NSE8_812 Exam Details
-
Exam Code
:NSE8_812 -
Exam Name
:Network Security Expert 8 Written Exam -
Certification
:Fortinet Certifications -
Vendor
:Fortinet -
Total Questions
:105 Q&As -
Last Updated
:Jan 14, 2026
Fortinet NSE8_812 Online Questions & Answers
-
Question 1:
A FortiGate is configured to perform outbound firewall authentication with Azure AD as a SAML IdP. What are two valid interactions that occur when the client attempts to access the internet? (Choose two.)
A. FortiGate SP sends a SAML request to the IdP.
B. The Microsoft SAML IdP sends the SAML response to the FortiGate SP.
C. The client browser forwards the SAML response received from Microsoft SAML IdP to the FortiGate SP.
D. FortiGate SP redirects the client browser to the local captive portal and then redirects to the Microsoft SAML IdP. -
Question 2:
Refer to the exhibits, which show a network topology and VPN configuration.
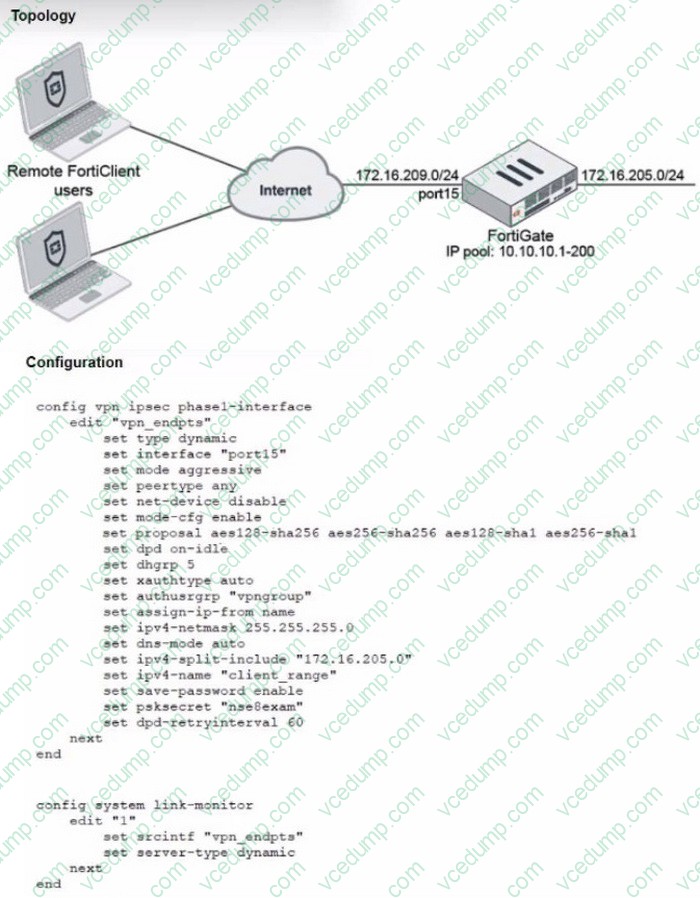
A network administrator has been tasked with modifying the existing dial-up IPsec VPN infrastructure to detect the path quality to the remote endpoints.
After applying the configuration shown in the configuration exhibit, the VPN clients can still connect and access the protected 172.16.205.0/24 network, but no SLA information shows up for the client tunnels when issuing the diagnose sys link-
monitor tunnel all command on the FortiGate CLI.
What is wrong with the configuration?
A. SLA link monitoring does not work with the net-device setting.
B. The admin needs to disable the mode-cfg setting.
C. IPsec Phase1 Interface has to be configured in IPsec main mode.
D. It is necessary to use the IKEv2 protocol in this situation. -
Question 3:
Refer to the exhibits.
