Exam Details
Exam Code
:NSE8_812Exam Name
:Network Security Expert 8 Written ExamCertification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:105 Q&AsLast Updated
:Aug 03, 2025
Fortinet Fortinet Certifications NSE8_812 Questions & Answers
-
Question 21:
You are troubleshooting a FortiMail Cloud service integrated with Office 365 where outgoing emails are not reaching the recipients' mail What are two possible reasons for this problem? (Choose two.)
A. The FortiMail access control rule to relay from Office 365 servers FQDN is missing.
B. The FortiMail DKIM key was not set using the Auto Generation option.
C. The FortiMail access control rules to relay from Office 365 servers public IPs are missing.
D. A Mail Flow connector from the Exchange Admin Center has not been set properly to the FortiMail Cloud FQDN.
-
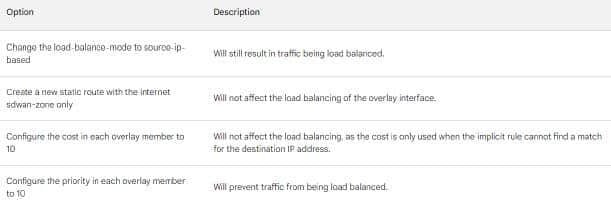
Question 22:
Refer to the exhibit, which shows a Branch1 configuration and routing table. In the SD-WAN implicit rule, you do not want the traffic load balance for the overlay interface when all members are available.
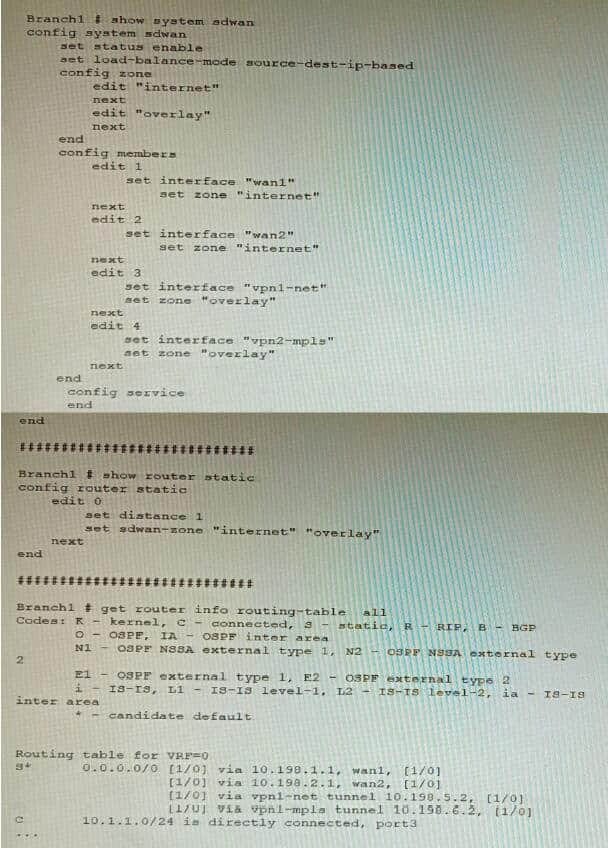
In this scenario, which configuration change will meet this requirement?
A. Change the load-balance-mode to source-ip-based.
B. Create a new static route with the internet sdwan-zone only
C. Configure the cost in each overlay member to 10.
D. Configure the priority in each overlay member to 10.
-
Question 23:
A retail customer with a FortiADC HA cluster load balancing five webservers in L7 Full NAT mode is receiving reports of users not able to access their website during a sale event. But for clients that were able to connect, the website works fine.
CPU usage on the FortiADC and the web servers is low, application and database servers are still able to handle more traffic, and the bandwidth utilization is under 30%.
Which two options can resolve this situation? (Choose two.)
A. Change the persistence rule to LB_PERSIS_SSL_SESSJD.
B. Add more web servers to the real server poof
C. Disable SSL between the FortiADC and the web servers
D. Add a connection-pool to the FortiADC virtual server
-
Question 24:
A customer wants to use the FortiAuthenticator REST API to retrieve an SSO group called SalesGroup. The following API call is being made with the 'curl' utility:

Which two statements correctly describe the expected behavior of the FortiAuthenticator REST API? (Choose two.)
A. Only users with the "Full permission" role can access the REST API
B. This API call will fail because it requires that API version 2
C. If the REST API web service access key is lost, it cannot be retrieved and must be changed.
D. The syntax is incorrect because the API calls needs the get method.
-
Question 25:
A remote worker requests access to an SSH server inside the network. You deployed a ZTNA Rule to their FortiClient. You need to follow the security requirements to inspect this traffic. Which two statements are true regarding the requirements? (Choose two.)
