Exam Details
Exam Code
:NSE8_812Exam Name
:Network Security Expert 8 Written ExamCertification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:105 Q&AsLast Updated
:Aug 03, 2025
Fortinet Fortinet Certifications NSE8_812 Questions & Answers
-
Question 11:
Refer to the exhibit.
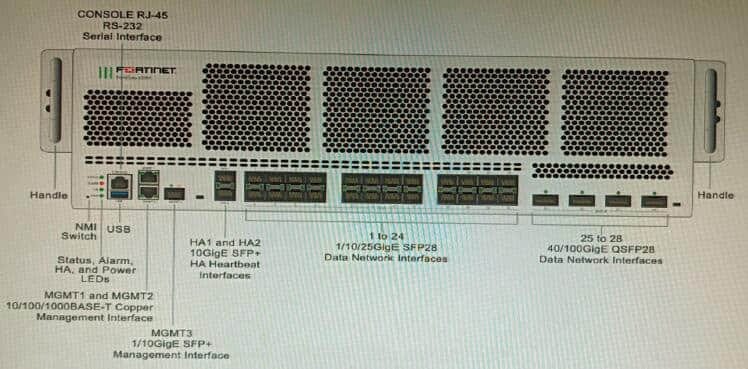
You are deploying a FortiGate 6000F. The device should be directly connected to a switch. In the future, a new hardware module providing higher speed will be installed in the switch, and the connection to the FortiGate must be moved to this higher-speed port.
You must ensure that the initial FortiGate interface connected to the switch does not affect any other port when the new module is installed and the new port speed is defined.
How should the initial connection be made?
A. Connect the switch on any interface between ports 21 to 24
B. Connect the switch on any interface between ports 25 to 28
C. Connect the switch on any interface between ports 1 to 4
D. Connect the switch on any interface between ports 5 to 8.
-
Question 12:
Refer to the exhibit.
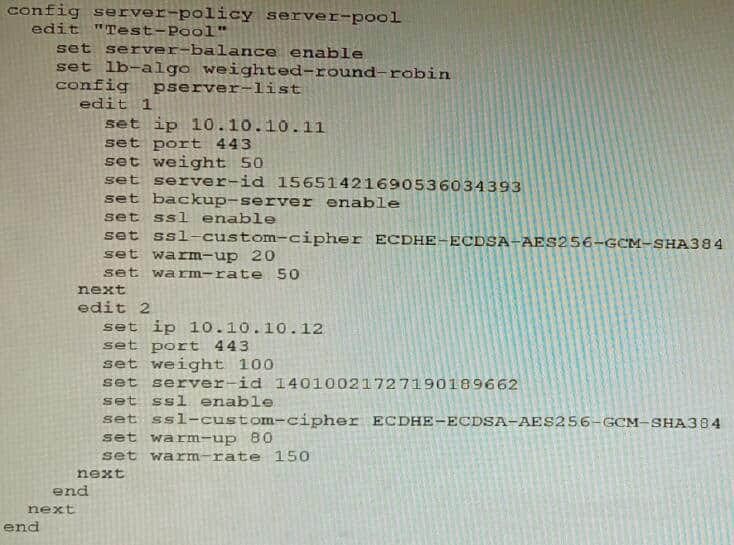
A FortiWeb appliance is configured for load balancing web sessions to internal web servers. The Server Pool is configured as shown in the exhibit.
How will the sessions be load balanced between server 1 and server 2 during normal operation?
A. Server 1 will receive 25% of the sessions, Server 2 will receive 75% of the sessions
B. Server 1 will receive 20% of the sessions, Server 2 will receive 66.6% of the sessions
C. Server 1 will receive 33.3% of the sessions, Server 2 will receive 66 6% of the sessions
D. Server 1 will receive 0% of the sessions Server 2 will receive 100% of the sessions
-
Question 13:
Which two methods are supported for importing user defined Lookup Table Data into the FortiSIEM? (Choose two.)
A. Report
B. FTP
C. API D. SCP
-
Question 14:
Refer to the exhibit showing FortiGate configurations
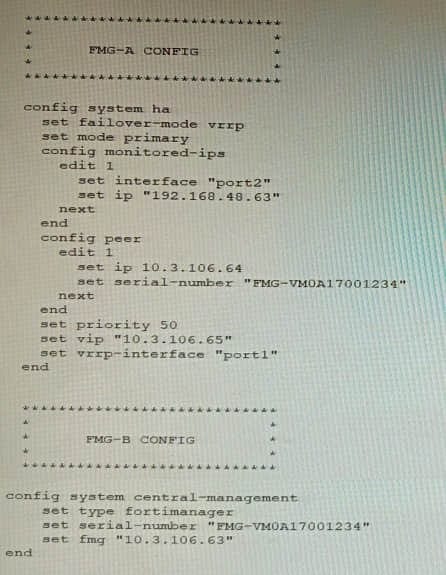
FortiManager VM high availability (HA) is not functioning as expected after being added to an existing deployment.