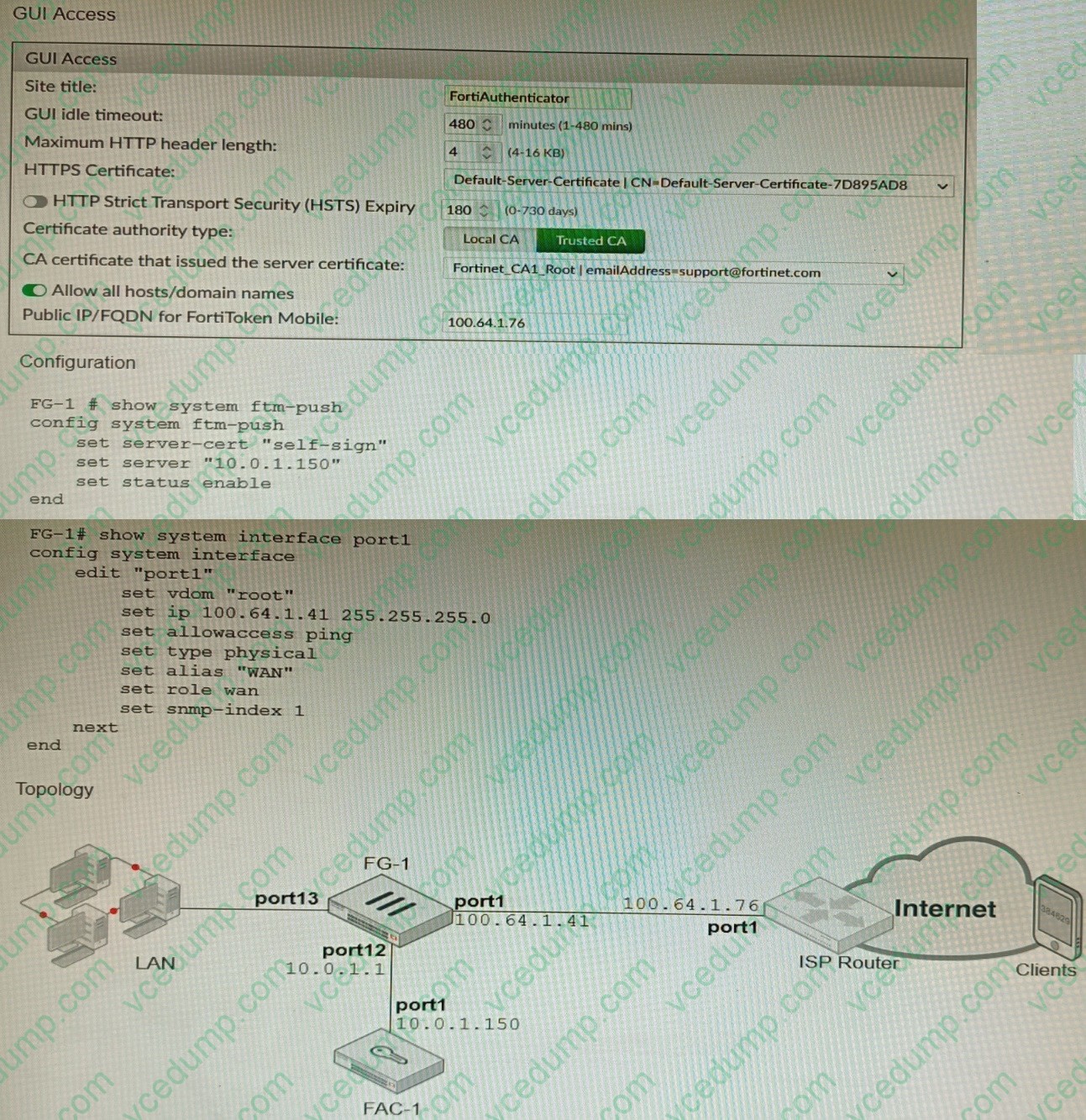
An administrator has configured a FortiGate and Forti Authenticator for two-factor authentication with FortiToken push notifications for their SSL VPN login. Upon initial review of the setup, the administrator has discovered that the customers can manually type in their two-factor code and authenticate but push notifications do not work
Based on the information given in the exhibits, what must be done to fix this?
A. On FG-1 port1, the ftm access protocol must be enabled.
B. FAC-1 must have an internet routable IP address for push notifications.
C. On FG-1 CLI, the ftm-push server setting must point to 100.64.141.
D. On FAC-1, the FortiToken public IP setting must point to 100.64.1 41 -
Question 4:
Refer to the exhibit showing a FortiView monitor screen.
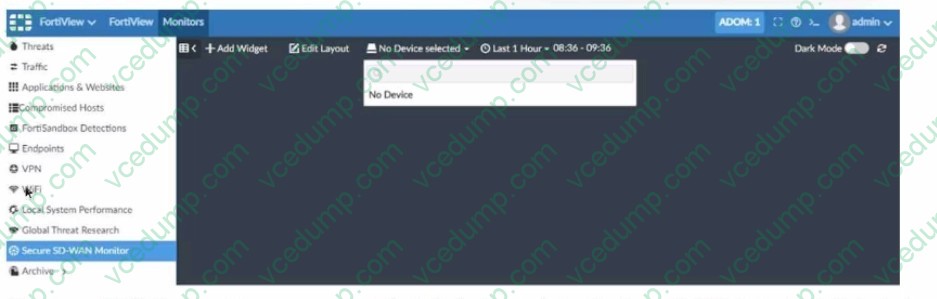
After a Secure SD-WAN implementation a customer reports that in FortiAnalyzer under FortiView Secure SD-WAN Monitor there is No Device for selection. What can cause this issue?
