NSE7_EFW-7.2 Exam Details
-
Exam Code
:NSE7_EFW-7.2 -
Exam Name
:Fortinet NSE 7 - Enterprise Firewall 7.2 -
Certification
:Fortinet Certifications -
Vendor
:Fortinet -
Total Questions
:80 Q&As -
Last Updated
:Jan 12, 2026
Fortinet NSE7_EFW-7.2 Online Questions & Answers
-
Question 1:
Exhibit.
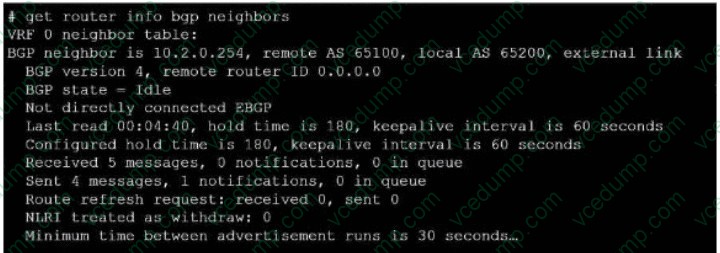
Refer to the exhibit, which provides information on BGP neighbors. Which can you conclude from this command output?
A. The router are in the number to match the remote peer.
B. You must change the AS number to match the remote peer.
C. BGP is attempting to establish a TCP connection with the BGP peer.
D. The bfd configuration to set to enable. -
Question 2:
Which two statements about IKE vision 2 are true? (Choose two.)
A. Phase 1 includes main mode
B. It supports the extensible authentication protocol (EAP)
C. It supports the XAuth protocol.
D. It exchanges a minimum of four messages to establish a secure tunnel -
Question 3:
An administrator has configured two fortiGate devices for an HA cluster. While testing HA failover, the administrator notices that some of the switches in the network continue to send traffic to the former primary device What can the administrator do to fix this problem?
A. Verify that the speed and duplex settings match between me FortiGate interfaces and the connected switch ports
B. Configure set link -failed signal enable under-config system ha on both Cluster members
C. Configure remote Iink monitoring to detect an issue in the forwarding path
D. Configure set send-garp-on-failover enables under config system ha on both cluster members -
Question 4:
Refer to the exhibit, which shows a routing table.
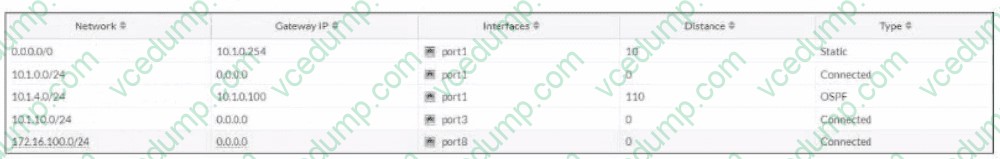
What two options can you configure in OSPF to block the advertisement of the 10.1.10.0 prefix? (Choose two.)
A. Remove the 16.1.10.C prefix from the OSPF network
B. Configure a distribute-list-out
C. Configure a route-map out
D. Disable Redistribute Connected -
Question 5:
In which two ways does fortiManager function when it is deployed as a local FDS? (Choose two)
A. lt can be configured as an update server a rating server or both
B. It provides VM license validation services
C. It supports rating requests from non-FortiGate devices.
D. It caches available firmware updates for unmanaged devices -
Question 6:
Exhibit.
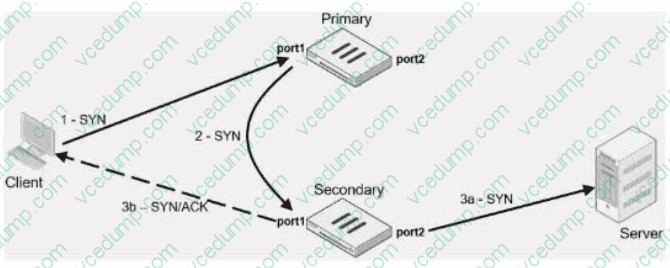
Refer to the exhibit, which contains an active-active toad balancing scenario.
During the traffic flow the primary FortiGate forwards the SYN packet to the secondary FortiGate.
What is the destination MAC address or addresses when packets are forwarded from the primary FortiGate to the secondary FortiGate?
A. Secondary physical MAC port1
B. Secondary virtual MAC port1
C. Secondary virtual MAC port1 then physical MAC port1
D. Secondary physical MAC port2 then virtual MAC port2 -
Question 7:
Which statement about ADVPN is true?
A. lt only uses BGP for dynamic routing
B. It requires all the devices must be on the same AS for inter-region ADVPN topology
C. lt is a combination of hub-and spoke and full-mesh topologies
D. It supports only on single hub-and spoke architecture -
Question 8:
Which two statements about the neighbor-group command are true? (Choose two.)
A. You can configure it on the GUI.
B. It applies common settings in an OSPF area.
C. It is combined with the neighbor-range parameter.
D. You can apply it in Internal BGP (IBGP) and External BGP (EBGP). -
Question 9:
Refer to the exhibit, which contains a TCL script configuration on FortiManager.
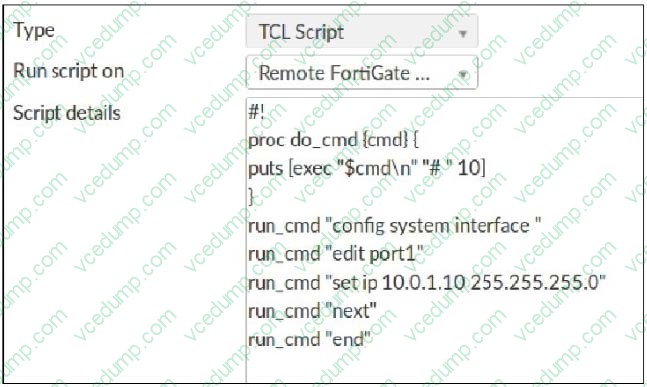
An administrator has configured the TCL script on FortiManager, but the TCL script failed to apply any changes to the managed device after being run. Why did the TCL script fail to make any changes to the managed device?
A. The TCL procedure run_cmd has not been created.
B. The TCL script must start with #include.
C. There is no corresponding #! to signify the end of the script.
D. The TCL procedure lacks the required loop statements to iterate through the changes. -
Question 10:
Refer to the exhibit, which contains a partial configuration of the global system.

What can you conclude from the output?
A. set strict-d^rty-session-check enable command instructs the FortiGate to offload all dirty session traffic to its SPU
B. set check-protocol-header loose command enables hardware acceleration on this FortiGate device.
C. set av-failopen pass command instructs the FortiGate to offload all traffic that uses the antivirus proxy to NP.
D. set memory-use-threshoId-extreme command instructs the FortiGate to disable hardware acceleration if the memory extreme threshold reaches 95%
Related Exams:
-
EMEA-ADVANCED-SUPPORT
Fortinet EMEA Advanced Support -
FCP_FAC_AD-6.5
FCP - FortiAuthenticator 6.5 Administrator -
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 Administrator -
FCP_FAZ_AN-7.4
FCP - FortiAnalyzer 7.4 Analyst -
FCP_FCT_AD-7.2
FCP - Forti Client EMS 7.2 Administrator -
FCP_FGT_AD-7.4
FCP - FortiGate 7.4 Administrator -
FCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6 -
FCP_FMG_AD-7.4
FCP - FortiManager 7.4 Administrator -
FCP_FMG_AD-7.6
FortiManager 7.6 Administrator -
FCP_FML_AD-7.4
FCP - FortiMail 7.4 Administrator
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE7_EFW-7.2 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.