NSE6_FML-7.2 Exam Details
-
Exam Code
:NSE6_FML-7.2 -
Exam Name
:Fortinet NSE 6 - FortiMail 7.2 -
Certification
:Fortinet Certifications -
Vendor
:Fortinet -
Total Questions
:31 Q&As -
Last Updated
:Jan 12, 2026
Fortinet NSE6_FML-7.2 Online Questions & Answers
-
Question 1:
In which FortiMail configuration object can you assign an outbound session profile?
A. Outbound recipient policy
B. Inbound recipient policy
C. IP policy
D. Access delivery rule -
Question 2:
Refer to the exhibits which show a topology diagram (Topology) and a configuration element (Access Control Rule).
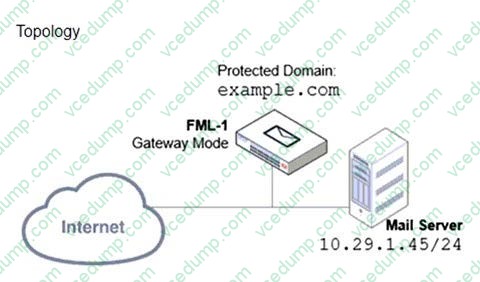
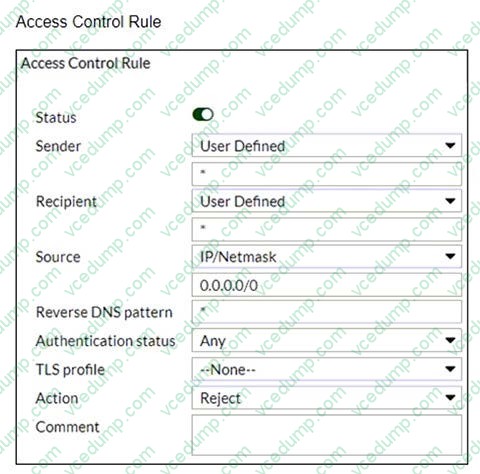
Which three access control settings are recommended to allow outbound email from the example.com domain on FML-1? (Choose three.)
A. The Sender IP/netmask should be set to 10.29.1.45/32.
B. The Recipient pattern should be set to 10.29.1.45/24
C. The Action should be set to Relay.
D. The Sender pattern should be set to *@example.com.
E. The Enable check box should be cleared. -
Question 3:
Refer to the exhibits which show a topology diagram (Topology), and a configuration element (Access Control Rule).
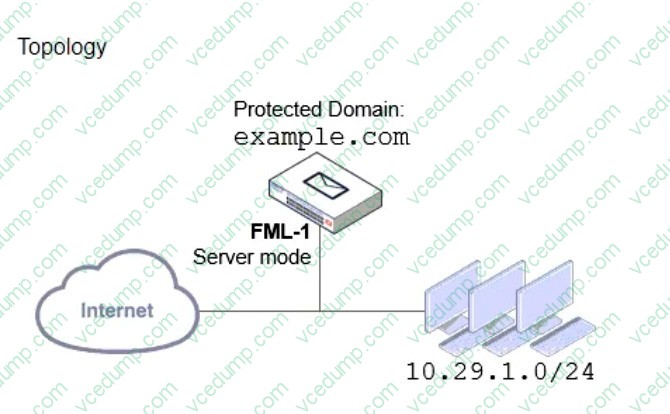
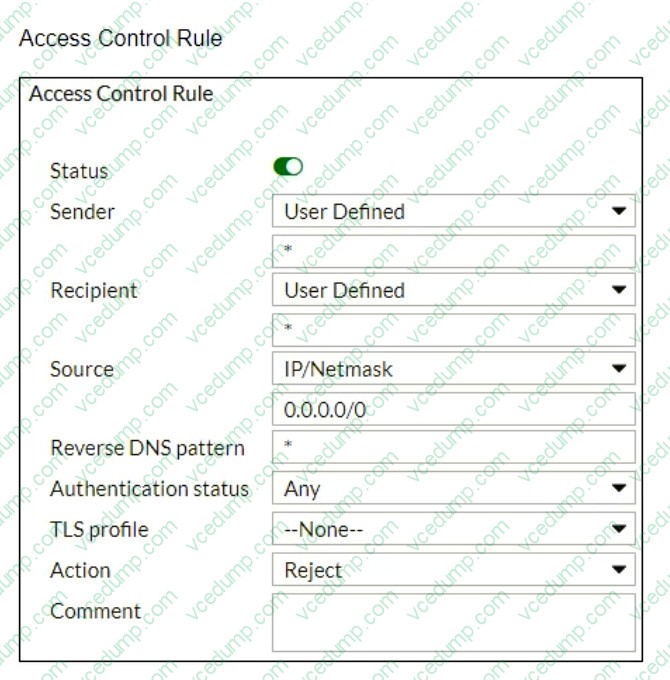
An administrator must enforce authentication on FML-1 for all outbound email from the example.com domain. Which two settings should be used to configure the access receive rule? (Choose two.)
A. The Sender IP/netmask should be set to 10.29.1.0/24.
B. The Action should be set to Reject
C. The Recipient pattern should be set to ?@example. com.
D. The Authentication status should be set to Authenticated -
Question 4:
In which two places can the maximum email size be overridden on FortiMail? (Choose two.)