A. Upload option from FortiGate to FortiAnalyzer is not set as a real time.
B. Extended logging is not enabled on FortiGate.
C. ADOM 1 is set as a Fabric ADOM.
D. sla-fail-log-period and sla-pass-log-period on FortiGate health check is not set. -
Question 5:
Refer to the exhibit.
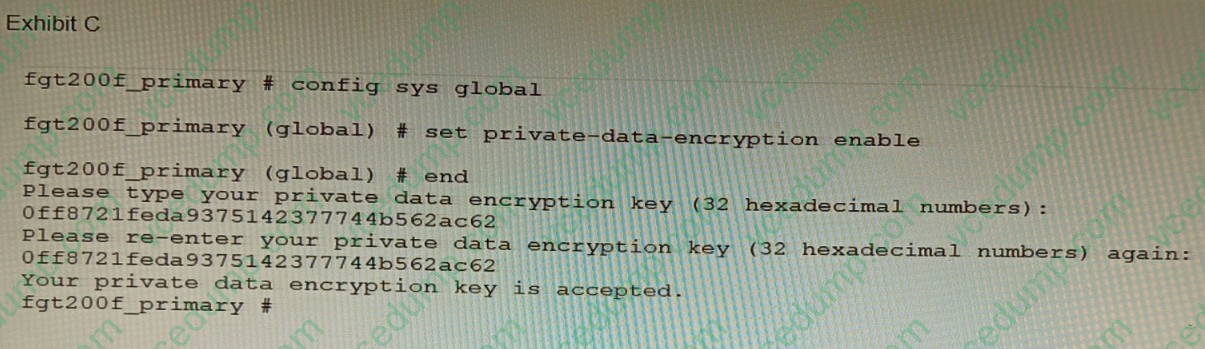
A customer has deployed a FortiGate 200F high-availability (HA) cluster that contains and TPM chip. The exhibit shows output from the FortiGate CLI session where the administrator enabled TPM.
Following these actions, the administrator immediately notices that both FortiGate high availability (HA) status and FortiManager status for the FortiGate are negatively impacted.
What are the two reasons for this behavior? (Choose two.)
