Exam Details
Exam Code
:PCCSEExam Name
:Prisma Certified Cloud Security Engineer (PCCSE)Certification
:Palo Alto Networks CertificationsVendor
:Palo Alto NetworksTotal Questions
:281 Q&AsLast Updated
:Aug 19, 2025
Palo Alto Networks Palo Alto Networks Certifications PCCSE Questions & Answers
-
Question 231:
Which resources can be added in scope while creating a vulnerability policy for continuous integration?
A. Images and cluster
B. Images and labels
C. Images and containers
D. Labels and AccountID
-
Question 232:
A container and image compliance rule has been configured by enabling all checks; however, upon review, the container's compliance view reveals only the entries in the image below.
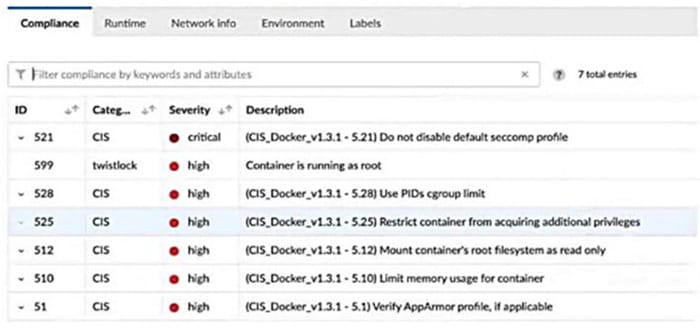
What is the appropriate action to take next?
A. Deploy defenders to scan complete container compliance.
B. Change the rule options to list both failed and passed checks in the compliance rule edit window.
C. Wait until Prisma Cloud finishes the compliance scan and recheck.
D. Change the rule options to list only failed checks in the compliance rule edit window.
-
Question 233:
What is the primary purpose of Prisma Cloud Code Security?
A. To address cloud infrastructure misconfigurations in code before they become alerts or incidents
B. To provide a platform for developers to create custom security policies for applications
C. To offer instant feedback on application performance issues and bottlenecks
D. To triage alerts and incidents in realtime during deployment
-
Question 234:
How does assigning an account group to an administrative user on Prisma Cloud help restrict access to resources?
A. It restricts access to all resources and data within the cloud account.
B. It restricts access only to certain types of resources within the cloud account.
C. It restricts access only to the resources and data that pertains to the cloud account(s) within an account group.
D. It does not restrict access to any resources within the cloud account.
-
Question 235:
Which three AWS policy types and identities are used to calculate the net effective permissions? (Choose three.)
A. AWS IAM group
B. AWS IAM role
C. AWS service control policies (SCPs)
D. AWS IAM tag policy
E. AWS IAM User
-
Question 236:
Based on the following information, which RQL query will satisfy the requirement to identify VM hosts deployed to organization public cloud environments exposed to network traffic from the internet and affected by Text4Shell RCE (CVE2022-42889) vulnerability?
Network flow logs from all virtual private cloud (VPC) subnets are ingested to the Prisma Cloud Enterprise Edition tenant. All virtual machines (VMs) have Prisma Cloud Defender deployed.
A. network from vpc.flow_record where bytes > 0 AND dest.resource IN (resource where finding.type IN ('Host Vulnerability') AND finding.source IN ('Prisma Cloud') AND finding.name IN ('CVE-2022-42889')) AND source.publicnetwork IN ('Internet IPs', 'Suspicious IPs')
B. config from vpc.flow_record where bytes > 0 AND dest.resource IN (resource where finding.type IN ('Host Vulnerability') AND finding.source IN ('Prisma Cloud') AND finding.name IN ('CVE-2022-42889')) AND source.publicnetwork = ('Internet IPs' or 'Suspicious IPs')
C. network from vpc.flow_record where bytes > 0 AND finding.type IN ('Host Vulnerability') AND finding.source IN ('Prisma Cloud') AND finding.name IN ('CVE-2022-42889') AND source.publicnetwork = 'Internet IPs'
D. config from cloud.resource where cloud.type = 'aws' AND api.name = 'aws-ec2-describe-instances' AND json.rule = publicIpAddress exists AND finding.type IN ('Host Vulnerability') AND finding.source IN ('Prisma Cloud') AND finding.name IN ('CVE-2022-42889')
-
Question 237:
Which of the following is not a supported external integration for receiving Prisma Cloud Code Security notifications?
A. ServiceNow
B. Splunk
C. Microsoft Teams
D. Cortex XSOAR
-
Question 238:
Which type of RQL query should be run to determine if AWS Elastic Compute Cloud (EC2) instances without encryption was enabled?
A. NETWORK
B. CONFIG
C. EVENT
D. SECURITY
-
Question 239:
Which RQL query is used to detect certain high-risk activities executed by a root user in AWS?
A. event from cloud.audit_logs where operation IN ( 'ChangePassword', 'ConsoleLogin', 'DeactivateMFADevice', 'DeleteAccessKey' , 'DeleteAlarms' ) AND user = 'root'
B. event from cloud.security_logs where operation IN ( 'ChangePassword', 'ConsoleLogin', 'DeactivateMFADevice', 'DeleteAccessKey' , 'DeleteAlarms' ) AND user = 'root'
C. config from cloud.audit_logs where operation IN ( 'ChangePassword', 'ConsoleLogin', 'DeactivateMFADevice', 'DeleteAccessKey', 'DeleteAlarms' ) AND user = 'root'
D. event from cloud.audit_logs where Risk.Level = 'high' AND user = 'root'
-
Question 240:
What is required for Prisma Cloud to successfully execute auto-remediation commands?
A. Access to the cloud platform only for Azure
B. Write access to the cloud platform
C. Read access to the cloud platform
D. Prisma Cloud requires no access to the cloud platform
Related Exams:
PAN-NGFE
Palo Alto Networks Network Next-Generation Firewall EngineerPAN-NSG
Palo Alto Networks Network Security GeneralistPAN-NSP
Palo Alto Networks Network Security ProfessionalPAN-SSEE
Palo Alto Networks Security Service Edge EngineerPAN-XDRE
Palo Alto Networks XDR EngineerPCCET
Palo Alto Networks Certified Cybersecurity Entry-level Technician (PCCET)PCCSA
Palo Alto Networks Certified Cybersecurity Associate (PCCSA)PCCSE
Prisma Certified Cloud Security Engineer (PCCSE)PCDRA
Palo Alto Networks Certified Detection and Remediation Analyst (PCDRA)PCNSA
Palo Alto Networks Certified Network Security Administrator (PCNSA)
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Palo Alto Networks exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your PCCSE exam preparations and Palo Alto Networks certification application, do not hesitate to visit our Vcedump.com to find your solutions here.