Exam Details
Exam Code
:NSE7_EFW-7.2Exam Name
:Fortinet NSE 7 - Enterprise Firewall 7.2Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:80 Q&AsLast Updated
:Aug 06, 2025
Fortinet Fortinet Certifications NSE7_EFW-7.2 Questions & Answers
-
Question 41:
In which two ways does fortiManager function when it is deployed as a local FDS? (Choose two)
A. lt can be configured as an update server a rating server or both
B. It provides VM license validation services
C. It supports rating requests from non-FortiGate devices.
D. It caches available firmware updates for unmanaged devices
-
Question 42:
Refer to the exhibit, which shows an ADVPN network.

Which VPN phase 1 parameters must you configure on the hub for the ADVPN feature to function? (Choose two.)
A. set auto-discovery-forwarder enable
B. set add-route enable
C. set auto-discovery-receiver enable
D. set auto-discovery-sender enable
-
Question 43:
Exhibit.

Refer to the exhibit, which contains a CLI script configuration on fortiManager. An administrator configured the CLI script on FortiManager rut the script tailed to apply any changes to the managed
device after being executed.
What are two reasons why the script did not make any changes to the managed device? (Choose two)
A. The commands that start with the # sign did not run.
B. Incomplete commands can cause CLI scripts to fail.
C. Static routes can be added using only TCI scripts.
D. CLI scripts must start with #!.
-
Question 44:
Refer to the exhibit, which contains a partial OSPF configuration.
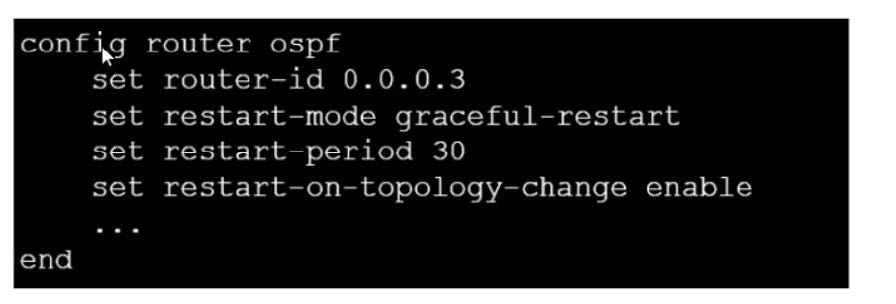
What can you conclude from this output?
A. Neighbors maintain communication with the restarting router.
B. The router sends grace LSAs before it restarts.
C. FortiGate restarts if the topology changes.
D. The restarting router sends gratuitous ARP for 30 seconds.
-
Question 45:
You contoured an address object on the tool fortiGate in a Security Fabric. This object is not synchronized with a downstream device. Which two reasons could be the cause? (Choose two)
A. The address object on the tool FortiGate has fabric-object set to disable
B. The root FortiGate has configuration-sync set to enable
C. The downstream TortiGate has fabric-object-unification set to local
D. The downstream FortiGate has configuration-sync set to local
-
Question 46:
You want to improve reliability over a lossy IPSec tunnel.
Which combination of IPSec phase 1 parameters should you configure?
A. fec-ingress and fec-egress
B. Odpd and dpd-retryinterval
C. fragmentation and fragmentation-mtu
D. keepalive and keylive
-
Question 47:
Exhibit.
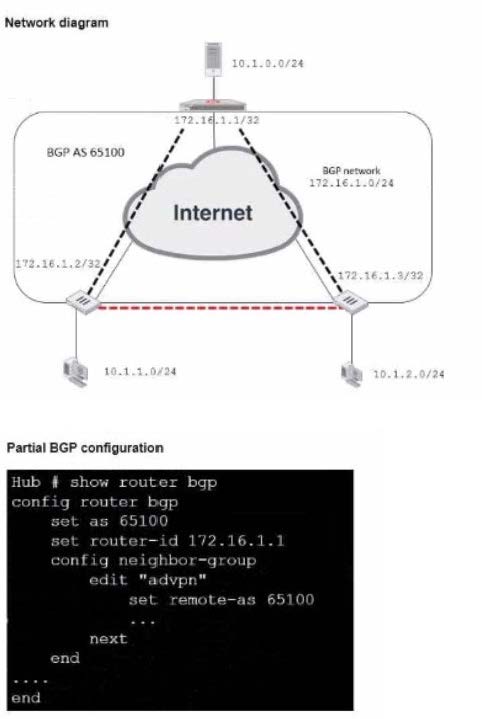
Refer to the exhibit, which contains an ADVPN network diagram and a partial BGP con figuration Which two parameters Should you configure in config neighbor range? (Choose two.)
A. set prefix 172.16.1.0 255.255.255.0
B. set route reflector-client enable
C. set neighbor-group advpn
D. set prefix 10.1.0 255.255.255.0
-
Question 48:
An administrator has configured two fortiGate devices for an HA cluster. While testing HA failover, the administrator notices that some of the switches in the network continue to send traffic to the former primary device What can the administrator do to fix this problem?
A. Verify that the speed and duplex settings match between me FortiGate interfaces and the connected switch ports
B. Configure set link -failed signal enable under-config system ha on both Cluster members
C. Configure remote Iink monitoring to detect an issue in the forwarding path
D. Configure set send-garp-on-failover enables under config system ha on both cluster members
-
Question 49:
Exhibit.
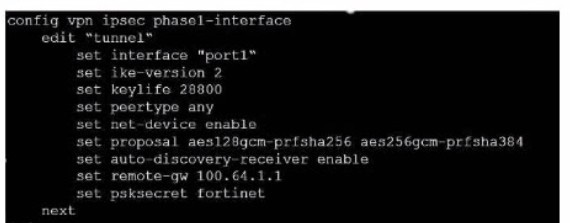
Refer to the exhibit, which contains the partial ADVPN configuration of a spoke.
Which two parameters must you configure on the corresponding single hub? (Choose two.)
A. Set auto-discovery-sender enable
B. Set ike-version 2
C. Set auto-discovery-forwarder enable
D. Set auto-discovery-receiver enable
-
Question 50:
Exhibit.
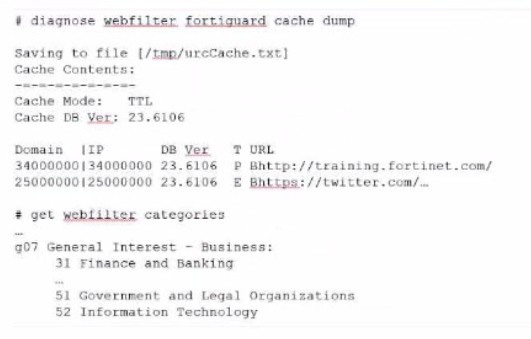
Refer to the exhibit, which shows the output from the webfilter fortiguard cache dump and webfilter categories commands.
Using the output, how can an administrator determine the category of the training.fortinet.comam website?
A. The administrator must convert the first three digits of the IP hex value to binary
B. The administrator can look up the hex value of 34 in the second command output.
C. The administrator must add both the Pima in and Iphex values of 34 to get the category number
D. The administrator must convert the first two digits of the Domain hex value to a decimal value
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE7_EFW-7.2 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.