A. The private-data-encryption key entered on the primary did not match the value that the TPM expected.
B. Configuration for TPM is not synchronized between FortiGate HA cluster members.
C. The FortiGate has not finished the auto-update process to synchronize the new configuration to FortiManager yet.
D. TPM functionality is not yet compatible with FortiGate HA.
E. The administrator needs to manually enter the hex private data encryption key in FortiManager. -
Question 6:
Refer to the exhibits.
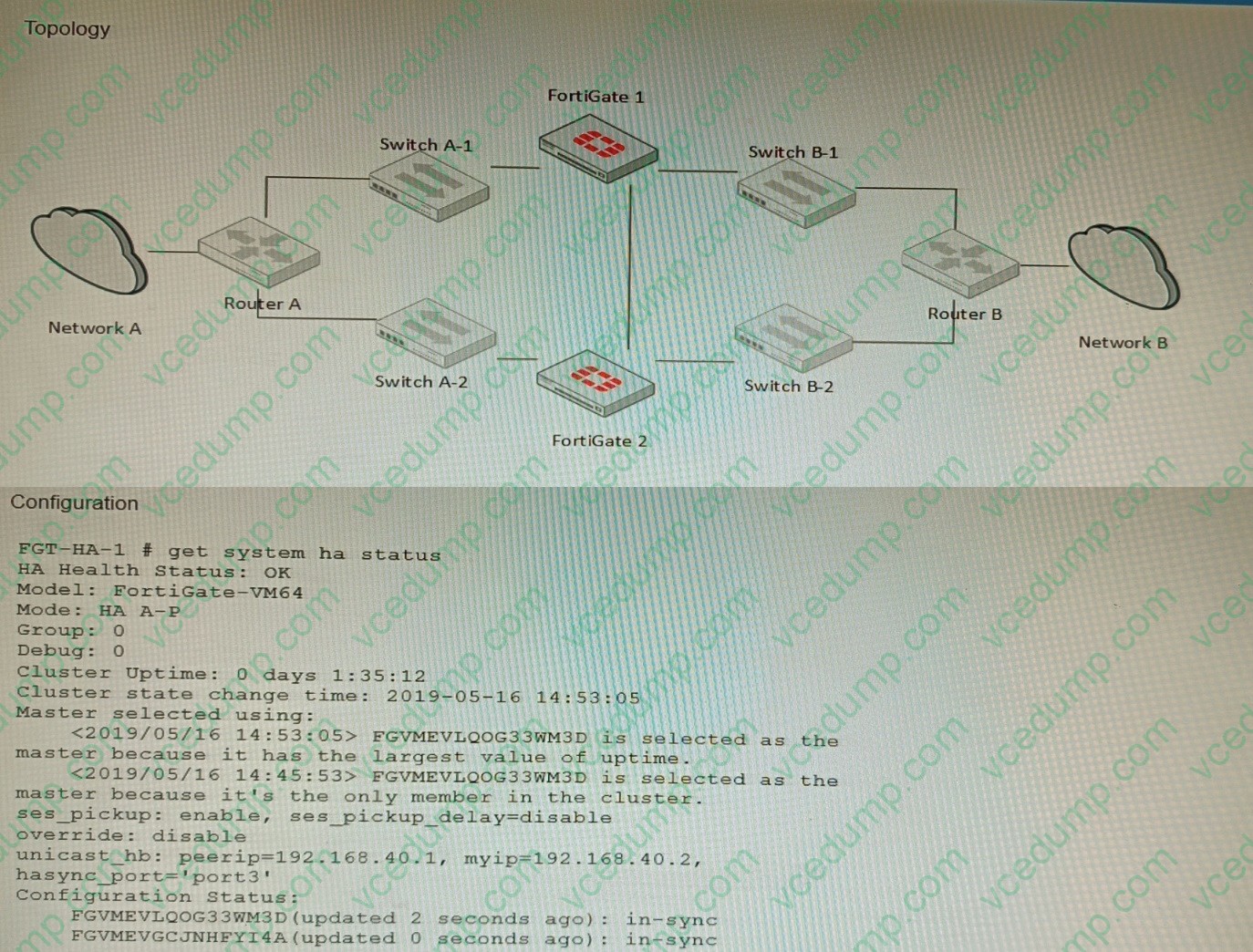
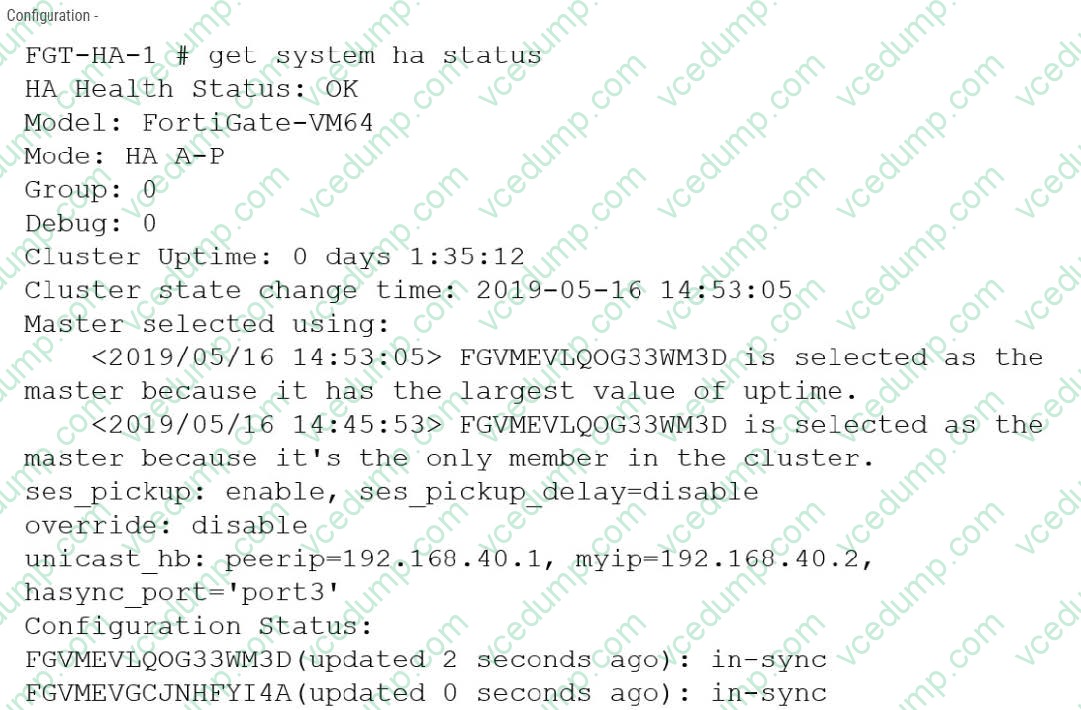
The exhibits show a FortiGate network topology and the output of the status of high availability on the FortiGate. Given this information, which statement is correct?