The administrator finds that VRRP HA mode is selected, but primary and secondary roles are greyed out in the GUI The managed devices never show online when FMG-B becomes primary, but they will show online whenever the FMG-A
becomes primary.
What change will correct HA functionality in this scenario?
A. Change the FortiManager IP address on the managed FortiGate to 10.3.106.65.
B. Make the monitored IP to match on both FortiManager devices.
C. Unset the primary and secondary roles in the FortiManager CLI configuration so VRRP will decide who is primary.
D. Change the priority of FMG-A to be numerically lower for higher preference
-
Question 15:
Refer to the exhibit.
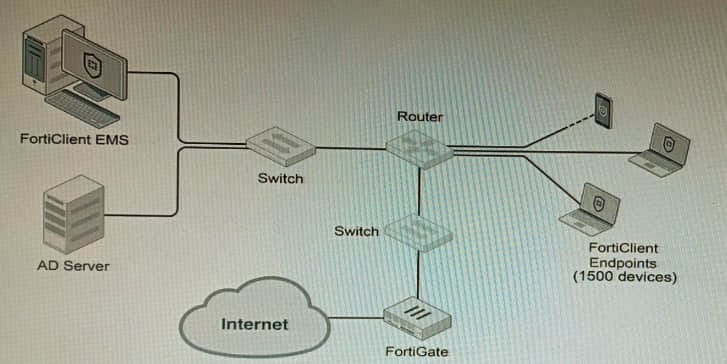
A customer wants FortiClient EMS configured to deploy to 1500 endpoints. The deployment will be integrated with FortiOS and there is an Active Directory server.
Given the configuration shown in the exhibit, which two statements about the installation are correct? (Choose two.)
A. If no client update time is specified on EMS, the user will be able to choose the time of installation if they wish to delay.
B. A client can be eligible for multiple enabled configurations on the EMS server, and one will be chosen based on first priority
C. You can only deploy initial installations to Windows clients.
D. You must use Standard or Enterprise SQL Server rather than the included SQL Server Express
E. The Windows clients only require "File and Printer Sharing0 allowed and the rest is handled by Active Directory group policy
-
Question 16:
A customer with a FortiDDoS 200F protecting their fibre optic internet connection from incoming traffic sees that all the traffic was dropped by the device even though they were not under a DoS attack. The traffic flow was restored after it was rebooted using the GUI. Which two options will prevent this situation in the future? (Choose two)
A. Change the Adaptive Mode.
B. Create an HA setup with a second FortiDDoS 200F
C. Move the internet connection from the SFP interfaces to the LC interfaces
D. Replace with a FortiDDoS 1500F
-
Question 17:
Refer to the exhibit.
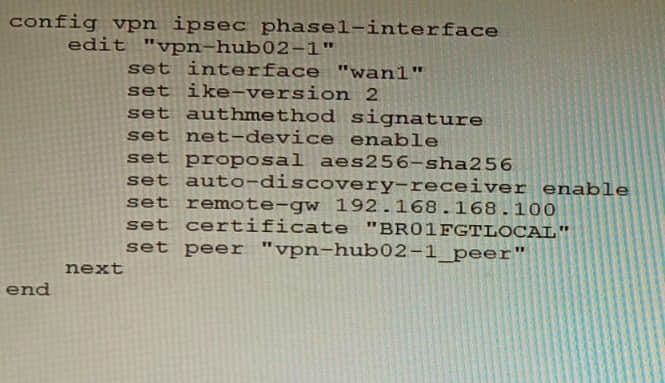
To facilitate a large-scale deployment of SD-WAN/ADVPN with FortiGate devices, you are tasked with configuring the FortiGate devices to support injecting of IKE routes on the ADVPN shortcut tunnels. Which three commands must be added or changed to the FortiGate spoke config vpn ipsec phasei-interface options referenced in the exhibit for the VPN interface to enable this capability? (Choose three.)
A. set net-device disable
B. set mode-cfg enable
C. set ike-version 1
D. set add-route enable
E. set mode-cfg-allow-client-selector enable
-
Question 18:
Review the VPN configuration shown in the exhibit.