A. IP Policy configuration
B. Protected Domain configuration
C. Resource Profile configuration
D. Session Profile configuration -
Question 5:
A FortiMail administrator is investigating a sudden increase in DSNs being delivered to their protected domain. After searching the logs, the administrator identifies that the DSNs were not generated because of any outbound email sent from their organization. Which FortiMail antispam technique can the administrator use to prevent this scenario?
A. FortiGuard IP Reputation
B. Spoofed header detection
C. Spam outbreak protection
D. Bounce address tag validation -
Question 6:
Refer to the exhibit which displays a list of IBE users on a FortiMail device.
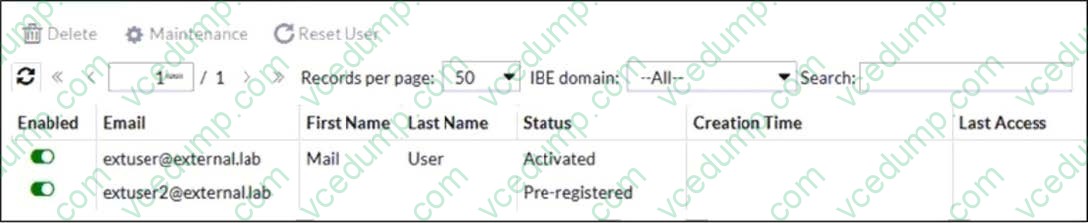
Which statement describes the pre-registered status of the IBE user extuser2@external.lab?
A. The user has received an IBE notification email, but has not accessed the HTTPS URL or attachment yet.
B. The user was registered by an administrator in anticipation of IBE participation.
C. The user account has been de-activated, and the user must register again the next time they receive an IBE email.
D. The user has completed the IBE registration process, but has not yet accessed their IBE email. -
Question 7:
Refer to the exhibit which shows an nslookup output of MX records of the example.com domain.
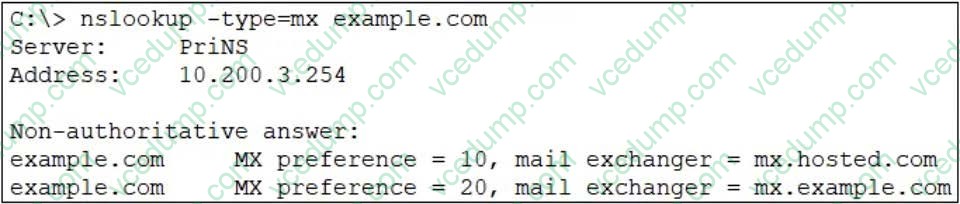
Which two MTA selection behaviors for the example.com domain are correct? (Choose two.)
A. mx.example.com will receive approximately twice the number of email as mx.hosted.com because of its preference value.
B. The primary MTA for the example.com domain is mx.hosted.com.
C. The external MTAs will send email to mx.example.com only if mx.hosted.com is unreachable.
D. The PriNS server should receive all email for the example.com domain. -
Question 8:
While reviewing logs, an administrator discovers that an incoming email was processed using policy IDs 0:4:9:INTERNAL. Which two statements describe what this policy ID means? (Choose two.)
A. Access control policy number 9 was used.
B. The FortiMail configuration is missing an access delivery rule.
C. The email was processed using IP-based policy ID 4.
D. FortiMail is applying the default behavior for relaying inbound email. -
Question 9:
What are two disadvantages of configuring the dictionary and DLP scan rule aggressiveness too high? (Choose two.)
A. High aggressiveness scan settings do not support executable file types.
B. It is more resource intensive
C. More false positives could be detected.
D. FortiMail requires more disk space for the additional rules. -
Question 10:
A FortiMail is configured with the protected domain example.com.
On this FortiMail, which two envelope addresses are considered incoming? (Choose two.)
A. MAIL FROM: mis@hosted.net RCPT TO: noc@example.com
B. MAIL FROM: accounts@example.com RCPT TO: sales@external.org
C. MAIL FROM: support@example.com RCPT TO: marketing@example.com
D. MAIL FROM: training@external.org RCPT TO: students@external.org
Related Exams:
-
EMEA-ADVANCED-SUPPORT
Fortinet EMEA Advanced Support -
FCP_FAC_AD-6.5
FCP - FortiAuthenticator 6.5 Administrator -
FCP_FAZ_AD-7.4
FCP - FortiAnalyzer 7.4 Administrator -
FCP_FAZ_AN-7.4
FCP - FortiAnalyzer 7.4 Analyst -
FCP_FCT_AD-7.2
FCP - Forti Client EMS 7.2 Administrator -
FCP_FGT_AD-7.4
FCP - FortiGate 7.4 Administrator -
FCP_FGT_AD-7.6
FortiGate 7.6 Administrator FCP_FGT_AD-7.6 -
FCP_FMG_AD-7.4
FCP - FortiManager 7.4 Administrator -
FCP_FMG_AD-7.6
FortiManager 7.6 Administrator -
FCP_FML_AD-7.4
FCP - FortiMail 7.4 Administrator
Tips on How to Prepare for the Exams
Nowadays, the certification exams become more and more important and required by more and more enterprises when applying for a job. But how to prepare for the exam effectively? How to prepare for the exam in a short time with less efforts? How to get a ideal result and how to find the most reliable resources? Here on Vcedump.com, you will find all the answers. Vcedump.com provide not only Fortinet exam questions, answers and explanations but also complete assistance on your exam preparation and certification application. If you are confused on your NSE6_FML-7.2 exam preparations and Fortinet certification application, do not hesitate to visit our Vcedump.com to find your solutions here.