Exam Details
Exam Code
:NSE7_EFW-7.2Exam Name
:Fortinet NSE 7 - Enterprise Firewall 7.2Certification
:Fortinet CertificationsVendor
:FortinetTotal Questions
:80 Q&AsLast Updated
:Aug 06, 2025
Fortinet Fortinet Certifications NSE7_EFW-7.2 Questions & Answers
-
Question 11:
Exhibit.
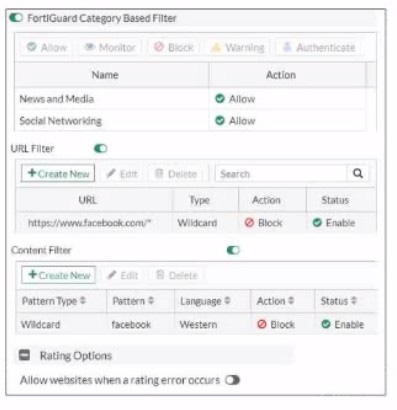
Refer to the exhibit, which shows a partial web filter profile conjuration
What can you cone udo from this configuration about access towww.facebook, com, which is categorized as Social Networking?
A. The access is blocked based on the Content Filter configuration
B. The access is allowed based on the FortiGuard Category Based Filter configuration
C. The access is blocked based on the URL Filter configuration
D. The access is hocked if the local or the public FortiGuard server does not reply
-
Question 12:
Exhibit.
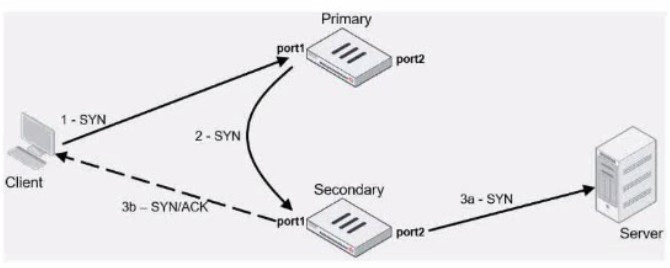
Refer to the exhibit, which contains an active-active toad balancing scenario.
During the traffic flow the primary FortiGate forwards the SYN packet to the secondary FortiGate.
What is the destination MAC address or addresses when packets are forwarded from the primary FortiGate to the secondary FortiGate?
A. Secondary physical MAC port1
B. Secondary virtual MAC port1
C. Secondary virtual MAC port1 then physical MAC port1
D. Secondary physical MAC port2 then virtual MAC port2
-
Question 13:
Exhibit.
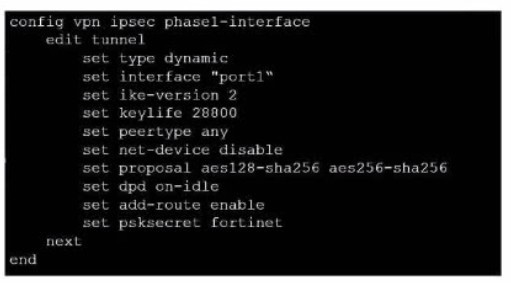
Refer to the exhibit, which contains a partial VPN configuration. What can you conclude from this configuration1?
A. FortiGate creates separate virtual interfaces for each dial up client.
B. The VPN should use the dynamic routing protocol to exchange routing information Through the tunnels.
C. Dead peer detection s disabled.
D. The routing table shows a single IPSec virtual interface.
-
Question 14:
Refer to the exhibit, which shows an error in system fortiguard configuration.
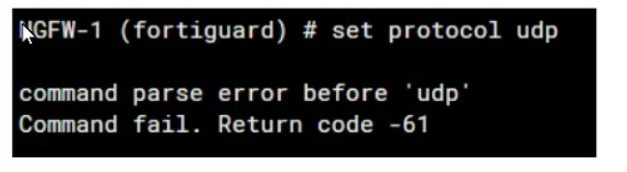
What is the reason you cannot set the protocol to udp in config system fortiguard?
A. FortiManager provides FortiGuard.
B. fortiguard-anycast is set to enable.
C. You do not have the corresponding write access.
D. udp is not a protocol option.
-
Question 15:
Exhibit.
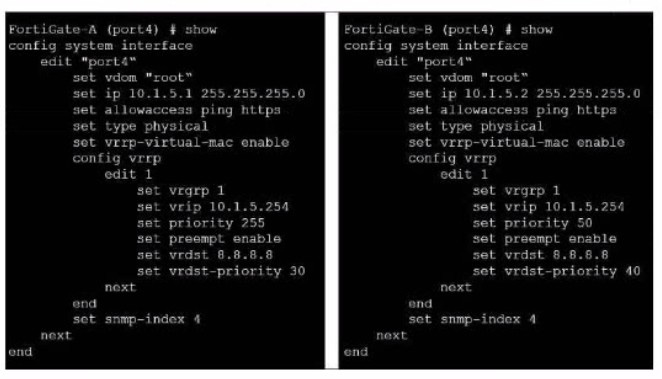
Refer to the exhibit, which contains the partial interface configuration of two FortiGate devices.
Which two conclusions can you draw from this con figuration? (Choose two)
A. 10.1.5.254 is the default gateway of the internal network
B. On failover new primary device uses the same MAC address as the old primary
C. The VRRP domain uses the physical MAC address of the primary FortiGate
D. By default FortiGate B is the primary virtual router
-
Question 16:
Which two statements about the BFD parameter in BGP are true? (Choose two.)