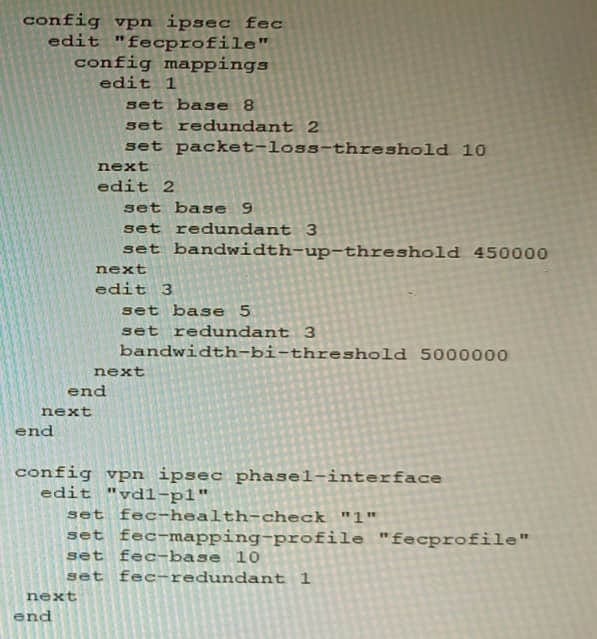
What is the Forward Error Correction behavior if the SD-WAN network traffic download is 500 Mbps and has 8% of packet loss in the environment?
A. 1 redundant packet for every 10 base packets
B. 3 redundant packet for every 5 base packets
C. 2 redundant packet for every 8 base packets
D. 3 redundant packet for every 9 base packets
-
Question 19:
Refer to the exhibits.
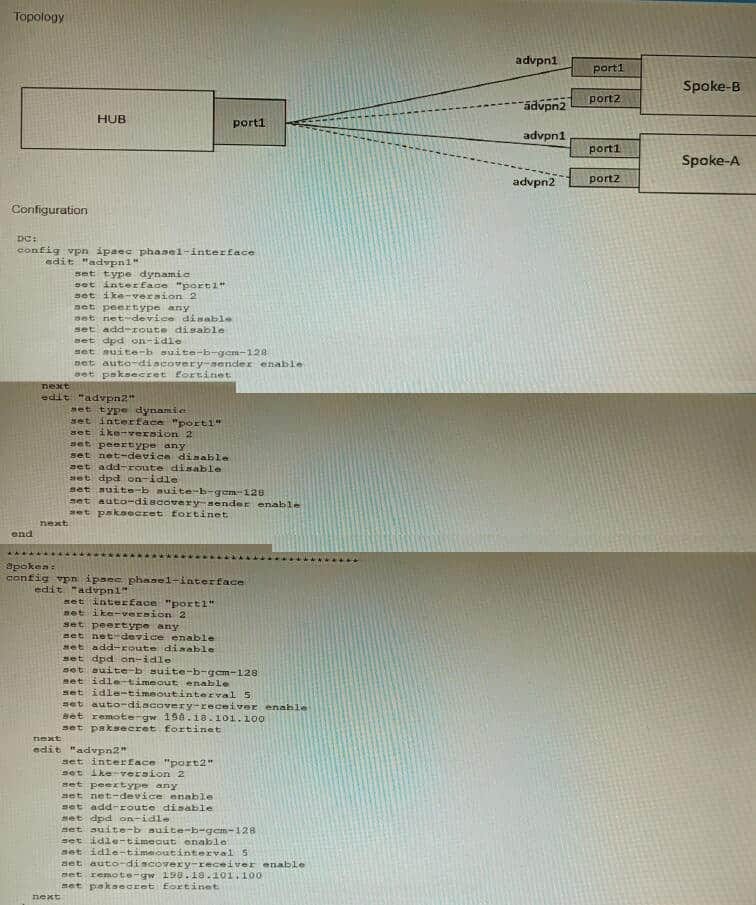
The exhibits show a diagram of a requested topology and the base IPsec configuration.
A customer asks you to configure ADVPN via two internet underlays. The requirement is that you use one interface with a single IP address on DC FortiGate.
In this scenario, which feature should be implemented to achieve this requirement?
A. Use network-overlay id
B. Change advpn2 to IKEv1
C. Use local-id
D. Use peer-id
-
Question 20:
Refer to the exhibit showing the history logs from a FortiMail device.
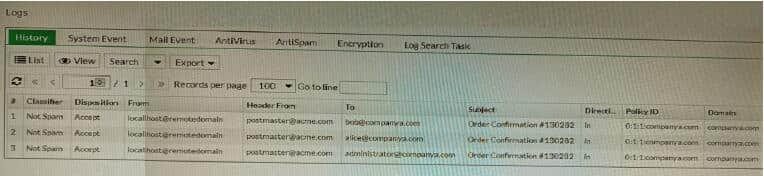
Which FortiMail email security feature can an administrator enable to treat these emails as spam?
A. DKIM validation in a session profile
B. Sender domain validation in a session profile
C. Impersonation analysis in an antispam profile
D. Soft fail SPF validation in an antispam profile
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE8_812 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.