A. The ethertype values of the HA packets are 0x8890, 0x8891, and 0x8892
B. The cluster mode can support a maximum of four (4) FortiGate VMs
C. The cluster members are on the same network and the IP addresses were statically assigned.
D. FGVMEVLQOG33WM3D and FGVMEVGCJNHFYI4A share a virtual MAC address. -
Question 7:
Refer to the exhibit.
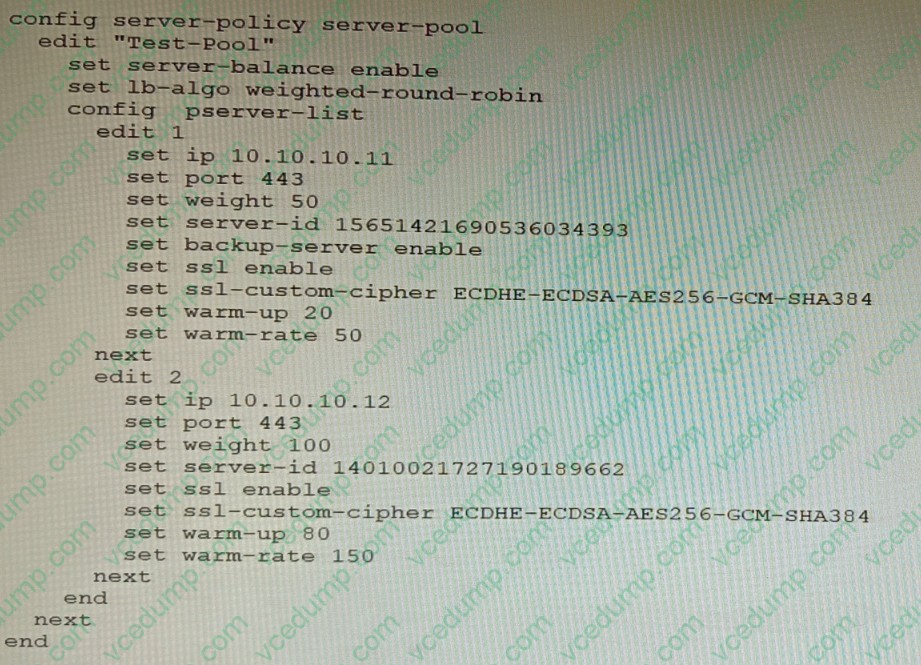
A FortiWeb appliance is configured for load balancing web sessions to internal web servers. The Server Pool is configured as shown in the exhibit. How will the sessions be load balanced between server 1 and server 2 during normal operation?
A. Server 1 will receive 25% of the sessions, Server 2 will receive 75% of the sessions
B. Server 1 will receive 20% of the sessions, Server 2 will receive 66.6% of the sessions
C. Server 1 will receive 33.3% of the sessions, Server 2 will receive 66 6% of the sessions
D. Server 1 will receive 0% of the sessions Server 2 will receive 100% of the sessions -
Question 8:
Refer to the exhibit.
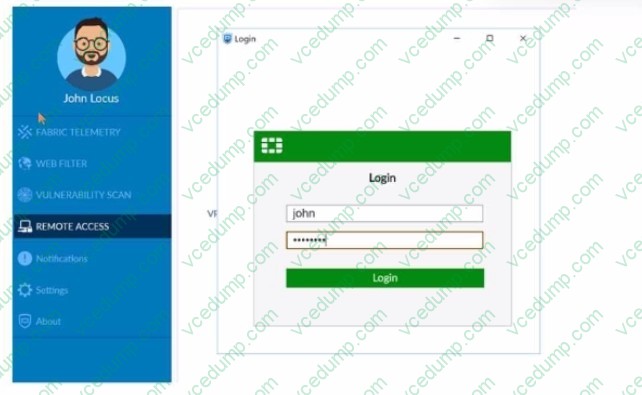
What is happening in this scenario?
