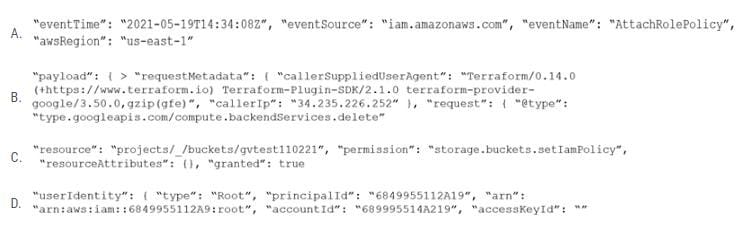
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 108:
Given the following audit event activity snippet:
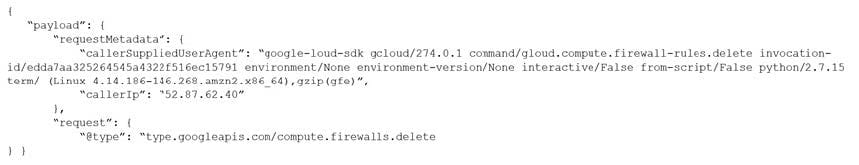
Which RQL will be triggered by the audit event?
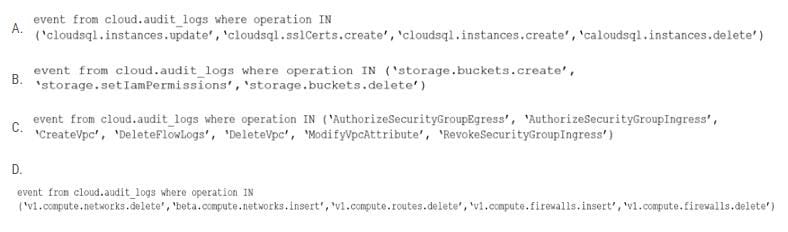
A. Option A
B. Option B
C. Option C
D. Option D
-
Question 109:
Which three fields are mandatory when authenticating the Prisma Cloud plugin in the IntelliJ application? (Choose three.)
A. Secret Key
B. Prisma Cloud API URL
C. Tags
D. Access Key
E. Asset Name
-
Question 110:
Which data security default policy is able to scan for vulnerabilities?
A. Objects containing Vulnerabilities
B. Objects containing Threats
C. Objects containing Malware
D. Objects containing Exploits
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCCSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.