A. FortiGate can perform SSH access proxy host-key validation.
B. You need to configure a FortiClient SSL-VPN tunnel to inspect the SSH traffic.
C. SSH traffic is tunneled between the client and the access proxy over HTTPS
D. Traffic is discarded as ZTNA does not support SSH connection rules
-
Question 26:
Refer to the exhibits.
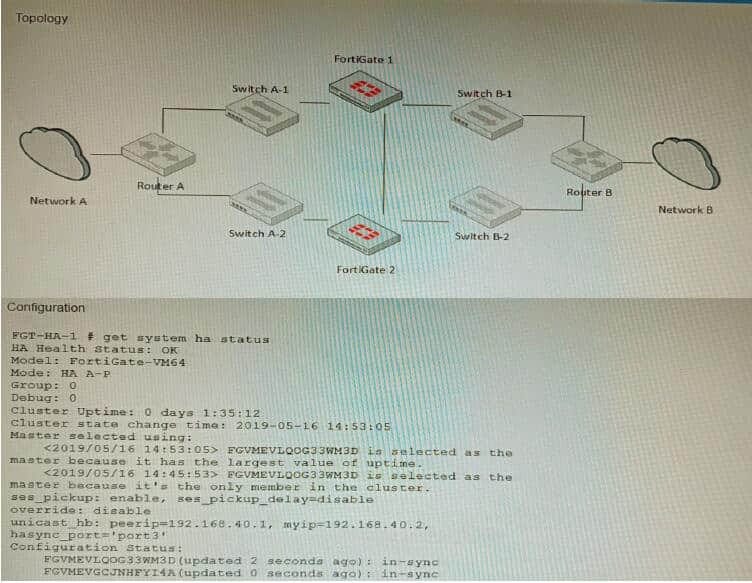
The exhibits show a FortiGate network topology and the output of the status of high availability on the FortiGate. Given this information, which statement is correct?
A. The ethertype values of the HA packets are 0x8890, 0x8891, and 0x8892
B. The cluster mode can support a maximum of four (4) FortiGate VMs
C. The cluster members are on the same network and the IP addresses were statically assigned.
D. FGVMEVLQOG33WM3D and FGVMEVGCJNHFYI4A share a virtual MAC address.
-
Question 27:
Review the following FortiGate-6000 configuration excerpt:
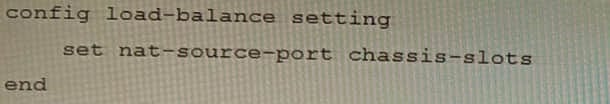
Based on the configuration, which statement is correct regarding SNAT source port partitioning behavior?
A. It dynamically distributes SNAT source ports to operating FPCs or FPMs.
B. It is the default SNAT configuration and preserves active sessions when an FPC or FPM goes down.
C. It statically distributes SNAT source ports to operating FPCs or FPMs
D. It equally distributes SNAT source ports across chassis slots.
-
Question 28:
You want to use the MTA adapter feature on FortiSandbox in an HA-Cluster. Which statement about this solution is true?
A. The configuration of the MTA Adapter Local Interface is different than on port1.
B. The MTA adapter is only available in the primary node.
C. The MTA adapter mode is only detection mode.
D. The configuration is different than on a standalone device.
-
Question 29:
Which two statements are correct on a FortiGate using the FortiGuard Outbreak Protection Service (VOS)? (Choose two.)
A. The FortiGuard VOS can be used only with proxy-base policy inspections.
B. If third-party AV database returns a match the scanned file is deemed to be malicious.
C. The antivirus database queries FortiGuard with the hash of a scanned file
D. The AV engine scan must be enabled to use the FortiGuard VOS feature
E. The hash signatures are obtained from the FortiGuard Global Threat Intelligence database.
-
Question 30:
SD-WAN is configured on a FortiGate. You notice that when one of the internet links has high latency the time to resolve names using DNS from FortiGate is very high.
You must ensure that the FortiGate DNS resolution times are as low as possible with the least amount of work. What should you configure?
A. Configure local out traffic to use the outgoing interface based on SD-WAN rules with a manual defined IP associated to a loopback interface and configure an SD-WAN rule from the loopback to the DNS server.
B. Configure an SD-WAN rule to the DNS server and use the FortiGate interface IPs in the source address.
C. Configure two DNS servers and use DNS servers recommended by the two internet providers.
D. Configure local out traffic to use the outgoing interface based on SD-WAN rules with the interface IP and configure an SD-WAN rule to the DNS server.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE8_812 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.