A. The user status changed at FortiClient EMS to off-net.
B. The user is authenticating against a FortiGate Captive Portal.
C. The user is authenticating against an IdP.
D. The user has not authenticated on their external browser. -
Question 9:
Refer to the exhibits.
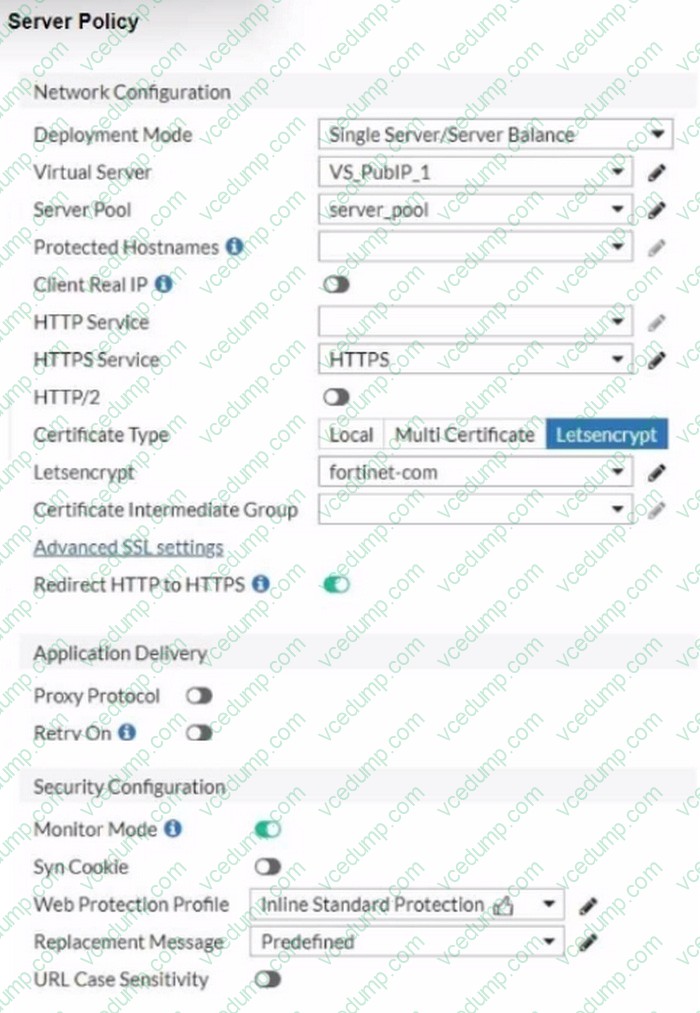
You are configuring a Let's Encrypt certificate to enable SSL protection to your website. When FortiWeb tries to retrieve the certificate, you receive a certificate status failed, as shown below.

Based on the Server Policy settings shown in the exhibit, which two configuration changes will resolve this issue? (Choose two.)
A. Disable Redirect HTTP to HTTPS in the Server Policy.
B. Remove the Web Protection Profile from this Server Policy.
C. Enable HTTP service in the Server Policy.
D. Configure a TXT record of the domain and point to the IP address of the Virtual Server. -
Question 10:
A customer wants to use the FortiAuthenticator REST API to retrieve an SSO group called SalesGroup. The following API call is being made with the 'curl' utility:

Which two statements correctly describe the expected behavior of the FortiAuthenticator REST API? (Choose two.)
A. Only users with the "Full permission" role can access the REST API
B. This API call will fail because it requires that API version 2
C. If the REST API web service access key is lost, it cannot be retrieved and must be changed.
D. The syntax is incorrect because the API calls needs the get method.
Related Exams:
-
EMEA-ADVANCED-SUPPORT
Fortinet EMEA Advanced Support -
FCP_FAC_AD-6.5
FCP - FortiAuthenticator 6.5 Administrator -
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 Administrator -
FCP_FAZ_AN-7.4
FCP - FortiAnalyzer 7.4 Analyst -
FCP_FCT_AD-7.2
FCP - Forti Client EMS 7.2 Administrator -
FCP_FGT_AD-7.4
FCP - FortiGate 7.4 Administrator -
FCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6 -
FCP_FMG_AD-7.4
FCP - FortiManager 7.4 Administrator -
FCP_FMG_AD-7.6
FortiManager 7.6 Administrator -
FCP_FML_AD-7.4
FCP - FortiMail 7.4 Administrator
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE8_812 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.