A. It allows failure detection in less than one second.
B. The two routers must be connected to the same subnet.
C. It is supported for neighbors over multiple hops.
D. It detects only two-way failures.
-
Question 17:
Exhibit.
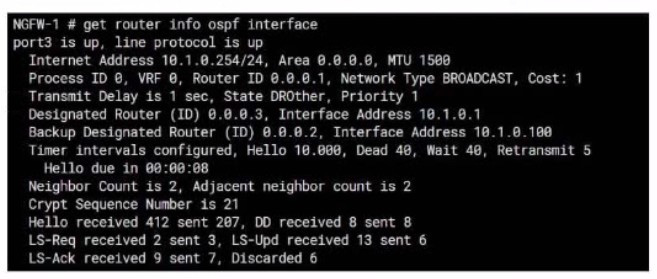
Refer to the exhibit, which shows information about an OSPF interlace
What two conclusions can you draw from this command output? (Choose two.)
A. The port3 network has more man one OSPF router
B. The OSPF routers are in the area ID of 0.0.0.1.
C. The interfaces of the OSPF routers match the MTU value that is configured as 1500.
D. NGFW-1 is the designated router
-
Question 18:
Refer to the exhibits, which show the configurations of two address objects from the same FortiGate.
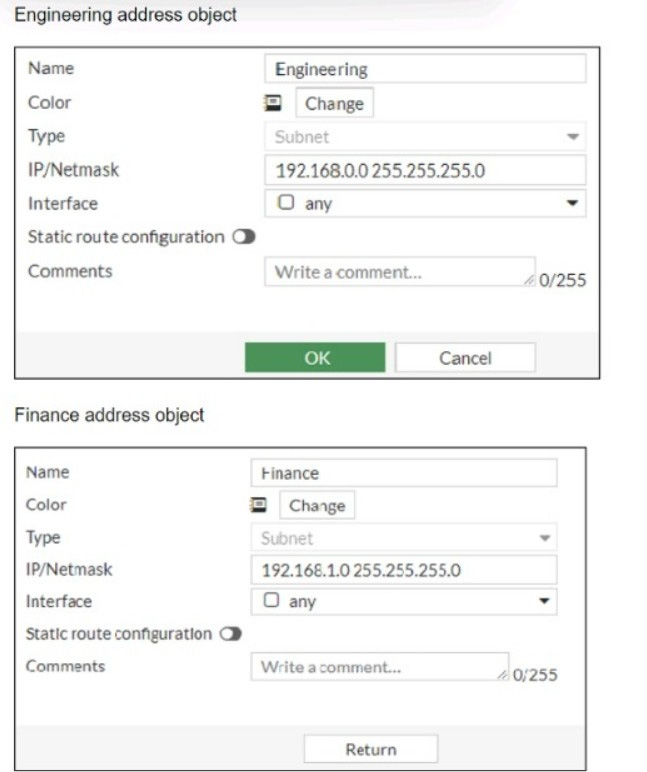
Why can you modify the Engineering address object, but not the Finance address object?
A. You have read-only access.
B. FortiGate joined the Security Fabric and the Finance address object was configured on the root FortiGate.
C. FortiGate is registered on FortiManager.
D. Another user is editing the Finance address object in workspace mode.
-
Question 19:
Exhibit.
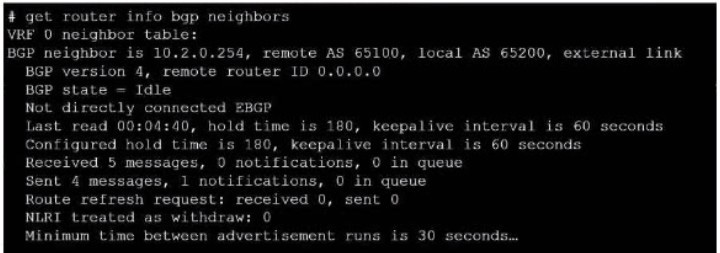
Refer to the exhibit, which provides information on BGP neighbors. Which can you conclude from this command output?
A. The router are in the number to match the remote peer.
B. You must change the AS number to match the remote peer.
C. BGP is attempting to establish a TCP connection with the BGP peer.
D. The bfd configuration to set to enable.
-
Question 20:
Which two statements about IKE version 2 fragmentation are true? (Choose two.)
A. Only some IKE version 2 packets are considered fragmentable.
B. The reassembly timeout default value is 30 seconds.
C. It is performed at the IP layer.
D. The maximum number of IKE version 2 fragments is 128.
Related Exams:
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 AdministratorFCP_FGT_AD-7.4
FCP - FortiGate 7.4 AdministratorFCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6FCP_WCS_AD-7.4
FCP - AWS Cloud Security 7.4 AdministratorFCSS_EFW_AD-7.4
FCSS - Enterprise Firewall 7.4 AdministratorFCSS_NST_SE-7.4
FCSS - Network Security 7.4 Support EngineerFCSS_SASE_AD-24
FCSS - FortiSASE 24 AdministratorNSE4_FGT-5.6
Fortinet NSE 4 - FortiOS 5.6NSE4_FGT-6.0
Fortinet NSE 4 - FortiOS 6.0NSE4_FGT-6.4
Fortinet NSE 4 - FortiOS 6.4
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE7_EFW-7.2 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.